Blog
Resources, News, Industry Updates for Cybersecurity & Compliance Consulting for DoD Contractors
Is AutoCAD ITAR Compliant? A Comprehensive Guide for Defense Manufacturers
Defense contractors and manufacturers working with sensitive military technologies face a critical question when selecting computer-aided design software: Is AutoCAD ITAR compliant? This question becomes

Is AutoCAD ITAR Compliant? A Comprehensive Guide for Defense Manufacturers
Defense contractors and manufacturers working with sensitive military technologies face a critical question when selecting computer-aided design software: Is AutoCAD ITAR compliant? This question becomes

How to Get Help in Windows: Guide to Security and Compliance Support
In today’s digital landscape, ensuring your computer systems are secure and compliant with industry regulations is essential for both businesses and individuals. Windows, as one

Microsoft Copilot for GCC High: Enhancing Security and Compliance
In today’s fast-evolving digital landscape, organizations that handle sensitive data, particularly those in government sectors or defense contractors, face growing pressure to maintain strict security

ITAR Explained: Why It Matters for U.S. Companies
The International Traffic in Arms Regulations (ITAR) is a set of U.S. government regulations designed to control the export and import of defense-related articles and

What is DORA? Protecting the EU in 2025
DORA: In an era where digital threats pose significant risks to financial stability, the European Union has taken a decisive step to fortify its financial
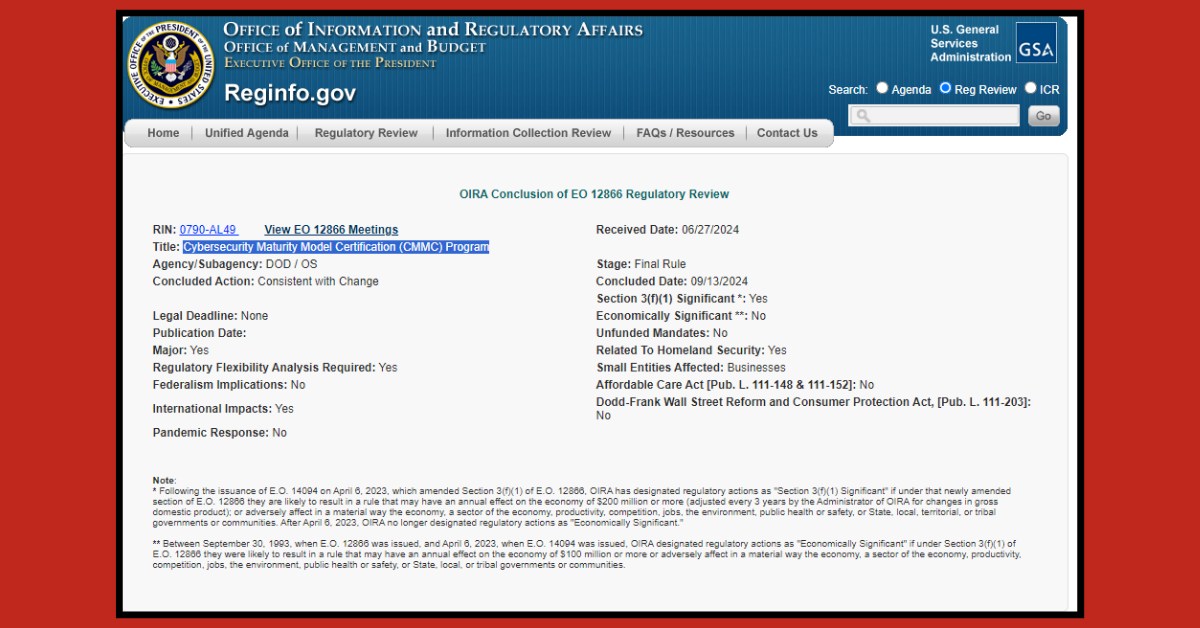
CMMC Program Updates: What You Need to Know and How to Avoid Snake Oil Salesmen
The Department of Defense’s (DoD) Cybersecurity Maturity Model Certification (CMMC) is rapidly moving forward, signaling significant changes for defense contractors. Two critical rules—one for the

How to Manage ITAR and EAR Export Compliance Program
In today’s globalized business environment, managing an effective export compliance program is crucial for companies dealing with sensitive technologies, defense articles, and controlled information. Two
Vulnerability Scanning vs. Penetration Testing: What’s the Difference?
In today’s complex cybersecurity landscape, federal contractors, the Defense Industrial Base (DIB), and defense manufacturers are constantly facing advanced threats targeting their networks and sensitive

LockBit Ransomware: A Critical Threat to Defense Manufacturing
In an increasingly digitized world, cybersecurity threats have become a paramount concern for businesses across all sectors and countries. One particularly insidious threat that has

How to Avoid Pitfalls in Weapon Exports
Exporting weapons is a challenging and intricate process, one that we’ve seen firsthand through our work with various defense contractors. Over the years, we’ve guided

DoD Releases A Memo Defining FedRAMP Moderate Equivalency
Members of the DoD supply chain that use Cloud Service Providers (CSP) to store, process, and transmit CUI/CDI must not only require but also ensure

CMMC Proposed Rule Is Finally Here!
On December 26th, 2023, the much-awaited proposed rule for the CMMC program was published on the Federal Register. The proposed rule establishes the requirements for

Elevate Your Aerospace Cybersecurity with vCISO Services
Ensure robust aerospace cybersecurity and regulatory compliance with strategic vCISO Services.
Partner with Us for Compliance & Protection
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Security
- Compliance
- Peace of mind
- Efficiency
- Trust
What happens next?
Schedule an initial meeting
Arrange a discovery and assessment call
Tailor a proposal and solution
