What is CUI Specified?
Entities with a close working relationship with the U.S. Government must institute proper safeguards to protect data that the Government deems sensitive. One such type of information is the Controlled Unclassified Information (CUI). CUI plays a vital role in protecting sensitive data that doesn’t warrant classification but requires safeguarding. The CUI framework has two categories: CUI Basic and CUI Specified. In this article, we will focus on CUI Specified, exploring its definition, distinction from CUI Basic, and its significance in ensuring the security of sensitive information. So, what is CUI Specified? How can you effectively secure it?
Defining CUI Specified
CUI Specified represents a subset of CUI that has specific handling requirements mandated by law, regulation, or government-wide policy (LRGWP). This information requires more stringent safeguarding measures compared to CUI Basic. This is owing to its sensitive nature and the potential harm that could arise from unauthorized disclosure. Each subcategory or category of CUI Specified has different requirements for treating information, unlike CUI Basic. This is because some Authorities have VERY particular requirements on handling each type of information about them. Such requirements might not make sense for the rest of CUI.
However, it is worth noting that CUI Specified is NOT a “higher Level” of CUI; it’s simply different. Since laws, Federal regulations, and government-wide policies define things making it different, you cannot legally overlook or ignore them. This is where marking plays a critical role. Documents with multiple CUI Specified Categories and Subcategories should include ALL in the Banner Marking. However, CUI Specified has one additional issue: some Categories and subcategories are not always CUI Specified, only sometimes.
Examples of CUI Specified
CUI Specified can include information such as:
- Export-controlled data: Information subject to export control regulations, such as the International Traffic in Arms Regulations (ITAR) or Export Administration Regulations (EAR).
- Critical infrastructure information: Data that reveals vulnerabilities or weaknesses in critical infrastructure systems, such as energy, transportation, or communications.
- Privacy Act information: Personal data protected under the Privacy Act of 1974, including Social Security numbers, medical records, or financial data.
CUI Specified vs. CUI Basic
The primary distinction between CUI Specified and CUI Basic lies in the handling requirements and the level of protection needed for each category.
Handling requirements
CUI Specified has specific LRGWP handling requirements. On the other hand, CUI Basic does not have such specified requirements and follows a standard set of safeguarding measures.
Level of protection
CUI Specified typically requires more stringent security measures due to the sensitive nature of the information and the potential consequences of unauthorized disclosure.
What DoD Instruction Implements the DoD CUI Program?
DODI 5200.48 implements the DoD CUI program and establishes the official DOD CUI Registry. This instruction assigns responsibilities, sets policy, and prescribes procedures for designation, handling, and decontrolling CUI in DoD systems. CUI Specified handling includes identification, sharing, marking, safeguarding, storage, dissemination, destruction, and records management. DODI 5200.48 also assigns eight responsibilities relating to CUI to DCSA.
What are the Handling Requirements for CUI Specified?
Control Requirements
For any information designated CUI Specified, the authorized holder should follow all the CUI registry’s dissemination and safeguarding procedures prescribed by the underlying authorities. If the LRGWP governing a particular type of CUI Specified are silent on either disseminating or safeguarding control, 32 CFR 2002.14(b)(2)(ii) requires agencies to apply the CUI Basic standards. However, this is only applicable to the extent that it results in a treatment that is in accordance with the CUI Specified authority. Otherwise, if applying CUI Basic conflicts with the CUI Specified authority, agencies should use the CUI Specified standards or may use the Limited Dissemination Controls (LDCs) listed in the ISOO CUI Registry to ensure the information is treated in accordance with the CUI Specified authority.
CUI Specified Marking
CUI Specified has additional marking requirements beyond CUI Basic. For instance, although the CUI banner marking is a requirement for all CUI, only CUI specified requires that the CUI category or subcategory markings be included. This is MANDATORY under 32 CFR 2002.20(b)(2)(iii), which states, “…authorized holders must include in the CUI banner marking all CUI Specified Category or Subcategory markings that pertain to the information in the document.”
What is The Purpose of the ISOO CUI Registry?
There are 2 CUI registries: the NARA ISOO CUI registry and the DoD CUI Registry, otherwise called the “DoD Registry.” But first, what does ISOO stand for? ISOO stands for the “Information Security Oversight Office.” Then, what is ISOO? The ISOO is an office within the National Archives and Records Administration (NARA). It acts as the Executive Agent responsible for oversight of the CUI Program, monitoring its implementation by executive branch agencies. Having understood what ISOO stands for and means, what is ISOO registry? It is a government-wide government repository for CUI policy guidance and practice at the federal level. It shows the authorized CUI specified and basic categories and associated markings, including applicable safeguarding, dissemination, and decontrol procedures.
ISOO continues to update the CUI registry as agencies submit the governing authorities that authorize safeguarding and protecting sensitive information. It is worth noting that the ISOO CUI registry is available to all federal, civilian, military, and contractor employees. The NARA ISOO CUI registry:
- Identifies “all approved CUI categories and subcategories;
- Provides general descriptions for each;
- Identifies the basis for controls;
- Establishes markings, and
- Issues guidance on handling procedures.
CUI Specified Marking Requirements
Below are other CUI Specified Marking requirements in accordance with the ISOO CUI Registry:
- Because CUI Specified Categories and Subcategories differ among each other and the CUI Basic, then users MUST always include CUI Specified in the CUI Banner. This ensures that the authorized holder and the end user receiving a document containing CUI Specified knows that such a document should be treated differently from CUI Basic. This can be achieved through:
- Ensuring that ALL CUI Specified Documents include Category and Subcategory markings for all CUI Specified within such documents in the Banner marking. Doing this ensures that the first thing a user receiving the document sees is the CUI Banner that lets them understand they are holding CUI Specified and have to meet the alternative or additional requirements.
- To ensure that it’s obvious that a Subcategory or Category is Specified, the marking features “SP-” at the beginning of it.
- The CUI Specified marking should always precede those of CUI Basic in the CUI Banner.
- The CUI Subcategory and Category Markings SHOULD be alphabetized within the CUI type. However, the alphabetized Specified CUI Subcategories and Categories should precede the alphabetized Basic CUI Categories or Subcategories.
CUI Specified Categories and Markings
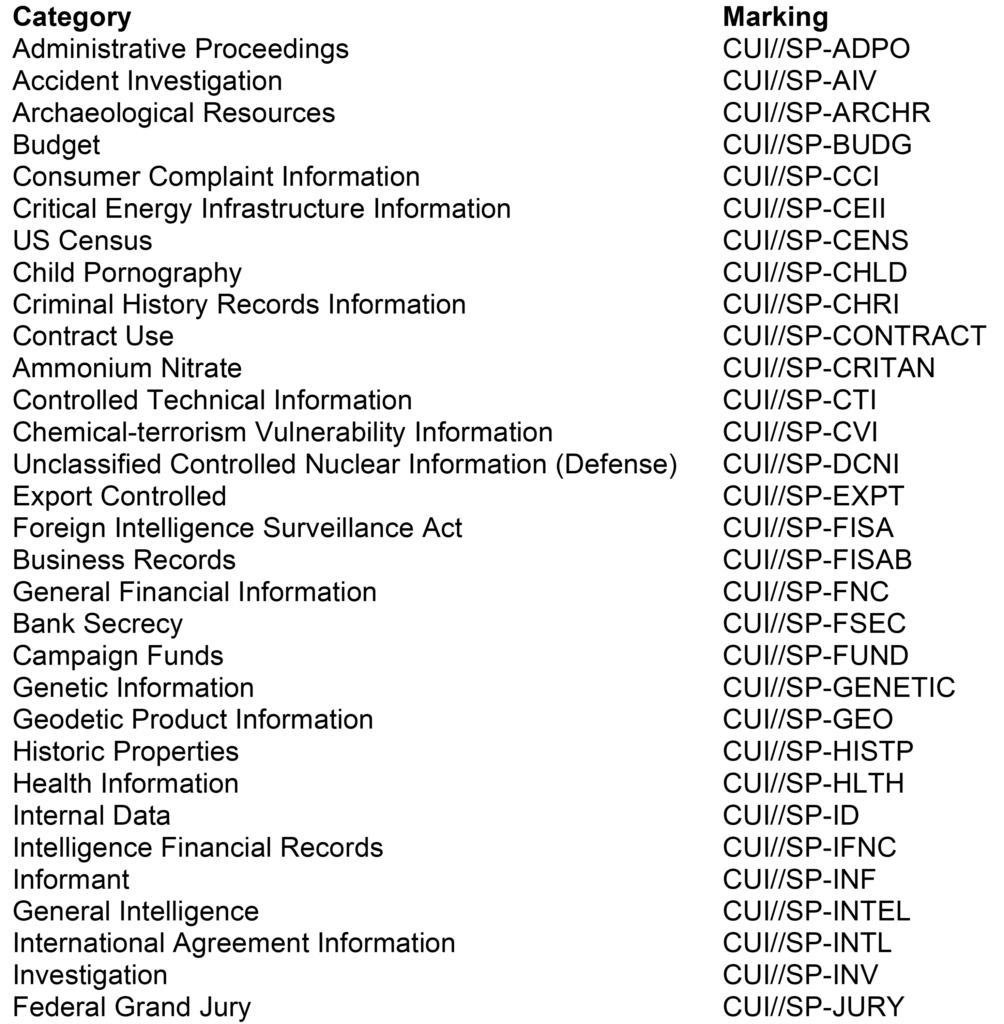
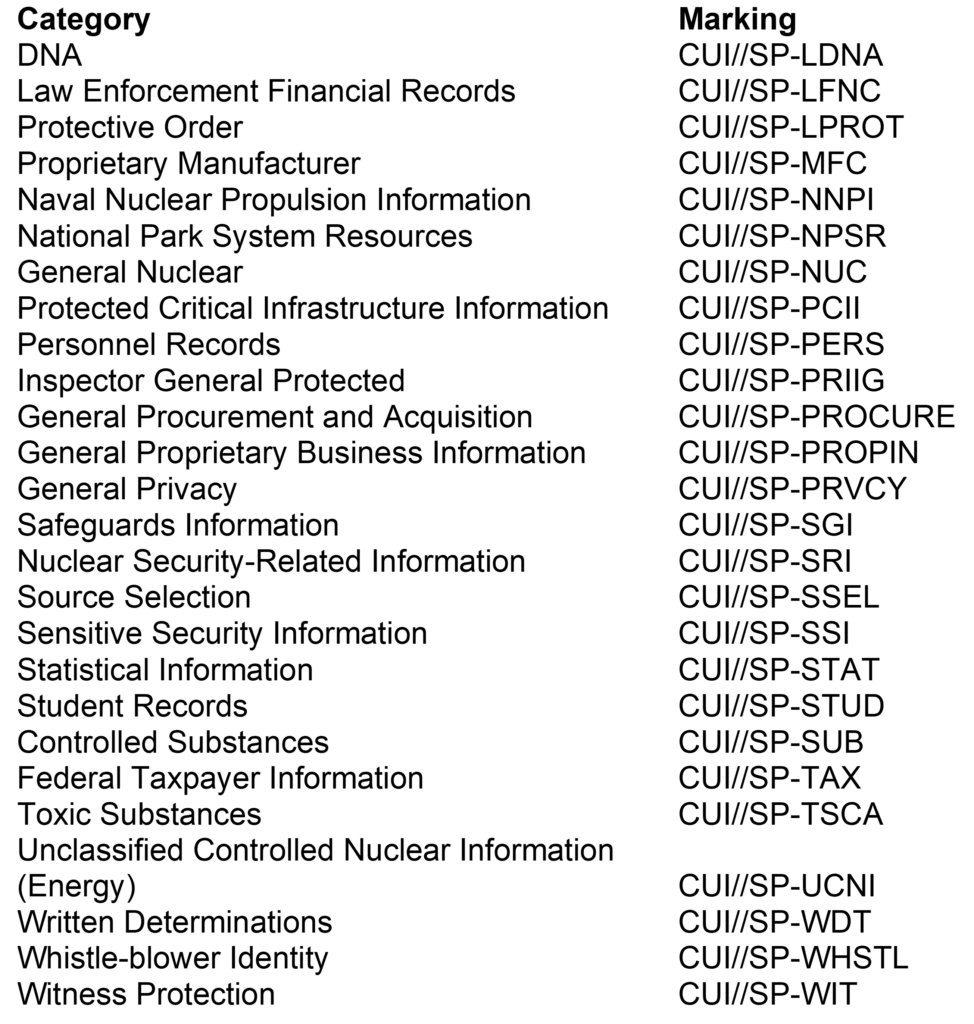
In addition to the above, two other NATO-Specific categories are considered CUI Specified. However, they don’t have default markings and include NATO Unclassified and NATO Restricted. The ISOO CUI Registry provides the mechanisms for marking these categories, and the specific markings required largely depend on the kind of content within the document.
CUI Specified Marking Description & Importance
| Category | Marking | Description | Importance |
|---|---|---|---|
| DNA | CUI//SP-LDNA | Genetic information and related data | High |
| Law Enforcement Financial Records | CUI//SP-LFNC | Financial records related to law enforcement activities | High |
| Protective Order | CUI//SP-LPROT | Legal orders for protection of individuals or entities | Medium |
| Proprietary Manufacturer | CUI//SP-MFC | Confidential manufacturing information | Medium |
| Naval Nuclear Propulsion Information | CUI//SP-NNPI | Data related to naval nuclear propulsion systems | High |
| National Park System Resources | CUI//SP-NPSR | Information about National Park resources | Low |
| General Nuclear | CUI//SP-NUC | General nuclear-related information | High |
| Protected Critical Infrastructure Information | CUI//SP-PCII | Information about critical infrastructure protection | High |
| Personnel Records | CUI//SP-PERS | Confidential information about personnel | Medium |
| Inspector General Protected | CUI//SP-PRIIG | Protected information from Inspector General | Medium |
| General Procurement and Acquisition | CUI//SP-PROCURE | Information related to procurement processes | Medium |
| General Proprietary Business Information | CUI//SP-PROPIN | Proprietary business data | Medium |
| General Privacy | CUI//SP-PRVCY | General privacy-related information | High |
| Safeguards Information | CUI//SP-SGI | Information related to security measures | High |
| Nuclear Security-Related Information | CUI//SP-SRI | Information about nuclear security | High |
| Source Selection | CUI//SP-SSEL | Information about selection of sources or contractors | Medium |
| Sensitive Security Information | CUI//SP-SSI | Information sensitive to security concerns | High |
| Statistical Information | CUI//SP-STAT | Protected statistical data | Low |
| Student Records | CUI//SP-STUD | Confidential student information | Medium |
| Controlled Substances | CUI//SP-SUB | Information about controlled substances | High |
| Federal Taxpayer Information | CUI//SP-TAX | Protected federal tax information | High |
| Toxic Substances | CUI//SP-TSCA | Information about toxic substances | High |
| Unclassified Controlled Nuclear Information (Energy) | CUI//SP-UCNI | Unclassified but controlled nuclear energy information | High |
| Written Determinations | CUI//SP-WDT | Official written determinations | Medium |
| Whistle-blower Identity | CUI//SP-WHSTL | Protected identity of whistle-blowers | High |
| Witness Protection | CUI//SP-WIT | Information related to witness protection | High |
Limited Dissemination Controls
However, CUI Specified often needs additional designation for controls beyond the markings above. One such requirement is the application of Limited Dissemination Controls (LDCs). For instance, an ITAR document usually has a NOFORN by dint of the governing regulation. However, an organization may not use limited dissemination controls other than those specified within the ISOO CUI Registry. If a document contains a CUI Banner Marking and Limited Dissemination Control Markings, the Limited Dissemination Control Markings should always be separated from the earlier CUI Banner by a double forward slash (//). Multiple LDCs within a document should be alphabetized and separated with a forward slash (/).
CUI Specified vs CDI: Is There a Difference?
Are you a defense contractor or interested in the world of defense contracting? If yes, you may have come across the term Covered Defense Information (CDI). This is because the DoD uses its own cybersecurity coordinating rules, and that’s where CDI or CTI comes in. But what is CDI? CDI is officially defined under DFARS 7012 while CUI specified is defined in 32 CFR 2002.4(r). But is there a difference between CDI vs CUI Specified? DoD uses CUI and CDI interchangeably, and, in fact, the DoD confirmed this in its Final Rule. Additionally, DoD clarified the definition of CDI to closely align with and leverage the definitions at the NARA CUI registry. Thus, it is fair to say that CDI is a subset of CUI. However, contractors should safeguard CDI, report cyber incidents, submit malicious software, and facilitate damage evaluation.
Importance of CUI Specified
Properly safeguarding CUI Specified is essential for several reasons:
1. Protection of sensitive information
CUI Specified includes information that, if mishandled or disclosed, could cause significant harm to individuals, organizations, or national security. Implementing appropriate safeguarding measures ensures the confidentiality and security of this information.
2. Compliance with laws and regulations
Organizations handling CUI Specified must adhere to specific laws, regulations, and government-wide policies. Non-compliance can result in penalties, legal consequences, or loss of government contracts.
3. Reputation and trust
Organizations that effectively manage and protect CUI Specified demonstrate a commitment to information security, fostering trust among clients, partners, and stakeholders.
How Should CUI Specified be Protected?
To protect CUI specified or basic, an organization must establish robust security measures to safeguard the information in or transiting through their internal information systems or networks. Adequate security entails adhering to the NIST SP 800-171 guidelines and following DFARS 7012. This framework encompasses 14 controls for cybersecurity and must be a contractor must fully implement. An organization is NIST SP 800-171 compliant only when it meets all requirementst unless the DoD CIO approves specific waivers or deviations. However, even with approved waivers or deviations, contractors should demonstrate their commitment to CUI protection by providing POA&M and SSP. These documents outline the progress in implementing the necessary security measures and serve as crucial components of a contractor’s risk management decision concerning CUI protection within their supply chain. However, it is worth noting that NIST is currently revising SP 800-171 Rev 2 into Rev 3.
What Level of System and Network Configuration is Required for CUI?
The level of system and network configuration required for CUI is moderate confidentiality. But What does moderate confidentiality mean? Systems and networks containing CUI must be protected from unauthorized access, use, disclosure, modification, or destruction. These systems and networks should be:
- Physically secure, with access restricted to authorized personnel only.
- Protected by firewalls and other security measures to prevent unauthorized internet or other external network access.
- Using strong passwords and encryption to protect CUI specified and Basic.
- Regularly monitored for security threats.
Besides these technical measures, organizations handling CUI specified or basic should implement appropriate personnel security measures, including training on CUI handling and conducting background checks. Background screening is critical, especially where export-controlled CUI such as ITAR or CUI marked NOFORN is involved. However, the best option is to implement the security controls in NIST SP 800-171 Rev 2. This standard includes requirements such as:
- Physical security: The systems and networks must be located in a secure area restricted to authorized personnel only.
- Access control: Access to the systems and networks must be controlled by a system of passwords, security tokens, or other authentication methods.
- Encryption: All CUI must be encrypted when stored on the systems or networks or transmitted over the network.
- Logging and monitoring: The systems and networks must be monitored for unauthorized access or activity.
- Incident response: The systems and networks must have a plan for responding to incidents involving CUI.
While there are unlimited paths or tools to implement NIST SP 800-171 Rev. 2, you must ensure CUI is protected from unauthorized access, use, disclosure, modification, or destruction. Where A CSP is involved, you must ensure that their systems meet the FedRAMP Moderate Baseline security requirements.
Identifying, Classifying, and Protecting CUI Specified with Microsoft Purview
To effectively safeguard the CUI specified, you should first identify, label, and classify it correctly. However, this can be challenging for organizations with vast amounts of data. Therefore, there’s a need for a solution that encompasses all these functionalities. Microsoft Purview is a platform that helps you govern, protect, and manage your multi-cloud, on-premises, and SaaS data. It offers data security, governance, and risk and compliance management solutions. OSCs can leverage Microsoft Purview through either commercial or Azure Government platforms such as GCC High. Azure Gov. infrastructure allows organizations to secure and manage their data and applications in a manner that meets stringent compliance standards. Additionally, enabling Azure government is the best cost-reduction strategy. It also addresses your plans for a unified cloud footprint, governance, and common identity through Azure AD for various data sets and users.
Identifying CUI Specified With Microsoft Purview
To classify CUI properly, an organization must first identify where it is created, residing, or used. Purview’s Content Search capability is equipped with advanced pattern matching and keyword recognition. This capability provides a service through which an OSC can register specific data sources. During this process, their data stays in its existing location, although a copy of its metadata referencing the location of the data source gets added to Microsoft Purview. Correctly leveraged, Purview’s features allow OSCs to turn the metadata into catalogs and dictionaries, allowing them to discover, classify, and secure the CUI specified. An OSC can map out its assessment scope and data flow by conducting a content search. They’ll also get critical information to help them make informed product and service acquisition and implementation decisions.
Besides helping OSCs identify their assessment scope and data landscape properly, Microsoft Purview Content Search also helps validate their already implemented data flow control capabilities. This is critical in meeting CMMC control AC. L2-3.1.3, which mandates organizations to map CUI flow per their approved authorizations. OSCs must properly demonstrate how effective the security controls they have in place limit CUI specified distribution. Fortunately, the organization can use Microsoft Purview Content Search to analyze search results to identify locations of CUI specified and match them up to locations authorized to store CUI.
CUI Classification with Microsoft Purview
After locating and identifying CUI specified, organizations should then classify it based on the categories and subcategories in the ISOO CUI registry. Microsoft Purview data classification feature can help OSCs achieve this goal. With Purview Data Classification features, organizations can categorize their CUI assets by assigning unique logical labels or classes to the data assets based on the business context of the data. CUI classification helps OSCs understand, search, and govern their data, as well as identify and mitigate data risks. Microsoft Purview provides over 200 built-in system classifications and the ability to create custom data classifications. OSCs can classify CUI assets automatically when they are scanned and ingested into the Microsoft Purview Data Map. They also can edit CUI manually in the Microsoft Purview governance portal after they are scanned and ingested. To identify and classify CUI Specified data assets using Microsoft Purview, you can follow these steps:
- Create a custom classification for each CUI Specified category that you need to handle, based on a regular expression pattern or dictionary. For example, you can create a custom classification for Critical Infrastructure Information (CRIT) based on the definition and examples provided by the CUI Registry.
- Configure a scan for your data sources that contain CUI Specified, such as Exchange mailboxes, Azure Data Lake Storage, conversations in Microsoft Teams, or documents in OneDrive SharePoint Online. You can use the built-in system scan rules or create custom scan rules to apply the appropriate classifications to your data assets.
- Review the scan results and the Microsoft Purview governance portal data classification dashboard. You can see the number and types of data assets that have been classified as CUI Specified, as well as your data’s locations and sensitivity levels.
CUI Protection with Microsoft Purview
Data protection is another feature of Microsoft Purview that organizations can use in their CUI-specified handling endeavors. This functionality provides a way of securing CUI assets by applying sensitivity and retention labels to the assets based on the business requirements and regulations. Leveraging this capability, OSCs can control access and dissemination of CUI. This also helps them preserve and decontrol CUI according to your legal, business, privacy, and regulatory obligations. Purview integrates with Microsoft Information Protection (MIP) and Microsoft 365 Compliance Center to provide CUI specified protections across your information systems. Organizations can manually or automatically apply sensitivity and retention labels to their CUI assets using policies and rules they define in the Microsoft 365 Compliance Center. OSCs can protect CUI Specified data assets using Microsoft Purview by:
- Creating sensitivity and a retention label for each CUI Specified category they need to handle, based on the handling requirements and guidance provided by the CUI Registry. For example, an organization can create a sensitivity and a retention label for a CUI specified category to specify the data’s encryption, access, and disposition settings.
- Publishing the sensitivity labels and retention labels to the Microsoft 365 Compliance Center. The OSC should then assign them to the relevant users and groups handling CUI Specified data.
- Applying the labels to its data assets classified as CUI Specified, using the Microsoft Purview Information Protection feature. OSCs can either manually apply the labels in the Microsoft Purview governance portal or automatically use the policies and rules they define in the Microsoft 365 Compliance Center.
CUI Monitoring and Auditing
Microsoft Purview also provides a feature that allows organizations to monitor and audit CUI residing on, being processed in, or transiting through its information systems. Hence, they can track and report events and activities related to their CUI. This is important in meeting audit and accountability requirements in the NIST SP 800-171 Rev 2. This Purview feature also helps OSCs instantly detect and investigate any incidents and anomalies that might arise. This is critical for DFARS 7012, 3 requirements in the IR Domain of the CMMC and NIST SP 800-171 Rev 2’s Incident Response controls. Organizations can use Microsoft Purview’s content explorer and activity explorer to monitor and audit CUI. The activity explorer shows the history of actions performed on CUI assets, such as scanning, classification, labeling, and modification. The content explorer shows the details of the CUI assets, such as the schema, columns, values, and labels. To monitor and audit CUI Specified data assets using Microsoft Purview, an OSC should:
- Access the activity and content explorer in the Microsoft Purview governance portal, and filter the data assets by its CUI Specified classifications.
- Review the activities and events on its CUI Specified data assets, such as who accessed, used, shared, or modified the data and when and how they did so.
- Generate reports and alerts for their CUI Specified data assets, using the built-in templates or creating custom templates in the Microsoft Purview governance portal. The OSC can also export the reports and alerts to other tools, such as Power BI or Azure Monitor, for further analysis and visualization.
CUI Cyber Incident Reporting
DFARS 7012 is a clause in government contracts that sets cybersecurity requirements for contractors handling Covered Defense Information (CDI). Rapid cyber incident reporting to the Department of Defense (DoD) is crucial. The clause applies to contractors working with CUI specified and basic, except those solely supplying Commercial off-the-shelf (COTS) items. So, what should you report? Contractors should rapidly report cyber incidents that affect a covered contractor information system or defense information. They should also report incidents affecting the contractor’s ability to perform the contract requirements designated as operationally critical support and identified in the contract. Under DFARS 7012, rapid reporting means within 72 hours of discovery.
How should you “rapidly” report cyber incidents? If a contractor discovers a cyber incident affecting CUI or CDI, they should use the DoD Incident Collection Form (ICF) on https://dibnet.dod.mil. However, they’ll need a DoD-approved medium assurance certificate to access the portal. What information does DoD need? Details of the incident, including nature, affected systems, potential impact, evidence of compromise, if any, and mitigation actions taken. The contractor should submit any malicious software discovered to the DoD Cyber Crime Center (DC3). Additionally, they must preserve and protect affected systems and data for at least 90 days after reporting. Remember, noncompliance can lead to contract termination, financial penalties, and damage to your reputation.
Who Can Decontrol CUI Specified?
Decontrolling CUI means removing any controls designed to safeguard or limit the dissemination of CUI. This can automatically happen or through direct action by the Office of the Director of National Intelligence (ODNI) or any of its components. Agencies must promptly decontrol CUI properly when determined by the CUI owner to no longer require safeguarding or dissemination controls. However, CUI decontrol must occur under the following parameters:
- When LRGWP no longer require its control as CUI and the authorized holder has the appropriate authority under the authorizing LRGWP.
- When the designating agency decides to release it to the public by making an affirmative, proactive disclosure
- When a pre-determined event or date occurs, as described in § 2002.20(g), unless LRGWP requires coordination first
- When the agency discloses it in accordance with an applicable information access statute, such as the FOIA or the Privacy Act.
Decontrolling occurs when an authorized holder, consistent with DoDI 5200.48 or the CUI Registry, removes safeguarding or dissemination controls from CUI that no longer require such controls. DoDI 5200.48 identifies three primary parties that can decontrol CUI Basic or CUI specified. They are the original classification authority (OCA), the information’s originator, and the designated office for decontrolling CUI if the information is within a classification guide. There are no specific timelines to decontrol CUI unless required in a LRGWP. Decontrol occurs when the CUI no longer requires safeguarding and must follow DOD records management procedures. Decontrolling CUI through the public release process relieves authorized holders of the requirement to handle information in accordance with the CUI program.
Conclusion
Understanding and properly managing CUI Specified is crucial for organizations handling sensitive information subject to specific legal or regulatory requirements. By implementing robust safeguards and ensuring compliance with the necessary guidelines, organizations can effectively protect CUI Specified, maintain trust with stakeholders, and avoid potential penalties or loss of government contracts. Adhering to the stringent requirements for CUI Specified not only demonstrates a commitment to information security but also ensures the protection of vital data that could have significant consequences if mishandled.
Frequently Asked Questions
Organizations can demonstrate their progress in implementing the security controls through POAM and SSPs. The two are part of a contractor’s risk management decision regarding CUI protection by their supply chain.
Include the applicable CUI marking at the top of each email. If the email containing CUI is forwarded, the Banner Marking must be moved or copied to the top of the forwarding email. It is best practice to include an indicator marking such as “Contains CUI” at the end of the subject line.
Compliance with the security controls is considered 100 percent complete if any waivers or deviations have been approved by the DOD CIO.
The deadline for implementing the security controls is 12/31/2017.
The specific security controls that should be implemented to protect CUI are defined as the implementation of NIST SP 800-171 controls for cybersecurity.
The guidance and definitions of CUI currently apply to commercial manufacturing under DOD contracts, as mentioned in their article.
Information is considered CUI in relation to contractors under two conditions. When provided to the contractor by or on behalf of DoD in connection with the performance of the contract. And, when collected, developed, received, transmitted, used, or stored by or on behalf of the contractor in support of the performance of the contract.
Yes. The CUI Category Marking is mandatory for CUI Specified. The general form for CUI Specified CategoryMarking is “SP-SPECIFIED CATEGORY. ” An example of CUI specified marking is CUI//SP-CTI.
The specific categories of CUI include CTI, critical information, export control, and any other information marked or otherwise identified in the contract that requires safeguarding or dissemination controls pursuant to and consistent with a LRGWP.
CTI stands for Controlled Technical Information, a category of CUI specified information. It refers to technical information with military or space application that is subject to controls on the access, use, reproduction, modification, display, performance, release, disclosure, or dissemination
A CUI label contains three parts, including;
- The CUI Control Marking (mandatory) may consist of either “CONTROLLED” or “CUI.”
- CUI Category Markings (mandatory for CU Specified). CUI Control Markings and Category Markings are separated by two forward slashes (//). When including multiple categories, they are separated by a single forward slash (/).
- Limited Dissemination Control Markings. Limited Dissemination Control Markings are separated from the rest of the Banner Marking by a double forward slash (//).
However, there’s an optional CUI portion marking to further distinguish portions of the information with differing classification levels or control requirements within the same document.
Share in Social Media
See More Case Studies

Securing Defense Contracts: A DFARS 252.204-7012 Compliance Case Study
Discover how Cleared Systems helped a Federal Contractor successfully achieve DFARS 252.204-7012 compliance by strengthening its cybersecurity posture, giving it a competitive edge when bidding for DoD Contracts.

What is GCC High? For ITAR & CMMC 2.0
Microsoft 365 Government Community Cloud (GCC) High is a specialized cloud solution tailored for U.S. federal, state, local, tribal, and territorial government organizations, as well as for contractors who hold or process data subject to specific security regulations. In this article, we will explore the features, benefits, and differences between Microsoft 365 GCC High and other Office 365 offerings.

Is AutoCAD ITAR Compliant? A Comprehensive Guide for Defense Manufacturers
Defense contractors and manufacturers working with sensitive military technologies face a critical question when selecting computer-aided design software: Is AutoCAD ITAR compliant? This question becomes

How to Get Help in Windows: Guide to Security and Compliance Support
In today’s digital landscape, ensuring your computer systems are secure and compliant with industry regulations is essential for both businesses and individuals. Windows, as one

Microsoft Copilot for GCC High: Enhancing Security and Compliance
In today’s fast-evolving digital landscape, organizations that handle sensitive data, particularly those in government sectors or defense contractors, face growing pressure to maintain strict security
Partner with Us for Compliance & Protection
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Security
- Compliance
- Peace of mind
- Efficiency
- Trust
What happens next?
Schedule an initial meeting
Arrange a discovery and assessment call
Tailor a proposal and solution
