CUI stands for Controlled Unclassified Information. But what is CUI? The ISOO CUI registry defines CUI as any information that requires safeguarding or dissemination controls pursuant to and consistent with applicable law, regulations, and government-wide policies but is not classified under Executive Order 13526 or the Atomic Energy Act, as amended. It is a designation used by the US government to classify unclassified information that requires safeguarding in accordance with NIST SP 800-171 and CMMC 2.0. This information may pertain to privacy, security, proprietary business interests, or government operations. Section 2002.4 of Title 32 CFR identifies two broad types of CUI: Basic and Specified. This article will delve into what basic CUI is, marking CUI basic, how it differs from the CUI specified and how to protect CUI basic.
CUI Basic Definition, What is the Definition of CUI Basic? Defining CUI Basic
What is CUI Basic?
CUI Basic is the subset of CUI for which the authorizing law, regulation, or Government-wide policy (LRGWP) does not have any specific handling or dissemination requirements. It contains baseline dissemination and handling controls identified in the November 14, 2016, Final Rule issued by NARA. CUI Basic is handled according to the uniform set of controls set forth in the CFR and the CUI Registry. In most instances, organizations can protect CUI basic by just applying the 110 security controls of NIST SP 800-171. Whenever you see a CUI basic marking on certain documents, you’ll need to implement the NIST SP 800-171 controls around the data or within that environment unless otherwise stated.
Besides marking it as CUI or Controlled, the Federal Information Systems Modernization Act requires that organizations protect CUI basic at a FISMA Moderate Level. Agencies cannot raise the external impact of CUI basic above moderate without an agreement with the external agency or contracting organization operating an information system on their behalf.
Examples of CUI Basic
There are many examples of CUI basics. Additionally, whether CUI is Basic or Specified is determined by the applicable Safeguarding and/or Dissemination Authority for that CUI. Thus, remember to always check the specific CUI marking for precise handling instructions, as requirements can vary depending on the information category. Some information that is basic CUI include:
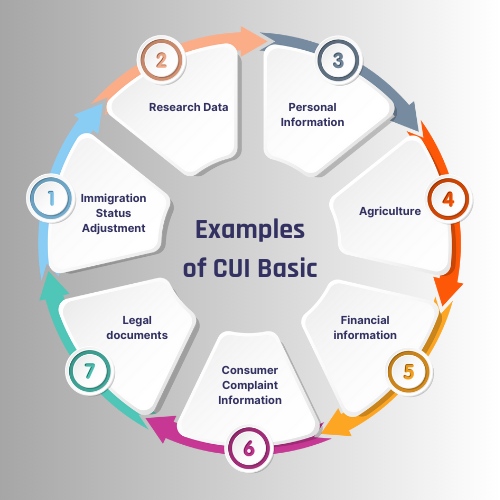
What is the difference between CUI basic and CUI specified?
Types of CUI: CUI Basic vs. CUI Specified
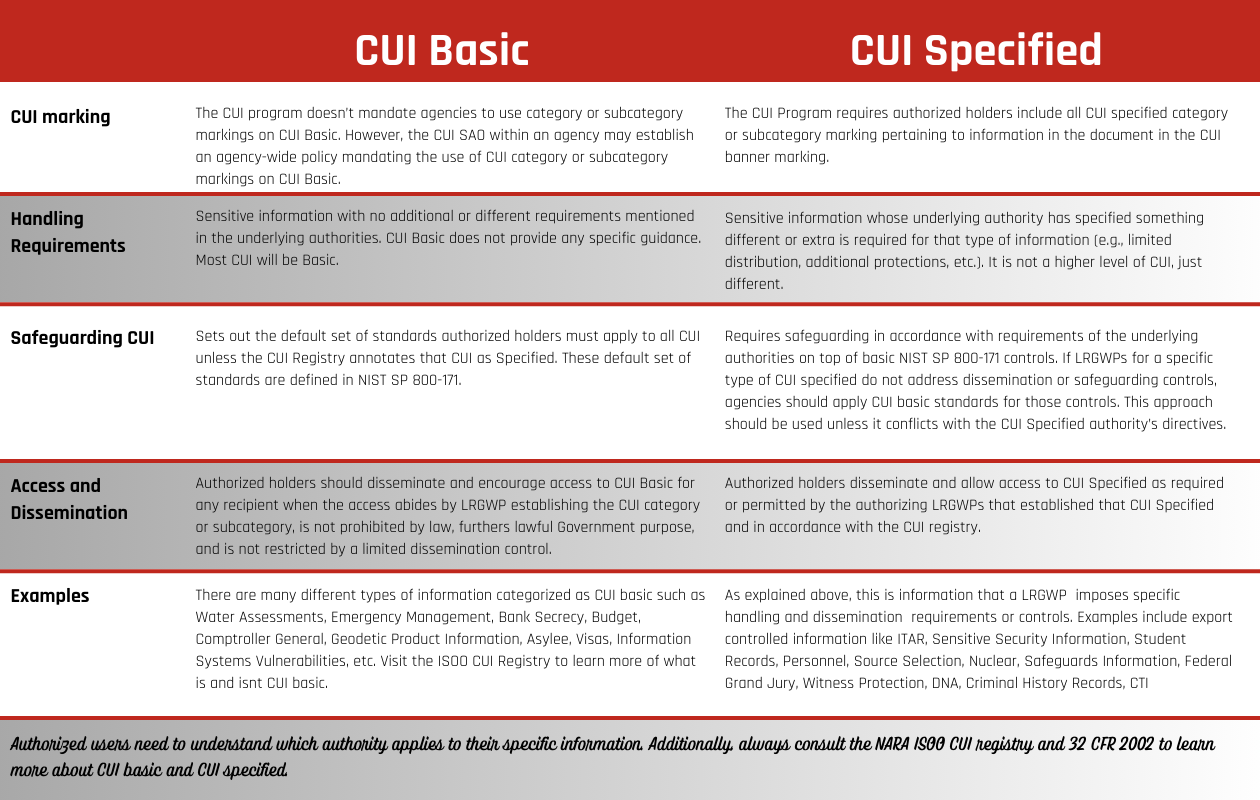
What are the differences between basic CUI and CUI specified? The two types of CUI differ primarily on handling requirements, which are informed by things like CUI marking, dissemination and access controls, safeguarding, among other CUI program requirements. So, what is the difference between CUI basic and CUI specified? Below are some areas in which the two differ:
Why Protect CUI?
Why is it Important to Protect CUI?
Though not classified, CUI Basic carries significant value and requires robust security measures to ensure its confidentiality, integrity, and availability. Understanding the “why” behind CUI protection empowers organizations to safeguard this critical information, preventing potential harm and reaping numerous benefits.
Maintaining Trust and Reputation
Organizations handling CUI must demonstrate an unwavering commitment to security. Implementing NIST SP 800-171’s stringent controls for CUI Basic safeguards not only information but also the organization’s reputation and trustworthiness. DoD and Government contracting officers will readily place their trust in organizations demonstrating robust security practices. This trust translates into a competitive edge, fostering strong partnerships and solidifying your reputation as a reliable and secure entity.
Legal and Regulatory Compliance
Compliance with CUI protection regulatory requirements is paramount. Organizations dealing with government and defense contracts are bound by specific compliance requirements mandated by federal regulations. For instance, if a contract contains DFARS clause 7012, then the awarded contractor must follow measures outlined in NIST SP 800-171 to ensure compliance. Additionally, they must ensure that cloud service providers for the environment they use have met FedRAMP moderate baseline security requirements. Failure to comply can result in hefty fines, contract termination, and damage to your legal standing.
Protection of Sensitive Information
CUI basic often includes sensitive information like proprietary business information, research data, trade secrets, and financial data. Adhering to the requirements of the CUI program ensures the confidentiality of this information and helps you maintain a competitive edge. By securing CUI, you protect sensitive information from theft or misuse.
Preventing Espionage
Information of strategic importance, such as CUI, is always sought after by US strategic competitors and adversaries. Protecting CUI helps prevent unauthorized access by competitors or malicious actors seeking to gain a competitive advantage.
Cybersecurity Concerns
Cybersecurity risks have never been higher, with malicious actors employing increasingly sophisticated tactics to breach IT systems. CUI, containing valuable information, is often a prime target for cyberattacks. A data breach involving CUI can have disastrous consequences, resulting in financial losses, reputational damage, and potential legal repercussions.
National Security Implications
Although CUI is not classified information, the malicious release of CUI poses a threat to national security. Unauthorized access to certain types of information could potentially harm a nation’s interests, making its protection vital. This can be traced from the history of the CUI program. Executive Order 13556 was in response to a major data breach at the National Archives and Records Administration (NARA) that put the records of millions of military veterans at risk. The CUI program formally acknowledged that some types of information, though not classified, are vitally sensitive and valuable to the US, and adversaries and strategic competitors are always after it.
Prerequisite for Award of Government Contracts
Many businesses engage in defense or government contracts or collaborations that involve handling CUI. Meeting the government’s stringent security requirements is not only a legal obligation but also a prerequisite for successful partnerships or contract awards. Demonstrating a commitment to CUI protection fosters trust and confidence, paving the way for long-term collaborations and lucrative contract opportunities. By prioritizing CUI security, you position your organization as a reliable and trusted partner, gaining a competitive advantage in the government contracting landscape
History of CUI
What is the History of the CUI Program?
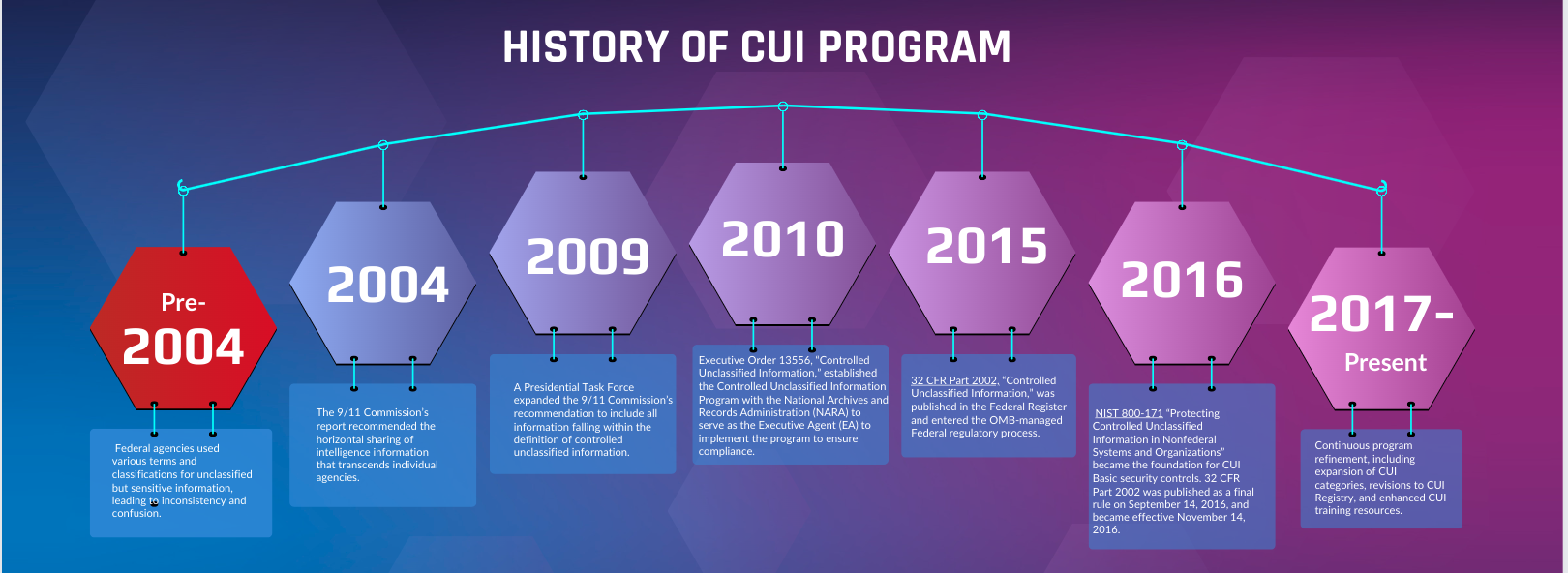
The CUI program wasn’t born overnight. Its journey began with concerns about safeguarding sensitive government information and evolved into a system we know today. The CUI program standardizes how government and contractors doing business with DoD handle and protect controlled unclassified information. Before the present CUI program, each agency used different information classifications, markings, and rules for managing and controlling information. Markings such as:
- Unclassified Controlled Technical Information (UCTI);
- Sensitive But Unclassified (SBU);
- For Official Use Only (FOUO);
- Law Enforcement Sensitive (LES);
- Sensitive Personally Identifiable Information (SPII); and
- Proprietary Business Information (PBI)
were common among defense and federal contractors and government agencies. Today, all these are combined under the Controlled Unclassified Information or CUI umbrella. Although unclassified, this information is crucial to US national defense and requires special protection to prevent unauthorized disclosure. Below is a timeline of CUI program:
- Pre-2004: Federal agencies used various terms and classifications for unclassified but sensitive information, leading to inconsistency and confusion.
- 2004: The 9/11 Commission Report highlighted the need for horizontal information sharing across agencies, prompting a shift towards standardized protection.
- 2009: A Presidential Task Force expanded the 9/11 Commission’s recommendation to include all information within the definition of controlled unclassified information.
- 2010: Executive Order 13556 established the CUI Program, assigning the National Archives and Records Administration (NARA) as the Executive Agent.
- 2015: 32 CFR Part 2002, “Controlled Unclassified Information,” was published in the Federal Register and entered the OMB-managed Federal regulatory process.
- 2016: NIST 800-171 “Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations” became the foundation for CUI Basic security controls. 32 CFR Part 2002 was published as a final rule on September 14, 2016, and became effective November 14, 2016.
- 2017-Present: Continuous program refinement, including expansion of CUI categories, revisions to CUI Registry, and enhanced CUI training resources.
How do I Know if I Have CUI Data?
Members of the DIB, prime- and sub-contractors, and vendors comprising the DoD supply chain should protect certain types of information they process when doing business with the DoD. This information is called CUI, and it has been defined above. But how do you know you have CUI data? Most defense contracts have a DFARS clause 252.204-7012 to protect DoD-related CUI, otherwise called Controlled Defense Information (CDI). However, what constitutes CUI remains unclear to many. They are left asking, “How do I know what is CUI data?”
Based on the CUI definition, it is any information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a LRGWP requires or permits an agency to handle using safeguarding or dissemination controls. Organizations can determine they have CUI data by asking the following question from this definition of CUI:
- Was the data originally owned or created by the Government and provided to you in association with a solicitation or contract?
- Will you be using the data to deliver your contractual responsibilities to a DoD prime contractor or Government?
- Can you identify the data type within categories or sub-categories listed on the NARA ISOO CUI registry?
The three questions will help you identify what is considered CUI data so that you can take the required measures to secure it.
Examples of CUI Basic
| Category | Marking | Description |
|---|---|---|
| Agriculture | CUI//BASIC | Information related to agriculture that requires safeguarding |
| Copyright | CUI//BASIC | Copyrighted material requiring protection |
| Export Control | CUI//BASIC | Information subject to export control regulations |
| Financial | CUI//BASIC | Sensitive financial information |
| Immigration | CUI//BASIC | Information related to immigration matters |
| Intelligence | CUI//BASIC | Intelligence-related information not classified but requiring protection |
| International Agreements | CUI//BASIC | Information protected by international agreements |
| Law Enforcement | CUI//BASIC | Sensitive law enforcement information |
| Legal | CUI//BASIC | Legal information requiring protection |
| North Atlantic Treaty Organization (NATO) | CUI//BASIC | NATO-related information requiring safeguarding |
| Patent | CUI//BASIC | Patent-related information requiring protection |
| Privacy | CUI//BASIC | Personal privacy information |
| Procurement and Acquisition | CUI//BASIC | Sensitive information related to procurement processes |
| Proprietary Business Information | CUI//BASIC | Business information requiring protection |
| Provisional | CUI//BASIC | Information provisionally determined to require protection |
| Tax | CUI//BASIC | Tax-related information requiring safeguarding |
Is FOUO CUI?
Is information that is marked as FOUO, CUI? DoDI 5200.48 identifies FOUO as a legacy marking. Information marked For Official Use Only (FOUO) can remain on DoD servers without a need for remarking. However, the information should be updated to CUI or “U” if it meets a CUI definition. FOUO marking was authorized to protect UNCLASSIFIED information that “may be exempt from mandatory disclosure under the Freedom of Information Act (FOIA).” Under 32 CFR 2002.1(c), CUI is unclassified information that requires any safeguarding or dissemination control throughout the executive branch. Thus, since FOUO is unclassified and requires safeguarding, it can be regarded as CUI. One could say FOUO meets the definition of CUI.
Although DoDI 5200.48 states that legacy marking, including FOUO, generally isn’t CUI, it requires that DoD reviews all information before disseminating it and ensuring it is Marked CUI. After all, DoD is the originator. So, does all legacy marked FOUO qualify as CUI? Not necessarily. It is not an automatic one-to-one swap. Some information previously marked as FOUO will qualify as CUI. FOUO has a habit of suddenly becoming CUI and, in rare cases, Secret.
Safeguarding CUI Basic
Although not classified or subject to an LRGWP, organizations, and contractors must take all measures to safeguard CUI basics. Authorized holders in these organizations must take reasonable precautions to protect CUI basic against unauthorized disclosure. What are the safeguards for CUI?
Identify and Classify CUI
The first step in safeguarding CUI is determining that you indeed process, store, or transmit CUI in your organization. You must identify the information as CUI and classify it based on the marking. As mentioned above, there are 2 types of CUI: basic and specified. Thus, after identifying CUI, organizations should classify it and apply appropriate marking in line with the ISOO CUI registry. There are many tools for identifying and categorizing CUI in federal and non-federal systems, as described above. For proper categorization, organizations must properly identify and mark CUI first.
Establish Controlled Environment
CUI generally has specific access and dissemination controls subject to the authorizing LRGWP, particularly for CUI Specified. However, this doesn’t mean any person is allowed to see or disseminate it. The basic CUI handling controls established in NIST SP 800-171 require that organizations protect not only information systems but also environments where CUI is handled. Thus, they implement virtual and physical restrictions to limit access to CUI basic using NIST SP 800-171 as the guide. This may involve creating dedicated rooms in their facility, securing networks or specific computer systems handling CUI. However, the Authorized holder should test and examine the controlled environment using NIST SP 800-171A for functional assurance purposes. You must ensure unauthorized individuals can’t access or observe CUI or overhear conversations discussing CUI.
Establish Identity and Access Management (IAM) Policy
Who can access CUI basic? How do you obtain access to CUI? The two questions are critical when designing a CUI basic access policy. However, for a person to access CUI, they must have a lawful government purpose and must be authorized through some form of authentication. Thus, organizations handling CUI need a robust Identity and Access Management (IAM) Policy in place. You can use physical access devices, biometrics, or other IoT-enabled access control devices to restrict physical access to the controlled environment. To restrict digital access only to authorized personnel, implement robust authentication protocols and authorization mechanisms. All access to CUI basic granted should be on zero trust and NIST SP 800-171’s least access privilege principle. Role Based Access Controls (RBAC) can help organizations assign specific permissions. Regularly review user access rights and revoke them when no longer needed, for instance, when an employee’s contract is terminated.
Secure Confidentiality of CUI Basic
Confidentiality of any information, including CUI basic, is of utmost importance both in transit and rest. Therefore, organizations must ensure CUI basic remains confidential and only accessible to those authorized or with legitimate government purposes. There are different means of ensuring information remains confidential, including encryption, secure storage, and file share scanning, among others. Does CUI need to be encrypted? Yes. Organizations should use FIPS-validated cryptographic modules to secure CUI basic during transmission over networks or when stored in servers or devices. By encrypting the CUI, you can keep it secure and confidential even in the event of unauthorized access. Additionally, take measures to prevent any transmission of information classified CUI over unencrypted media or networks. However, encryption without a strong way of managing encryption keys is an exercise in futility. Hence, implement key management solutions for secure generation, storage, and access control.
Employee Training
Improper employee practices constitute the biggest source of cybersecurity risks facing organizations. This holds when it comes to securing CUI basic. Give your employees CUI training to understand its handling, marking, and dissemination controls, if any. This will ensure that your employees follow your organization’s CUI security policy and help eliminate preventable mistakes that might otherwise place your data at risk. By conducting regular cybersecurity awareness and CUI training, your employees will also understand the importance of protecting CUI, following security protocols, recognizing potential threats, and Fostering a culture of cybersecurity awareness.
Regularly Security Audits and Assessments
Organizations should regularly audit their information systems and physical facilities to assess the effectiveness of the existing security measures and identify vulnerabilities. Penetration testing is one of the mechanisms used to assess CUI handling systems. Whenever vulnerabilities are identified, address them quickly to minimize attack surfaces. Besides conducting self-assessments on their internal systems, organizations should also conduct security assessments on third-party systems with which they share CUI basics. They should ensure that third-party solutions, like Cloud Service Providers (CSPs), are compliant with any LRGWP governing CUI handling. Additionally, DFARS 7012 requires that the contractor flows down the CUI handling requirements to any subcontractors involved in contract performance.
Fully Implement NIST SP 800-171 and DFARS 7012 Security Requirements
Implementing NIST SP 800-171 and DFARS 7012 represents a comprehensive approach to safeguarding CUI. NIST SP 800-171 mandates the adoption of 110 security controls across 14 families, encompassing access control, incident response, and system and information integrity, among others. By enforcing these controls, organizations ensure that access to CUI is strictly regulated, monitored, and protected against unauthorized disclosure. The structured guidelines help in establishing a robust security posture that mitigates risks from cyber threats, insider threats, and accidental leaks. Implementing NIST SP 800-171 fosters a culture of security awareness and resilience, which is essential for maintaining the confidentiality, integrity, and availability of sensitive information.
DFARS 7012 further enhances the protection of CUI by mandating defense contractors to report cyber incidents that affect CUI or their ability to perform tasks critical to defense missions. This clause extends the cybersecurity framework by requiring rapid incident reporting, thorough incident investigation, and the submission of malicious software to the DoD if discovered during the investigation. The synergy between DFARS 7012 and NIST SP 800-171 ensures a defense-in-depth strategy, where not only are proactive measures implemented to secure CUI against unauthorized access and cyber threats, but reactive measures are also in place to respond effectively to incidents. This holistic approach significantly reduces the risk of compromising sensitive defense-related information, thereby supporting national security objectives.
What is a CUI Enclave? Defining CUI Enclave, Defination for Enclave, CUI Enclave Meaning
CUI Enclaves: An Effective Way To Secure CUI Basic
What are CUI Enclaves? CUI enclaves are unique, purpose-built, stand-alone information systems that process and store sensitive data types like ITAR and other types of CUI. It does this by establishing a software-defined perimeter around the included resources. A more official enclave definition is set of system resources that operate within the same security domain and that share the protection of a single, standard, and continuous security perimeter. The purpose of a CUI enclave is to separate various types of data and provide an extra security layer, limiting unauthorized access, disclosure, or dissemination of CUI. Applying the NIST SP 800-171 and NIST 800-37 policies to your CUI enclave instead of applying them to your entire business will lower the burden on those managing the infrastructure. CUI-compliant enclaves also help you segment sensitive data properly. Additionally, a security enclave helps organizations mitigate workload constraints stemming from complete infrastructure migration.
Organizations can pursue a selective migration strategy with network and computer network approaches. They can isolate select workloads and approaches within secure environments while ensuring the rest of the infrastructure remains intact and compliant with CMMC and DFARS, among other compliance requirements.
Using CUI Enclaves to Implement Security Measures
This CUI solution is usually implemented using a combination of physical and logical measures. It involves using both hardware and software security controls. These measures and controls isolate the enclave from your facility’s broader network. This ensures that only authorized individuals access information within that security enclave. Some of these controls include:
Physical Controls
- Limiting Access: Implement access controls such as keycards, biometrics, or security cameras to restrict entry into work enclaves. This ensures that only authorized personnel can access information, enclave computers, etc., enhancing the environment’s security.
- Secure Storage: Utilize secure storage solutions like locked cabinets, safes, or secure storage containers for physical CUI media and other enclave computing devices. This includes documents, CDs, and other forms of physical media.
- Environmental Controls: CUI security goes beyond protecting it against cyber threats. By its definition, an enclave should have appropriate environmental conditions, including temperature, humidity, and dust control. Remember, CUI must be destroyed per agency policy and to a degree that makes the information unreadable, indecipherable, and irrecoverable. Implementing these measures prevents damage to physical media and ensures the longevity and reliability of the data stored.
- Soundproof offices: To ensure visitors or unauthorized personnel don’t overhear conversations involving CUI basic, consider soundproofing offices where such meetings take place.
Virtual Controlled Environments
Network Segmentation
Create network enclaves by separating networks for CUI systems from other networks within your facility. But what is a network enclave? A network enclave is an internal network segment that gets separated from the rest of your digital infrastructure. Organizations can achieve this by using firewalls and other security controls, reducing the risk of unauthorized access.
Zero Trust Security Model
Today, employees prefer working on their devices or bringing them to their workplaces. The BYOD increases your attack surface as the number of physical and virtual endpoints increases drastically. Thus, define a secure enclave by implementing a Zero Trust approach where every user and device requires verification and authorization before accessing any resources in your IT enclave.
Access Controls
Implement Role-Based Access Control (RBAC) based on the principle of least privilege access. This system grants access to CUI systems and data based on job duties and clearance levels, ensuring that users only have access to the information necessary for their roles. This protects CUI and ensures that enclave software, servers, networks and other IT systems remain secure. However, the access controls implemented should be auditable. They should clearly describe your CUI landscape, who accessed it, and where and when.
Strong Authentication
Enforce the use of strong passwords and Multi-Factor Authentication (MFA). These secure login methods provide an additional layer of security and make unauthorized access more difficult.
Encryption
Encrypt CUI data both at rest and in transit using NIST-validated cryptographic modules. Encryption makes the data unreadable without the correct decryption key, further securing the information. Since meetings can now be conducted online via various sources, leverage encrypted video conferencing or phone lines for remote discussions. Additionally, consider encrypting data and virtual machines, system backups, networks, and sensitive configurations.
Logging and Monitoring
Monitor system activity and log all access attempts to CUI systems. This allows for detecting any unusual or suspicious activity, enabling timely response to potential security threats within your CUI enclave. In addition, implement DLP solutions to prevent unauthorized data exfiltration through email, USB drives, or other channels. Audit the logs and monitoring systems regularly to Ensure CUI is safe and intact.
Virtual Desktop Infrastructure (VDI)
A great enclave software is a VDI. It allows secure remote access to information marked CUI in a compliant manner. Hence, consider using VDI like Azure Virtual Desktop (AVD) to provide secure access to CUI systems. You can enhance security and control over the virtual environment by using dedicated virtual machines instead of physical endpoints.
CUI Enclave Architecture
As explained when defining an enclave, it’s designed to be isolated from other network elements. Individuals must be properly authenticated before gaining physical or logical access to the enclave. Once inside the enclave, users can only access information required to perform their duties under the least privilege principle. CUI or CMMC enclaves are designed to be tamper-proof. Thus, the enclave software and hardware components are designed to detect and respond to attempts of electronic or physical alteration to the system. This maintains the integrity of the CUI within the enclave. The other essential aspect of enclave architecture is that they’re designed to meet the specific LRGWP governing the handling of CUI, such as CMMC and DFARS 7012. Enclaves can be used in various contexts, including:
- Internet of Things (IoT): Organizations can use work enclaves to create isolated, secure environments on IoT devices to protect all data collected and transmitted via or by these devices.
- Cloud Environments: OSCs can use computing enclaves to create secure, isolated, stand-alone information system environments within a cloud computing platform. Thus, they can access CUI stored in these systems securely. However, always ensure you follow DFARS 7012 requirements on cloud service providers. They must be authorized at a FedRAMP moderate baseline or higher to store CUI.
- Privately Hosted and Virtual: You can also configure and access enclaves through VDIs to ensure CUI remains within that work enclave’s technical boundary.
Benefits of a CUI Enclave
A CUI (Controlled Unclassified Information) enclave provides a secure environment for handling, storing, and processing CUI. The benefits of establishing a CUI enclave include:
- Enhanced Security: CUI enclaves have robust security measures to protect sensitive information from unauthorized access, disclosure, and cyber threats. These security measures may include physical security controls, access controls, encryption, and network security protocols, ensuring that CUI is handled securely throughout its lifecycle.
- Compliance with Regulations: Establishing a CUI enclave helps organizations comply with federal regulations and guidelines for handling CUI, such as the National Institute of Standards and Technology (NIST) Special Publication 800-171. Compliance reduces the risk of penalties, fines, and damage to reputation that can result from non-compliance.
- Scalability and flexibility: implementing cloud-based CUI enclaves provides the scalability and flexibility of cloud computing and ensures a secure environment for various critical assets.
- Improved Information Sharing: A CUI enclave facilitates secure and efficient sharing of CUI among authorized individuals and entities. By providing a controlled environment for accessing and disseminating CUI, organizations can collaborate more effectively while protecting sensitive information.
- Risk Management: By implementing a CUI enclave, organizations can better manage the risks associated with handling sensitive information. The enclave provides a framework for identifying, assessing, and mitigating risks, which can help prevent data breaches and other security incidents.
- Cost Saving: Consolidating Controlled Unclassified Information (CUI) into a dedicated enclave can lead to significant cost savings for organizations. This is beneficial compared to the alternative of implementing the same stringent security measures across an entire general computing environment.
Conclusion
Now that we understand what is CUI basic, understanding and properly handling it is crucial for organizations that deal with sensitive information. By implementing appropriate safeguarding measures and adhering to federal regulations, organizations can effectively protect CUI and demonstrate their commitment to information security. As the digital landscape continues to evolve, it is essential to stay informed about the latest developments in CUI Basic and other information security measures to maintain a robust and secure environment. Learn more about CUI here.
CUI Frequently Asked Questions
CUI is any information that requires safeguarding or dissemination controls pursuant to and consistent with applicable law, regulations, and government-wide policies but is not classified under Executive Order 13526 or the Atomic Energy Act, as amended.
No. The CUI Category Marking is optional for CUI Basic, but it is best practice and may be required by agency-specific policies.
32 CFR 2002.4(m) identifies the National Archives and Records Administration (NARA) as the CUI Executive Agent responsible for overseeing the CUI program. However, NARA has delegated this authority to the Director of the Information Security Oversight Office (ISOO). Thus, the Director ISOO is the CUI EA.
CUI encompasses unclassified information requiring specific safeguards due to its sensitivity or potential misuse. Protecting CUI basic is crucial for national security, economic prosperity, and public safety.
- Issuing guidance on CUI identification, marking, security, and dissemination.
- Maintaining the CUI Registry, a central repository for CUI categories and safeguarding requirements.
- Overseeing agency compliance with CUI program requirements.
- Collaborating with stakeholders, including federal agencies, industry, and academia, on CUI-related issues.
Protecting Controlled Unclassified Information (CUI) is a shared responsibility. Anyone who creates information that is considered CUI is responsible for protecting and correctly handling it. Depending on context:
- NARA ISOO acts as the Executive Agent for the CUI program. They oversee implementation, compliance, and provide guidance to agencies.
- Federal Agencies
- Designate CUI: Identify and mark CUI information.
- Protect: Implement security controls based on CUI type (Basic or Specified) and agency policies.
- Disseminate CUI: Apply CUI limited dissemination controls and share CUI securely with contractors and other authorized recipients.
- Federal and DoD Contractors: Follow agency CUI protection requirements in contracts (e.g., DFARS 7012) and implement necessary CUI safeguards detailed in NIST SP 800-171 and NIST SP 800-172. Flow down CUI safeguarding requirements to their subcontractors.
- Employees: Should only access and use only with proper authorization and training and in a compliant manner. Whenever they notice suspicious activity or breaches involving CUI, they should immediately report to their immediate superiors or authorized holders.
Ultimately, everyone handling CUI shares responsibility for its protection. While agencies and contractors set policies, individuals must follow them and report any potential risks.
The ISOO CUI registry identifies 2 types of CUI; CUI basic and CUI specified.
Yes. DFARS 7012 requires government and DoD contractors encrypt for CUI in transit and at rest usinf FIPS compliant cryptographic modules. As a good CUI handling practice, encrypt networks, files resting in servers and computers, emails, etc. Restrict use of portable devices and if any is used to transfer or stire CUI, ensure it is encrypted and protected using physical access protections such as biometrics.
CUI can trace its roots from three authorities, including;
- Executive Order 13556, “Controlled Unclassified Information,” published on November 4, 2010
- 32 Code of Federal Regulations, part 2002, first published on September 14, 2016
- DoDI 5200.48, “Controlled Unclassified Information (CUI)” March 6, 2020
- Law, Regulation, or Government-Wide Policy: This is the most important factor. If a specific law, regulation, or government-wide policy requires or permits an agency to handle information with safeguarding or dissemination controls, it can be designated as CUI.
- Identification in the National CUI Registry: NARA maintains a central registry of specific categories of information designated as CUI. If your information falls within one of these categories, it qualifies as CUI.
- Designation by an Authorized Official: In some cases, an authorized official within an agency can designate information as CUI if it meets specific criteria and is not already covered by existing laws or the CUI registry.
DoDI Instruction 5200.48 Controlled Unclassified Information (CUI). DoDI 5200.48 establishes policy, assigns responsibilities, and prescribes procedures for CUI throughout the DOD and establishes the official DOD CUI Registry.
No. CUI isn’t a classification and shouldn’t be referred to as “classified as CUI.” A better way to phrase it is “controlled as CUI.” In fact, CUI is a safeguarding mechanism for UNCLASSIFIED information. CUI and CNSI have separate, co-equal Executive Orders and implementing directives.
An agency’s Senior Agency Official (SAO) may approve marking waivers for CUI when marking is excessively burdensome and the information remains within agency control.
Not necessarily. Whether to mark it as CUI depends on what PII is on the document. If the individual pieces of PII in a document can be combined and collaboratively used to identify a specific person, then mark it as CUI.
Administrative, civil, or criminal sanctions may be imposed if there is an unauthorized disclosure (UD) of CUI.
CUI program was established vide executive order 13556 to standardize the way the Executive branch handles sensitive information that requires dissemination controls
Share in Social Media
See More Case Studies

Securing Defense Contracts: A DFARS 252.204-7012 Compliance Case Study
Discover how Cleared Systems helped a Federal Contractor successfully achieve DFARS 252.204-7012 compliance by strengthening its cybersecurity posture, giving it a competitive edge when bidding for DoD Contracts.

What is GCC High? For ITAR & CMMC 2.0
Microsoft 365 Government Community Cloud (GCC) High is a specialized cloud solution tailored for U.S. federal, state, local, tribal, and territorial government organizations, as well as for contractors who hold or process data subject to specific security regulations. In this article, we will explore the features, benefits, and differences between Microsoft 365 GCC High and other Office 365 offerings.

Is AutoCAD ITAR Compliant? A Comprehensive Guide for Defense Manufacturers
Defense contractors and manufacturers working with sensitive military technologies face a critical question when selecting computer-aided design software: Is AutoCAD ITAR compliant? This question becomes

How to Get Help in Windows: Guide to Security and Compliance Support
In today’s digital landscape, ensuring your computer systems are secure and compliant with industry regulations is essential for both businesses and individuals. Windows, as one

Microsoft Copilot for GCC High: Enhancing Security and Compliance
In today’s fast-evolving digital landscape, organizations that handle sensitive data, particularly those in government sectors or defense contractors, face growing pressure to maintain strict security
Partner with Us for Compliance & Protection
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Security
- Compliance
- Peace of mind
- Efficiency
- Trust
What happens next?
Schedule an initial meeting
Arrange a discovery and assessment call
Tailor a proposal and solution
