Penetration Testing Consulting Services
In today’s complex digital landscape, safeguarding sensitive information is paramount, especially for federal and defense contractors who handle classified data. At Cleared Systems, we provide comprehensive Penetration Testing Services also know as pen testing is designed to meet the stringent compliance requirements and security needs of government contractors. Our services are tailored to identify vulnerabilities, assess risks, and enhance the overall security posture of your organization.
What is Penetration Testing
Penetration testing, also known as ethical hacking, is a proactive security assessment method where authorized professionals simulate cyberattacks on an organization’s IT systems, networks, or applications. The purpose of penetration testing is to identify and exploit vulnerabilities, weaknesses, or misconfigurations that could be used by malicious hackers to gain unauthorized access or cause harm. By simulating real-world attack scenarios, penetration testing helps organizations understand the potential impact of security breaches and provides valuable insights into how to strengthen their defenses. This process is essential for maintaining a robust security posture, ensuring compliance with industry standards, and protecting sensitive information from evolving cyber threats.
Why do you need Penetration Testing?
In an era where cyber threats are increasingly sophisticated and pervasive, ensuring the security of your organization’s digital assets is more critical than ever. For federal and defense contractors, the stakes are even higher, as the protection of sensitive and classified information is not just a priority—it’s a mandate. Penetration testing, or ethical hacking, is a vital security practice that allows organizations to proactively identify and address vulnerabilities before they can be exploited by malicious actors. By simulating real-world cyberattacks, penetration testing helps you strengthen your defenses, achieve compliance with stringent regulations, and safeguard the integrity of your IT infrastructure.
Penetration testing is essential for several reasons:
Identify Vulnerabilities: Penetration testing helps uncover hidden vulnerabilities in your systems, networks, and applications that could be exploited by malicious hackers. By identifying these weaknesses, you can take proactive measures to secure your infrastructure.
Enhance Security Posture: Regular penetration testing strengthens your overall security posture by providing insights into potential risks and offering actionable recommendations to mitigate them.
Compliance Requirements: Many industries, especially federal and defense sectors, require penetration testing to comply with regulations like NIST, DFARS, CMMC, and ITAR. Penetration testing ensures that your organization meets these compliance standards.
Prevent Data Breaches: By simulating real-world attacks, penetration testing helps you understand how an actual breach could occur and what the impact would be. This knowledge allows you to implement safeguards to prevent data breaches and protect sensitive information.
Risk Management: Penetration testing provides a clear understanding of the risks your organization faces, allowing you to prioritize security efforts and allocate resources effectively to address the most critical vulnerabilities.
Continuous Improvement: Cyber threats are constantly evolving, and regular penetration testing ensures that your security measures keep pace with new attack methods. This continuous improvement process helps you stay ahead of potential threats.
Our Penetration Testing Services
Network Security Penetration Testing
Your network is the backbone of your IT infrastructure. Our Network Security Penetration Testing assesses the security of your entire network by identifying vulnerabilities in routers, switches, and other networking devices. We simulate attacks on your network to uncover potential breaches and offer actionable insights to strengthen your network defenses.
Firewall Penetration Testing
Firewalls are the first line of defense against cyber threats. Our Firewall Penetration Testing simulates real-world attacks to evaluate the strength and effectiveness of your firewall configurations. We identify potential entry points, misconfigurations, and weaknesses that could be exploited by adversaries, ensuring that your firewall is robust enough to protect your network.
Web Application Penetration Testing
Web applications are often targeted by cybercriminals looking to exploit vulnerabilities. Our Web Application Penetration Testing service evaluates the security of your web applications, identifying issues such as SQL injection, cross-site scripting (XSS), and other common vulnerabilities. We provide detailed reports and remediation strategies to protect your applications from attacks.
Hardware Penetration Testing
Hardware devices, including IoT devices and embedded systems, can be entry points for cyber threats if not properly secured. Our Hardware Penetration Testing assesses the security of your hardware components by simulating attacks that could compromise your devices. We help you identify and mitigate risks, ensuring that your hardware is secure against tampering and unauthorized access.
Compliance Penetration Testing
Federal and defense contractors must comply with various regulations, including NIST, DFARS, CMMC, and ITAR. Our Compliance Penetration Testing services are designed to ensure that your systems meet the required compliance standards. We conduct thorough assessments based on specific regulatory requirements, providing you with the assurance that your systems are secure and compliant.
Cloud Computing Penetration Testing
As more federal and defense contractors migrate to cloud environments, securing cloud-based systems has become critical. Our Cloud Computing Penetration Testing focuses on identifying vulnerabilities in cloud infrastructure, including configurations, access controls, and data storage. We ensure that your cloud environment complies with federal regulations and is secure against unauthorized access and data breaches.
Mobile Penetration Testing
With the increasing use of mobile devices in federal and defense sectors, securing mobile applications is crucial.
Our Mobile Penetration Testing service evaluates the security of your mobile apps, identifying vulnerabilities that could be exploited by attackers. We test for issues such as insecure data storage, improper session handling, and weak encryption, providing recommendations to secure your mobile applications.
IoT Penetration Testing
IoT Penetration Testing focuses on identifying and fixing vulnerabilities within your Internet of Things (IoT) devices and systems. As IoT devices integrate into critical operations, they can become targets for cyber threats. Our service simulates real-world attacks to uncover weaknesses in your devices, networks, and communication protocols, including insecure data storage, weak authentication, and unencrypted communications. By securing your IoT ecosystem, we help you prevent unauthorized access, protect sensitive data, and ensure compliance with industry standards.
Social Engineering Penetration Testing
Evaluate the resilience of your organization’s personnel against targeted attacks, such as phishing and spear-phishing campaigns, which are commonly used to breach federal and defense contractors. This testing simulates social engineering tactics to identify and address weaknesses in employee security training, reducing the risk of human error leading to a security breach.
Physical Penetration Testing
Test the physical security of your facilities, which is critical for federal contractors handling sensitive information or operating in secure locations. This service includes attempts to bypass physical security controls such as badge systems, surveillance, and perimeter defenses, ensuring your premises are protected against unauthorized physical access.
Endpoint Penetration Testing
Focus on the security of endpoints such as desktops, laptops, and mobile devices. For federal contractors, securing endpoints is crucial as they often access sensitive or classified information. This service identifies vulnerabilities in endpoint configurations and software, helping prevent unauthorized access and data breaches.
Wireless Network Penetration Testing
Assess the security of your wireless networks, crucial for federal facilities where secure communication is paramount. This service identifies vulnerabilities like weak encryption and unauthorized access points, ensuring that your wireless infrastructure complies with strict federal security standards and is safeguarded against unauthorized access.
Red Teaming
Conduct a comprehensive, simulated attack on your organization that mirrors potential threats from advanced persistent threats (APTs) targeting federal and defense contractors. Red Teaming involves testing both digital and physical defenses, providing a holistic view of your security posture and ensuring your defenses can withstand sophisticated, multi-vector attacks.
SCADA/ICS Penetration Testing
Secure your Industrial Control Systems (ICS) and SCADA environments, which are often critical to national security and defense operations. This service identifies vulnerabilities in your control systems, ensuring they are protected against cyber threats that could disrupt critical infrastructure or defense-related operations.
API Penetration Testing
Assess the security of your Application Programming Interfaces (APIs), which are increasingly used in defense and federal applications. This service focuses on ensuring your APIs meet stringent security requirements, protecting sensitive data and systems from unauthorized access and ensuring compliance with federal cybersecurity mandates.
Why Choose Cleared Systems?
Expertise in Federal and Defense Sector: With years of experience in the federal and defense sectors, we understand the unique security challenges faced by government contractors. Our team of certified penetration testers has extensive knowledge of federal regulations and compliance requirements.
Tailored Solutions: We provide customized penetration testing services tailored to your specific needs, ensuring that we address the unique security challenges of your organization.
Comprehensive Reporting: Our detailed reports include an overview of vulnerabilities found, risk assessments, and actionable recommendations to enhance your security posture.
Regulatory Compliance: We ensure that our testing methods and remediation strategies align with federal regulations, helping you maintain compliance with NIST, DFARS, CMMC, ITAR, and other relevant standards.
Continuous Support: Beyond penetration testing, we offer continuous support to help you implement security measures and maintain a strong defense against evolving cyber threats.
Get Started with Penetration Testing Today
Secure your systems and maintain compliance with Cleared Systems. Contact us today to learn more about our Penetration Testing Services and how we can help you protect your organization from cyber threats while meeting federal and defense contracting requirements.
What is penetration testing?
Penetration testing, also known as ethical hacking, is a simulated cyberattack on your systems to identify and exploit vulnerabilities. The goal is to find weaknesses before malicious hackers can exploit them.
Why is penetration testing important for federal and defense contractors?
Penetration testing is crucial for federal and defense contractors to ensure compliance with stringent security regulations like NIST, DFARS, CMMC, and ITAR. It helps protect sensitive information and secures your systems against potential cyber threats.
How often should penetration testing be conducted?
For federal and defense contractors, it is recommended to conduct penetration testing at least annually or whenever significant changes are made to your IT infrastructure. Regular testing helps ensure ongoing security and compliance.
What types of penetration testing do you offer?
We provide a comprehensive range of penetration testing services tailored for federal and defense contractors, including Firewall Penetration Testing, Network Security Penetration Testing, Cloud Security Penetration Testing, Web Application Penetration Testing, Hardware and Embedded Systems Penetration Testing, Mobile Device Penetration Testing, Compliance-Focused Penetration Testing, Wireless Network Penetration Testing, Social Engineering Penetration Testing, Physical Penetration Testing, Red Teaming, SCADA/ICS Penetration Testing, and API Penetration Testing.
What is the difference between vulnerability scanning and penetration testing?
Vulnerability scanning identifies potential vulnerabilities in your systems, while penetration testing goes a step further by actively exploiting those vulnerabilities to determine their impact and risk.
How long does a penetration test take?
The duration of a penetration test varies depending on the scope and complexity of the systems being tested. Typically, tests can range from a few days to several weeks.
Will penetration testing disrupt my business operations?
Our penetration testing is designed to minimize disruption. We work with you to schedule testing during off-peak hours and take precautions to ensure that critical operations are not affected.
Is penetration testing required for CMMC compliance?
Yes, penetration testing is an essential component of achieving and maintaining CMMC compliance. It helps ensure that your cybersecurity practices meet the necessary standards.
How do you ensure the confidentiality of our data during testing?
We adhere to strict confidentiality agreements and employ secure testing methods to protect your data. Our team of certified professionals is trained to handle sensitive information with the utmost care.
Can penetration testing help with ITAR compliance?
Yes, penetration testing can help ensure that your systems meet ITAR compliance requirements by identifying and mitigating security vulnerabilities that could expose sensitive defense-related information.
What certifications do your penetration testers hold?
Our penetration testers hold industry-recognized certifications such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and Certified Information Systems Security Professional (CISSP).
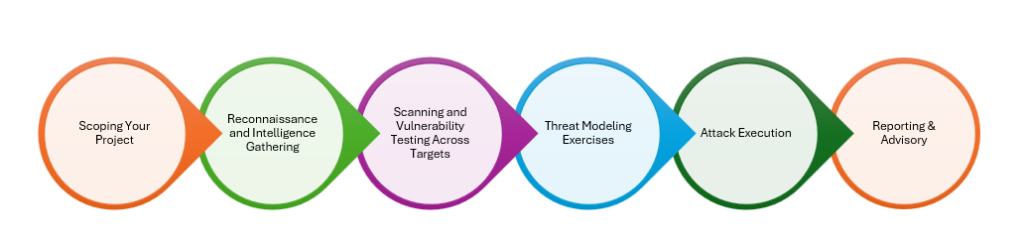
What are the Five Phases of the Penetration Testing
Penetration testing is based on five phases reconnaissance, scanning, vulnerability assessment, exploitation, and reporting.
Our Certifications





Partner with Us for Compliance & Protection
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Security
- Compliance
- Peace of mind
- Efficiency
- Trust
What happens next?
Schedule an initial meeting
Arrange a discovery and assessment call
Tailor a proposal and solution
