
What is DORA? Protecting the EU in 2025
DORA: In an era where digital threats pose significant risks to financial stability, the European Union has taken a decisive step to fortify its financial

DORA: In an era where digital threats pose significant risks to financial stability, the European Union has taken a decisive step to fortify its financial
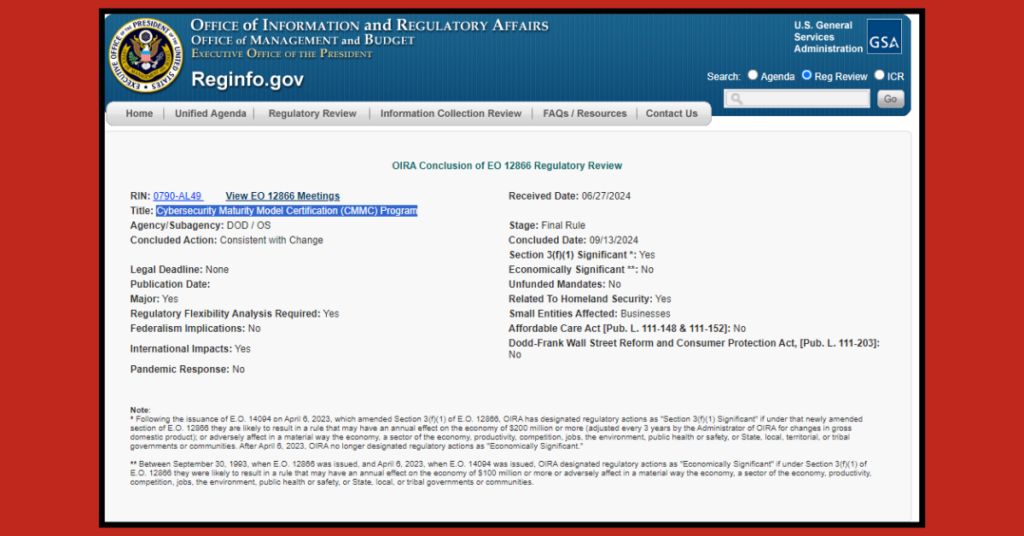
The Department of Defense’s (DoD) Cybersecurity Maturity Model Certification (CMMC) is rapidly moving forward, signaling significant changes for defense contractors. Two critical rules—one for the
In today’s complex cybersecurity landscape, federal contractors, the Defense Industrial Base (DIB), and defense manufacturers are constantly facing advanced threats targeting their networks and sensitive

In an increasingly digitized world, cybersecurity threats have become a paramount concern for businesses across all sectors and countries. One particularly insidious threat that has

Exporting weapons is a challenging and intricate process, one that we’ve seen firsthand through our work with various defense contractors. Over the years, we’ve guided

In the ever-evolving landscape of cyber security, safeguarding sensitive information is paramount. For organizations handling Controlled Unclassified Information (CUI), particularly those working with the U.S.

In the rapidly evolving digital landscape, cybersecurity is a top business priority. A Virtual Chief Information Security Officer (vCISO) is a high-level security professional who

In today’s digital landscape, where cyber threats are constantly evolving, ensuring the protection and security of sensitive information is critical. This is especially critical, considering

A manufacturer was looking to bid for an upcoming lucrative DoD contract. However, they had to pass the CMMC 2.0 level 2 assessment because the

An FPGA manufacturer’s basic cybersecurity efforts were spearheaded by their 2-man IT department. With growing security challenges and customers’ demand for privacy and protection, the
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Schedule an initial meeting
Arrange a discovery and assessment call
Tailor a proposal and solution