NIST SP 800-171 Assessment Template
Streamline Your NIST SP 800-171 Compliance with Our Assessment Template: A Comprehensive Guide to Evaluating and Enhancing Your Organization's Cybersecurity Posture
The DoD’s current cybersecurity regulations are specified in the Defense Federal Acquisition Regulation Supplement (DFARS), released in 2015. DFARS required the defense contractors handling Controlled Unclassified Information (CUI) to build resilient cybersecurity infrastructure following the 110 security controls specified by the National Institute of Technology and Standards Special Publication 800-171 (NIST SP 800-171) by the end of 2017.
NIST developed the security controls to specifically protect CUI. The DoD contractors have had the liberty to assess their compliance with NIST SP 800-171 themselves since 2017. However, the DoD released the DFARS Interim Rule 2019-D041 in late 2020. The Interim Rule requires that self-assessments be conducted, and the scores from the assessments are filed with the Department of Defense Supplier Performance Risk System (SPRS).
Although the clauses in the Interim Rule related to the implementation of the CMMC Framework were suspended upon the release of CMMC 2.0, DFARS 7019 that mandates contractors to report the scores remains in effect. The Interim Rule doesn’t specify the minimum scores a contractor can get in NIST SP 800-171 assessment. However, the DoD does a risk-based assessment in determining which organizations it will award contracts to.
If the self-assessment scores of an organization are low, then DoD will consider the organization a higher security risk than another organization having a better score. Similarly, prime contractors consider the self-assessment scores when evaluating the subcontractors, they will likely work with. Hence, it is only reasonable that the subcontractors that have a higher score will most likely win the bid.
Therefore, it is clear that raising your organization’s self-assessment score is essential. Given the importance and weight NIST SP 800-171 imposes on CUI protection, enhancing your company’s ability to protect it will improve your score quickly and effectively. CUI is normally shared or disseminated in the form of emails and files. Hence, implementing platforms that effectively protect email and file sharing will undoubtedly improve your scores. This post will serve as a definitive guide to NIST SP 800-171 assessment.
Determination Statements Versus Control Statements
DFARS 252.204-7012 and 32 CFR Part 2002 point to the NIST SP 800-171, the protection of Controlled Unclassified Information (CUI). The NIST Special Publication has about 113 pages with 14 domains having a total of 110 controls. But does it form the best guidance for self-evaluating each control’s implementation?
Every practice in NIST SP 800-171 features a control statement (in bold text) next to the control ID number. Besides describing the capabilities, the control systems also summarize what’s being done. However, they don’t provide a deep insight into how organizations can effectively implement the controls. For instance:
3.8.1 Protect(i.e., physically control and securely store) system media containing CUI, both paper and digital.
The control statement above isn’t clear even with the guidance contained in the discussion. Hence, it is hard to break the control down into finer components.
Discussion
System media includes digital and non-digital media. Digital media includes diskettes, magnetic tapes, external and removeable hard disk drives, flash drives, compact disks, and digital video disks. Non-digital media includes paper and microfilms. Protecting digital media includes limiting access to design specifications stored on compact disks or flash drives in the media library to the project leader and any individual on the development team. Physically controlling system media includes conducting inventories, maintaining accountability for stored media, and ensuring procedures are in place to allow individuals to check out and return media to the media library. Store storage includes a locked drawer, desk, or cabinet, or a controlled media library.
Access to CUI on system media can be limited by physically controlling such media, which includes conducting inventories, ensuring procedures are in place to allow individuals to check out and return media to the media library, and maintaining accountability for all stored media.
[SP 800-171] provides guidance on storage encryption technologies for end users devices.
Adapted from NIST SP 800-171 Rev 2
You could have difficulty trying to do a self-assessment of such control using NIST SP 800-171 only. To assess the implementation of controls, organizations can use NIST SP 800-171A. It’s the guide for assessing the implementation of NIST SP 800-171 controls. Though it isn’t referenced in the DFARS or CFR clauses, NIST points it out on the NIST SP 800-171 landing page.
NIST SP 800-171A expands on the 110 practices by creating 320 additional determination statements. The statements form more granular components of the control statements that an assessor will check during the evaluation of the practice. For instance, there are four determination statements from the aforementioned practice 3.8.1.
A keen inspection of the image below shows that the security requirement and the control statement adapted from NIST SP 800-171 Rev. 2 are the same. Then comes the assessment objective immediately below the security requirement that consists of 4 determination statements listed from [a] through to [d].
The assessor checks these statements for each practice. For an organization to effectively meet the security requirement, the determination statements should either be met or N/A for all assets within that scope. When self-assessing on any control, you must look at the determination statement as it acts like the reference authority.
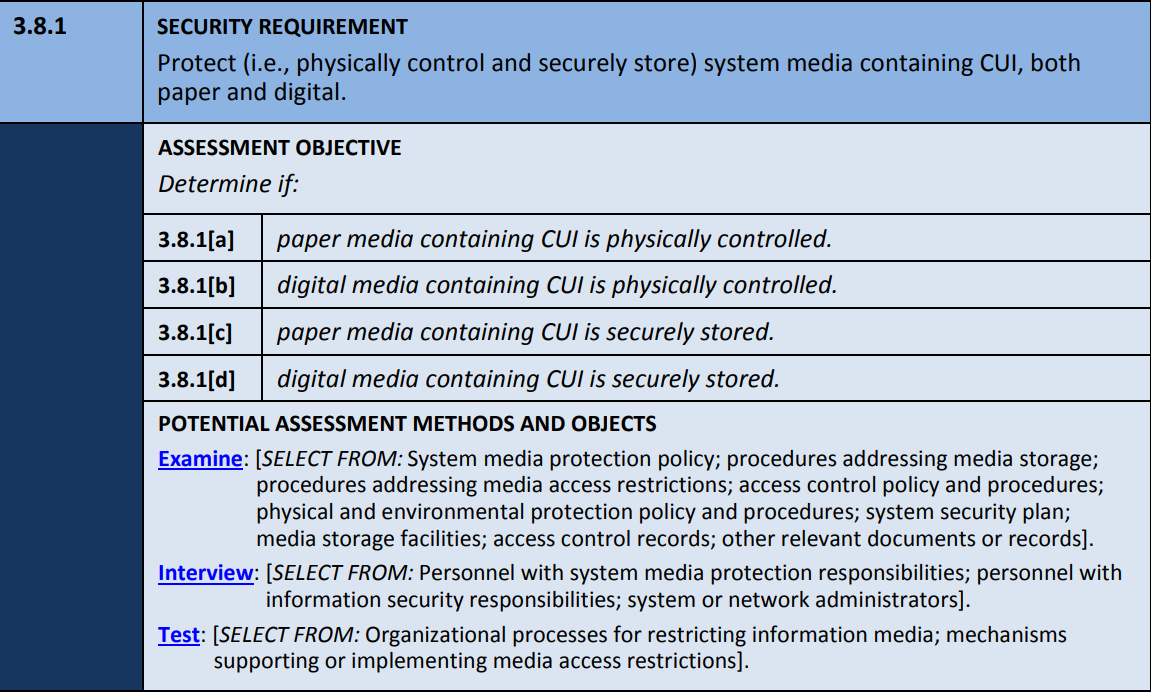
Adapted from NIST SP 800-171A
How Do I Determine the Scope of NIST SP 800-171?
Now that you understand what we need to implement, how these controls can be applied in your environment? The best place to start is the guidance under section 1.1 of NIST SP 800-171 Rev 2 (Purpose and Applicability): The second paragraph states as follows:
The requirements apply to components of non-federal systems that process, store, or transmit CUI, or that provide security protection for such components. If nonfederal organizations designate specific system components for the processing, storage, or transmission of CUI, those oraganizations may limit the scope of the security requirements by isolationg the designated system components in a separate CUI security domain. Isolation can achieved by applying architectural and design concepts (e.g., implementing subnetworks with firewalls or other boundary protection devices and using information flow control mechanisms). Security domains may employ physical separation, logical separation, or a combination of both. This approach can provide adequate security for the CUI and avoid increasing the organization’s security posture to a level beyond that which it requires for protecting its missions, operations, and assets.
Adapted from NIST SP 800-171 Rev 2
As you can see, the first sentence is pointing to reference 9, which states:
Assessment Objects
Section 1.1 of NIST SP 800-171 Rev 2 is an excellent start point that organizations could rely on to understand the scope of NIST SP 800-171. It also can be used as guidance on defining a boundary. separating the relevant and irrelevant things in NIST SP 800-171. NIST uses the term Assessment Objects to describe the objects within this boundary. But how does NIST Define assessment objects? NIST CRSC defines it as shown in the extract below:
Assessment objects identify the specific items being assessed, and as such, can have one or more security defects. Assessment objects include specifications, mechanisms, activities, and individuals which in turn may include, but are not limited to, devices, software products, software executables, credentials, accounts, account-privileges, things to which privileges are granted (including data and physical facilities), etc. See SP 800-53A.
Source(s):
NISTIR 8011 Vol. 1 under Object, Assessment
Adapted from NIST CSRC
As you can see, NIST SP 800-171 lists operating systems, computers, mainframes, servers, and applications as instances of information systems. However, physical facilities, individuals, and activities are also incorporated into the definition of an assessment object. Therefore, scope not only refers to assets (facilities, people, and technology) but incorporates processes and activities too. Assessment objects can be broadly categorized into:
CUI Assets
These are assets storing, transmitting, or processing Controlled Unclassified Information (CUI) and include technology, facilities, or even people that process, transmit, or store CUI.
Special Protection Assets
These are the assets providing security protection of the controlled unclassified information assets. These assets also include the technology, people, and facilities which provide security functions for the CUI Assets. However, security protection assets themselves don’t have to store, transmit, or even process CUI.
CUI Security Domains
As it can be noted, you now know that you should not only be looking for computers. When it comes to scope, there is more at play. The second part of the guidance above talks about security domains. However, organizations may create separate CUI security domains using logical separation, physical separation, or even a combination.
Physical Isolation
This arises whenever the CUI security domains aren’t connected (either via wireless or wired means). If systems aren’t connected, and the data transfer can only happen when there’s human interaction, these systems can be termed “air-gapped.”
Physical isolation involves separation of components, systems, and networks by hosting them on separate hardware. It may also include the use of specialized computing facilities and operational procedures to allow access to systems only by authorized personnel. In many situations, isolation objectives may be achieved by a combination of logical and physical isolation. Security architects and operational users must be cognizant of the co-dependencies between the logical and physical mechanisms and must ensure that their combination satisfies security and assurance objectives. A full discussion of isolation is beyond the scope of this appendix.
Adapted from NIST SP 800-160 v1
Logical Isolation
Logical isolation usually exists in a system through tools for controlling information flow. If a system is logically isolated, it connects to other systems but uses mechanisms for creating isolated processing environments.
Are NIST SP 800-171 and CMMC 2.0 Scopes the Same?
Are you are researching NIST SP 800-171? Your CUI might originate from a Department of Defense contract or might be preparing for a NIST SP 800-171 assessment by a third-party in your organization. CMMC Assessment Scope Level 2 Guide was released by the DoD in December 2021. Under CMMC 2.0 guidelines, organizations can be assessed for implementing NIST SP 800-171 controls by a certified assessor, or even do it themselves.
However, the division of contracts that will need an assessment by a third party versus those that won’t is yet to be known. The Department of Defense advised that it will relate back to the risk assessments conducted based on how critical to national security the CUI is. Organizations must use the Level 2 Scoping Guide because it clarifies the scope’s segmentation. The Special Protection Assets and CUI Assets discussed above in relation to NIST SP 800-171 are the same primary assets assessed in the CMMC.
However, there is a slight change in how Special Protection Assets are defined. NIST SP 800-171 defines Special Protection Assets in a manner that means they provide security functions to the CUI Assets. However, the Special Protection Assets also offer security functions for specialized and contractor risk-managed assets under the CMMC 2.0 guidance. But what do the two mean?
Contractor Risk-Managed Assets
These assets don’t need separation from the controlled unclassified information assets. They also aren’t intended to use procedure, policy, or even practice to handle CUI. Although they remain in CMMC 2.0 Assessment Scope, they have not assessed all the controls. These assets should be documented within the System Security Plan (SSP) in compliance with Control 3.12.4 of NIST SP 800-171 Rev 2.
Specialized Assets
These assets don’t need to be separated from CUI and some might even store, process, or even transmit it. Though they aren’t assessed against any other control besides 3.12.4, specialized assets remain a part of the CMMC assessment scope. They may be categorized into the Internet of Things (IoT), government property, test equipment, restricted information systems, and Operational Technology (OT).
Scoring Using the Supplier Performance Risk System (SPRS) Portal
The suppliers should conduct a NIST SP 800-171 assessment on their covered information systems as per DFARS Case 2019-D041. An accompanying scoring method reflects the net impact of not-yet-implemented requirements. The results uploaded on the SPRS verify that the supplier’s scores aren’t older than three years. To access the SPRS portal, you’ll need your Commercial and Government Entity (CAGE) Code and Procurement Integrated Enterprise Environment (PIEE).
You’ll be able to enter your assessment scores only if your organization follows the instructions provided under the SPRS quick entry guide. You can perform either of the assessment levels below:
- Basic: These are self-assessments completed by the supplying organization with a result of a low confidence level.
- Medium: The government reviews the SSP at this level, resulting in a medium confidence level.
- High: Here, the government does the assessment via a review of the evidence presented. Assessment under this level has a high confidence level
However, an organization can conduct an assessment under either of the following scopes:
- Contract: Contract Specific System Security Plan review.
- Enclave: As a standalone business unit within Enterprise CAGE
- Enterprise: The entire organization’s network is under the listed CAGEs
Organizations are only required to provide the summary level score that is also CUI. Hence, you should implement the necessary access restrictions.
As mentioned above, NIST SP 800-171 has 110 controls, meaning a perfect score would be 110 points. Each control is evaluated on a point scale (1, 3, and 5) in as listed in Annex A of the DoD Assessment Methodology. The scores indicate the control’s impact on an organization’s data or network security. If a control isn’t implemented, its score value is subtracted from 110. However, -203 is the lowest score, and any assessment is non-compliant with DFARS 252.204-7012 and incomplete without an SSP.
Controls That Have 5 Points
Forty-two of the NIST SP 800-171 Rev 2 controls have a 5-point score. Failing to implement these security requirements poses a significant risk of the DoD CUI exfiltration. Further, it is highly likely that the controls under this category are not eligible for the PoAMs under CMMC 2.0. Hence, work with a CMMC-certified assessor to implement these controls and assess where you are about your Plan of Action and Milestones. Below are the 42 controls:
| 3.1.1 | 3.2.1 | 3.4.6 | 3.6.2 | 3.10.2 | 3.13.6 |
| 3.1.2 | 3.2.2 | 3.4.7 | 3.7.2 | 3.11.2 | 3.13.15 |
| 3.1.12 | 3.3.1 | 3.4.8 | 3.7.5 | 3.12.1 | 3.14.1 |
| 3.1.13 | 3.3.5 | 3.5.1 | 3.8.3 | 3.12.3 | 3.14.2 |
| 3.1.16 | 3.4.1 | 3.5.2 | 3.8.7 | 3.13.1 | 3.14.3 |
| 3.1.17 | 3.4.2 | 3.5.10 | 3.9.2 | 3.13.2 | 3.14.4 |
| 3.1.18 | 3.4.5 | 3.6.1 | 3.10.1 | 3.13.5 | 3.14.6 |
Partially implementing the following two controls will mitigate their scoring impact:
- 3.5.3 Multi-Factor Authentication: If multi-factor authentication is implemented for the privileged and remote users but not for general use, 3 points should be subtracted. However, if MFA isn’t implemented completely (for any user), 5 points should be subtracted.
- 3.1.13 FIPS Validated Encryption: Whenever required, if using encryption that isn’t FIPS 140-1, 140-2, or validated, 3 points are subtracted. If required but not implemented, all 5 points are to be subtracted.
Controls That Have 3 Points
There is a total of 14 controls having a 3-point score, including:
| 3.1.5 | 3.3.2 | 3.7.4 | 3.8.2 | 3.8.8 | 3.12.2 | 3.14.5 |
| 3.1.19 | 3.7.1 | 3.8.1 | 3.9.1 | 3.11.1 | 3.13.8 | 3.14.7 |
Although control 3.12.4 has no points, any assessment without it is not compliant with DFARS 252.204-7012.
Controls That Have 1 Point
Therefore, 51 controls have a point each. Below is a summary of the controls and the number of points:
| Controls | 42 | 2 | 14 | 51 | 1 | 110 |
| Points Per Control | -5 | -5 or -3 | -3 | -1 | 0 | |
| Worst Score | -210 | -10 | -42 | -51 | 0 | -203 |
Having a PoAMs isn’t a substitute for a completed control/practice. Your organization can assess the controls as applied even when they feature some temporary deficiencies, provided they are addressed in the PoAMs. This may include those that need corrective actions but show significant progress towards the implementation. Though there isn’t any standard duration that the temporary deficiency should be addressed, ensure that you institute measures to resolve them within a reasonable period.Additionally, some controls might not be relevant to a supplier. For instance, if remote access isn’t allowed or required, the score practice 3.1.12 isn’t applicable or implemented, and no points should be deducted. However, a procedure or policy should still exist to ensure such capabilities aren’t enabled. Further, a supplier might receive determinations from DoD CIO that an alternate security measure has the same effectiveness as one within NIST SP 800-171. The organization should consider the security controls approved inapplicable via alternatives in such a case. As a supplier, ensure that you include any DoD CIO assessment in your SSP
What About NFO Controls?
Appendix E (Tailoring Criteria) of NIST SP 800-171 Rev 2 provides a list of FIPS 200 and NIST SP 800-53 Rev 4 controls. These controls aren’t part of NIST SP 800-171 assessment for either of the reasons below:
- NFOs should satisfy the controls without specification routinely.
- The control enhancement or control for CUI isn’t related to protecting its confidentiality.
- The control or even control enhancements are the federal government’s responsibility.
The phrase routinely satisfied …. without specification is supplemented by the cautionary note below:
… Organizations that are interested in or are required to comply with the recommendations in this publication are strongly advised to review the complete listing of controls in the moderate baseline in Appendix E to ensure that their individual security plans and control deployments provide the necessary and sufficient protection to address the cyber and kinetic threats to organizational missions and business operations.
Adapted from NIST SP 800-171 Rev 2
The rumor that CMMC 2.0 doesn’t need written policies and procedures was dispelled at a CMMC-AB Town Hall meeting on January 25th 2022. Matt Travis referenced Appendix E on his slide with the title CMMC Rumor Control, as illustrated below:
Adapted from cmmcab.org
Travis Provided his interpretation of Appendix Ein the Q&A session of that meeting. Though he believes that the NFO controls are in place, he also acknowledged that the Department of Defense should provide more elaboration. However, some provisional assessors believe that NFO controls aren’t in the scope. However, note that NIST has updated the NIST SP 800-54 Rev 4 to NIST SP 800-54 Rev 5. Some of the controls listed in appendix 5 were consolidated and moved in this update.
For instance, the following were the contents of NFO control CM-2(1) within NIST SP 800-53 Rev 4
(1) BASELINE CONFIGURATION | REVIEWS AND UPDATES
The organization reviews and updates the baseline configuration of the information system:
- (a) [Assignment: organization-defined frequency];
- (b) When required due to [Assignment organization-defined circumstances]; and
- (c) As an integral part of information system component installations and upgrades.
Supplemental Guidance: Related control: CM-5.
Adapted from NIST SP 800-53 Rev 4
This control was removed in NIST SP 800-54 Rev 5 and subsequently moved to CM-2, which states:
CM-2 BASELINE CONFIGURATION
Control:
- a. Develop, document, and maintain under configuration control, a current baseline
configuration of the system; and - b. Review and update the baseline configuration of the system:
- 1. [Assignment: organization-defined frequency];
- 2. When required due to [Assignment: organization-defined circumstances]; and
- 3. When system components are installed or upgraded.
Adapted from NIST SP 800-53 Rev 5
As indicated below, this control has already been mapped to the control 3.4.1 & 3.4.2 in table D of NIST SP 800-171.
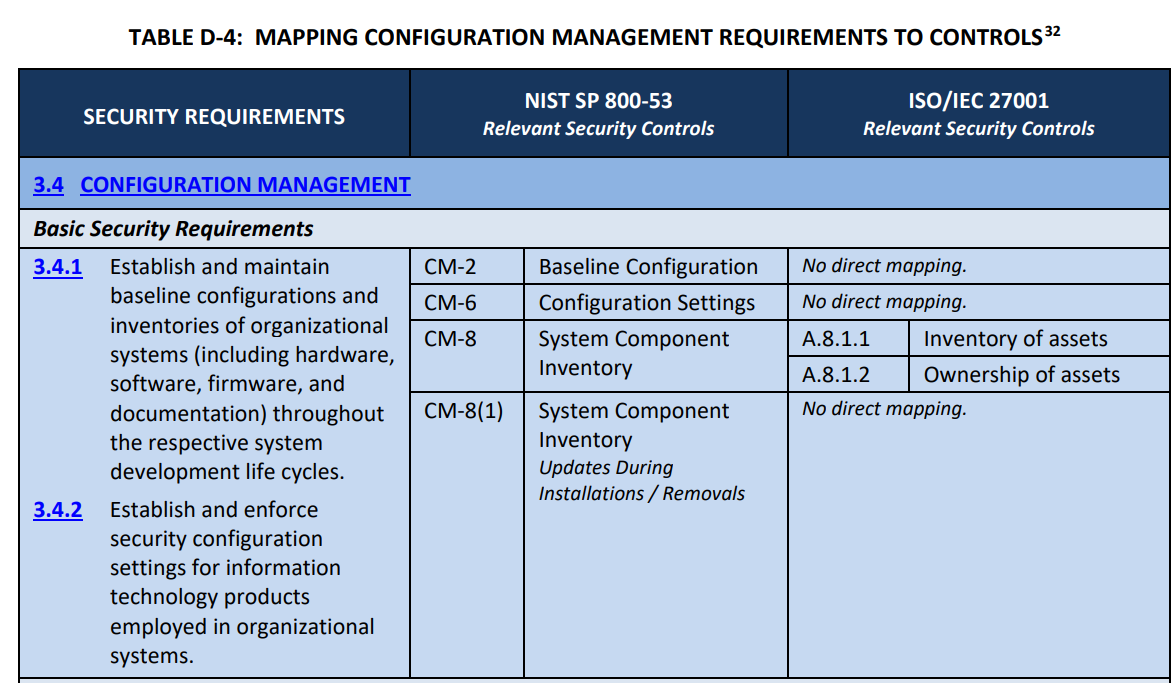
Adapted from NIST SP 800-171 Rev 2
The following 6 NFO controls have been removed through similar updates.
| NIST SP 800-54 Rev 4 NFO Control | New NIST SP 800-54 Rev 5 Control | Mapping to NIST 800-171 |
| CA-3(5) | SC-7(5) | 3.13.6 |
| CM-2(1) | CM-2 | 3.4.1 & 3.4.2 |
| CM-8(5) | CM-8 | 3.4.1 & 3.4.2 |
| RA-5(1) | RA-5 | 3.11.2 & 3.11.3 |
| PL-2(3) | PL-2 | 3.12.1, 3.12.2, 3.12.3 & 3.12.4 |
| MA-4(2) | MA-4 | 3.7.5 |
MA-4(2) is divided into MA-1 and MA-4 in NIST SP 800-53 Rev 5
(2) NONLOCAL MAINTENANCE | DOCUMENT NONLOCAL MAINTENANCE
[Withdrawn: Incorporated into MA-1 and MA-4.]
Adapted from NIST SP 800-53 Rev 5
MA-4 maps to 3.7.5 according to the NIST SP 800-171, although MA-1 is already an NFO control.
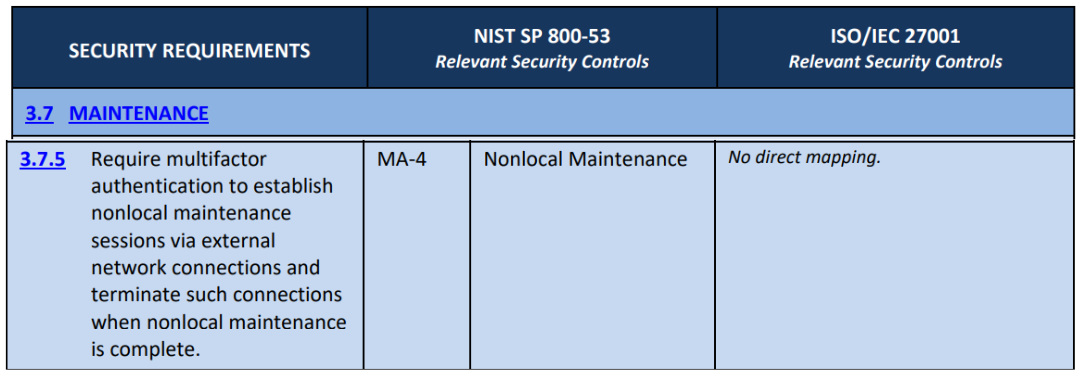
Adapted from NIST SP 800-171 Rev 2
Appendix E of the NIST SP 800-171 had 61 NFO controls. After a review of updates from the controls within NIST SP 800-53 Rev 5, 6 can be removed, meaning there is a total of 55 controls. The remaining controls have determination statements found in NIST SP 800-53A Rev 5.
Besides the determination statements, organizational-defined parameters are also used in NIST SP 800-53A. The ODPs can assign select operations or defined values from the provided options. Below is a summary of NFO controls, the corresponding number of ODPs, and the determination statements.
How About Delta 20 Controls?
These are the 20 more controls added to NIST SP 800-171 during the lunch of CMMC. However, these 20 additional requirements were removed with the introduction of CMMC 2.0, which brought the controls back in tandem with NIST SP 800-171. But this does not mean that organizations should not fully consider the controls. Reviewing them and determining whether they need an implementation has some value.
NIST SP 800-171 primarily focuses on protecting the integrity and confidentiality of CUI. Some delta practices, like those in the recovery domain, address information availability. However, the development of other practices like the implementation of the advanced email protections within SI.3.219 and SI.3.218 was necessitated by new threats. There are reports that NIST has plans to update NIST SP 800-171 Rev 2. Based on the progress in CMMC 2.0 rulemaking, Revision 3 is likely to occur before CMMC is implemented. Hence, NIST expected to incorporate all or some of Delta 20 controls into the third revision of SP 800-171.
Conclusion
Any good NIST SP 800-171 assessment template should scope the security protection assets, processes, people, facilities and information systems. It should also consider the NFO controls and Delta 20 controls because NIST might incorporate them in the next revision of NIST SP 800-171. These are some of the items any useful template should include. However, developing a properly refined template that you can use to self-assess is tiring and tedious. To ensure that you develop a solid one, work with a certified RPO or CMMC assessor.
At Cleared Systems, our expert RPs have over 20 years of experience in NIST SP 800-171 consulting. We can help you draw a template that will help you effectively calculate your SPRS scores and submit them to DoD. We will also help you implement the NIST controls to ensure that your organization gets better scores, meaning that you’ll be in a better position to win DoD contracts. Alternatively, you can use our readymade template to self-assess. For NIST SP 800-171 consulting and assessment, contact us today.
Share in Social Media
See More Case Studies

Securing Defense Contracts: A DFARS 252.204-7012 Compliance Case Study
Discover how Cleared Systems helped a Federal Contractor successfully achieve DFARS 252.204-7012 compliance by strengthening its cybersecurity posture, giving it a competitive edge when bidding for DoD Contracts.

What is GCC High? For ITAR & CMMC 2.0
Microsoft 365 Government Community Cloud (GCC) High is a specialized cloud solution tailored for U.S. federal, state, local, tribal, and territorial government organizations, as well as for contractors who hold or process data subject to specific security regulations. In this article, we will explore the features, benefits, and differences between Microsoft 365 GCC High and other Office 365 offerings.

Is AutoCAD ITAR Compliant? A Comprehensive Guide for Defense Manufacturers
Defense contractors and manufacturers working with sensitive military technologies face a critical question when selecting computer-aided design software: Is AutoCAD ITAR compliant? This question becomes

How to Get Help in Windows: Guide to Security and Compliance Support
In today’s digital landscape, ensuring your computer systems are secure and compliant with industry regulations is essential for both businesses and individuals. Windows, as one

Microsoft Copilot for GCC High: Enhancing Security and Compliance
In today’s fast-evolving digital landscape, organizations that handle sensitive data, particularly those in government sectors or defense contractors, face growing pressure to maintain strict security
Partner with Us for Compliance & Protection
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Security
- Compliance
- Peace of mind
- Efficiency
- Trust
What happens next?
Schedule an initial meeting
Arrange a discovery and assessment call
Tailor a proposal and solution
