What You Should Know About CMMC 2.0 Level 3
The Cybersecurity Maturity Model Certification (CMMC) is a set of cybersecurity standards developed by the United States Department of Defense (DoD) to ensure that companies that work with the government have adequate cybersecurity measures in place. CMMC 2.0 Level 3 is the third level of certification in the CMMC model and is designed for companies that handle Controlled Unclassified Information (CUI) that is critical to the mission of the DoD. In this article, we will discuss the basics of CMMC Level 3 and what you need to know to achieve compliance.
What is CMMC Level 3
CMMC Level 3 is the third level of certification in the CMMC model. It is designed for companies that handle Controlled Unclassified Information (CUI) that is critical to the mission of the DoD. CMMC Level 3 requires the implementation of 130 cybersecurity practices. These practices are based on the requirements of the National Institute of Standards and Technology (NIST) Special Publication 800-172.
CMMC Level 3 Security Requirements
CMMC Level 3 is the highest level of cybersecurity or digital hygiene an organization can achieve. It focuses on the effectiveness of cybersecurity practices and controls around protecting CUI from Advanced Persistent Threats (APTs). To achieve Certification at this maturity level, the OSC must achieve a CMMC Level 2 Final Certification assessment on the Level 3 CMMC Assessment Scope and implement the 24 security requirements specified in the proposed rule. These security requirements are selected from NIST SP 800-172, and at times, Organizational-Defined Parameters are defined where applicable. Below are the CMMC 2.0 Level 3 Certification Assessment security requirements with the DoD ODPs italicized. The table is an adaptation of TABLE 1 TO § 170.14(c)(4) in the CMMC proposed rule
Restrict access to systems and system components to only those information resources that are owned, provisioned, or issued by the organization.
Provide awareness training upon initial hire, following a significant cyber event, and at least annually, focused on recognizing and responding to threats from social engineering, advanced persistent threat actors, breaches, and suspicious behaviors; update the training at least annually or when there are significant changes to the threat
Establish and maintain an authoritative source and repository to provide a trusted source and accountability for approved and implemented system components.
Employ automated discovery and management tools to maintain an up-to-date, complete, accurate, and readily available inventory of system components.
Employ automated or manual/procedural mechanisms to prohibit system components from connecting to organizational systems unless the components are known, authenticated, in a properly configured state, or in a trust profile.
Establish and maintain a security operations center capability that operates 24/7, with allowance for remote/on-call staff.
Employ threat intelligence, at a minimum from open or commercial sources, and any DoD-provided sources, as part of a risk assessment to guide and inform the development of organizational systems, security architectures, selection of security solutions, monitoring, threat hunting, and response and recovery activities.
Conduct cyber threat hunting activities on an on-going aperiodic basis or when indications warrant, to search for indicators of compromise in organizational systems and detect, track, and disrupt threats that evade existing controls.
Assess the effectiveness of security solutions at least annually or upon receipt of relevant cyber threat information, or in response to a relevant cyber incident, to address anticipated risk to organizational systems and the organization based on current and accumulated threat intelligence.
Assess, respond to, and monitor supply chain risks associated with organizational systems and system components.
Employ physical isolation techniques or logical isolation techniques or both in organizational systems and system components.
Develop a plan for managing supply chain risks associated with organizational systems and system components; update the plan at least annually, and upon receipt of relevant cyber threat information, or in response to a relevant cyber incident.
Ensure that Specialized Assets including IoT, IIoT, OT, GFE, Restricted Information Systems, and test equipment are included in the scope of the specified enhanced security requirements or are segregated in purpose-specific networks.
Employ secure information transfer solutions to control information flows between security domains on con-nected systems.
Include practical exercises in awareness training for all users, tailored by roles, to include general users, users with specialized roles, and privileged users, that are aligned with current threat scenarios and provide feed- back to individuals involved in the training and their supervisors.
Employ automated mechanisms to detect misconfigured or unauthorized system components; after detection, remove the components or place the components in a quarantine or remediation network to facilitate patching, re-configuration, or other mitigations.
Identify and authenticate systems and system components, where possible, before establishing a network connection using bidirectional authentication that is cryptographically based and replay resistant.
Establish and maintain a cyber-incident response team that can be deployed by the organization within 24 hours.
Ensure that organizational systems are protected if adverse information develops or is obtained about individuals with access to CUI.
Employ advanced automation and analytics capabilities in support of analysts to predict and identify risks to organizations, systems, and system components.
Document or reference in the system security plan the security solution selected, the rationale for the security solution, and the risk determination.
Conduct penetration testing at least annually or when significant security changes are made to the system, leveraging automated scanning tools and ad hoc tests using subject matter experts.
Verify the integrity of security critical and essential software using root of trust mechanisms or cryptographic signatures.
Use threat indicator information and effective mitigations obtained from, at a minimum, open or commercial sources, and any DoD-provided sources, to guide and inform intrusion detection and threat hunting.
CMMC 2.0 Level 3 Scoping
Scoping is critical before embarking on a CMMC level 3 assessment. It helps identify the assets that are subject to CMMC Level 3 Security Requirements. However, if the OSC uses an ESP (External Service Provider) other than a CSP (Cloud Service Provider), the ESP must have its own CMMC Level 3 Final Certification Assessment. If the ESP is an internal entity within the OSC, the OSC’s SSP should enumerate the security requirements implemented by the ESP to demonstrate the connection within its in-scope environment. Within the CMMC Program, CUI or Security Protection Data, such as log data and configuration data, must be processed, stored, or transmitted on the ESP assets in order to be considered part of the ESP.
Under § 170.18(c)(5) of the rule, an OSC may use a FedRAMP Moderate (or higher) cloud environment to process, store, or transmit CUI for a CMMC Level 3 contract if:
- The CSP is FedRAMP Authorized per the FedRAMP Marketplace;
- The CSP is not FedRAMP Authorized but meets equivalent security requirements as evidenced by the CSP’s SSP, security documentation, and CRM mapping to NIST SP 800-171 Rev 2.
- Per § 170.19, the OSC’s on-premises infrastructure connecting to the CSP is part of the CMMC Assessment Scope, so related security requirements from the CRM must be in the OSC’s SSP.
The table below shows the CMMC Level 3 in-scope and out-of-scope assets.
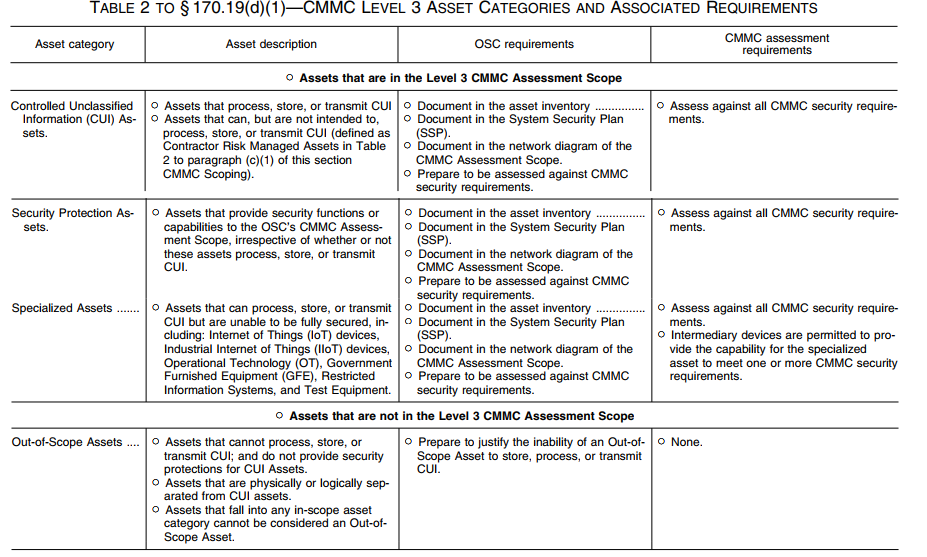
CMMC Level 3 Certification Assessment and Affirmation Requirements
Certification Assessment
Before initiating a CMMC 2.0 Level 3 Certification Assessment, the OSC should first achieve a CMMC Level 2 Final Certification Assessment on the Level 3 CMMC Assessment Scope. Additionally, such an organization must complete and implement the Level 3 security requirements. Only after an organization meets these requirements should it contact DCMA DIBCAC for a CMMC Level 3 Certification Assessment. However, Certification is not a one-time thing. Organizations are expected to maintain the cybersecurity maturity to protect critical CUI. To this end, the organization must achieve CMMC Level 3 Final Certification Assessment in line with § 170.18 and CMMC Level 2 Final Certification in accordance with § 170.18 of the proposed rule. All the information systems within CMMC Level 3 Assessment Scope will undergo triennial assessment. After an Assessment, the results are submitted to the CMMC instantiation of eMASS by the DCMA DIBCAC. The eMASS instantiation then offers an automated transmission into the SPRS.
The assessment results input into the CMMC instantiation of eMASS includes, at a minimum, the following items:
- The date and level of the assessment.
- Name and business contact information for each Assessor(s) conducting the assessment.
- All industry CAGE code(s) associated with the information system(s) covered by the CMMC Assessment Scope.
- The name, date, and version of the system security plan(s) (SSP).
- Results for each security requirement objective.
- Certification date
- Usage and compliance of the POA&M, as applicable.
- A list of artifact names, along with the return values of the hashing algorithm and the hashing algorithm used.
CMMC Level 3 Assessment Scoring
The scoring system for CMMC Level 3 differs from CMMC Level 2 by assigning a uniform value of ‘1’ point to each security requirement MET. Consequently, the maximum attainable score for CMMC 2.0 Level 3 corresponds to the total number of its security requirements. This maximum score is then decreased by one point for every security requirement that is NOT MET. Notably, the scoring approach acknowledges that all CMMC Level 2 security requirements must already be satisfied within the Level 3 CMMC Assessment Scope. Achieving the maximum score in a CMMC Level 2 assessment is a prerequisite for qualifying to undergo a CMMC Level 3 Certification Assessment. The CMMC Level 3 assessment score is determined by the number of security requirements at Level 3 that are successfully MET.
Conditional Certification
CMMC 2.0 Level 3 also allows for the use of time-limited POA&Ms. If a POA&M exists after the DCMA DICAC completes the assessment, and it meets all the POA&M requirements for CMMC Level 3 (§ 170.21(a)(3) of the proposed rule), then an OSC may be granted a CMMC Level 3 Conditional Certification Assessment. Section 170.21(a)(3) outlines the requirements for a POA&M for the purposes of a CMMC 2.0 Level 3 Assessment. For a POA&M to be allowed, the following conditions must be met:
- The assessment score as a percentage of the total number of CMMC Level 3 security requirements met or exceeded 80%, and
- The following security requirements aren’t included in the POA&M:
- IR.L3–3.6.1e Security Operations Center.
- IR.L3–3.6.2e Cyber Incident Response Team.
- RA.L3–3.11.1e Threat-Informed Risk Assessment.
- RA.L3–3.11.6e Supply Chain Risk Response.
- RA.L3–3.11.7e Supply Chain Risk Plan.
- RA.L3–3.11.4e Security Solution Rationale.
- SI.L3–3.14.3e Specialized Asset Security.
POA&M Closeout
POA&Ms aren’t a short path to CMMC 2.0 Level 3 Certification. While they can help an OSC become conditionally certified, the organization has a maximum of 180 days to remediate any practices in the POA&M document. After the OSC remediates any deficiencies, they should have DCMA DIBCAC conduct a POAM closeout assessment. After a successful POA&M closeout, the results are transmitted to the SPRS via the CMMC instantiation of eMASS. Failure to close out the POA&M within the stipulated 180 days results in the expiration of the Conditional Level 3 Certification. So, what happens if the Level 3 Conditional Certification expires during the contract’s performance period? Normal contractual remedies apply. For instance, the OSC loses eligibility for additional awards requiring Level 3 certification assessment criteria for all its information systems covered by the CMMC assessment scope. The organization must provide an affirmation attesting that they have closed out the POA&M.
Final Certification
Upon implementing all CMMC 2.0 Level 3 security requirements and closing out any POA&M, the OSC is granted a Final Certification Assessment for all its information systems within the CMMC Level 3 Assessment Scope. However, the organization must continually ensure that all the security requirements are met throughout the contract period. The Affirming Official must submit a CMMC Level 3 Affirmation annually after completion of the DCMA DIBCAC Assessment. The affirmation attests that the organization has taken up measures to ensure continued compliance with all the Level 3 requirements. However, this doesn’t mean that an organization shouldn’t submit CMMC Level 2 affirmations. Both are required.
CMMC Status Revocation
Can CMMC status be revoked even after attaining final Certification? Yes, the CMMC PMO has the discretion to revoke the validity status of the CMMC 2.0 Level 3 Final Certification Assessment. This is if they determine that an organization hasn’t met or maintained various provisions. The Standard contractual remedies discussed above will apply in this instance. It is worth noting that if an organization’s CMMC Level 2 Final Certification Assessment is revoked, that will result in an automatic revocation of its CMMC Level 3 Certification Assessment, particularly those reliant on the Level 2 Final Certification Assessment.
Does CMMC 2.0 Level 3 Certification Assessment Apply to Subcontractors?
Depends. Subcontractors that process, store, or transmit CUI in the execution of a contract should have a Level 2 Certification Assessment at a minimum if the prime is required to achieve a Level 3 certification assessment.
Conclusion
CMMC Level 3 is a higher level of certification than Level 2, and it is designed for companies that handle Controlled Unclassified Information (CUI) that is critical to the mission of the DoD. Compliance with CMMC Level 3 requires the implementation of 130 cybersecurity practices. Companies can achieve compliance by identifying the scope of the system that requires compliance, performing a self-assessment, identifying any gaps and deficiencies, developing a plan to address them, implementing the plan, obtaining a third-party assessment, and uploading the assessment results to the DoD’s SPRS. Achieving compliance with CMMC Level 3 is a significant step towards ensuring the security of the nation’s critical infrastructure and protecting sensitive government information.
Share in Social Media
See More Case Studies

Securing Defense Contracts: A DFARS 252.204-7012 Compliance Case Study
Discover how Cleared Systems helped a Federal Contractor successfully achieve DFARS 252.204-7012 compliance by strengthening its cybersecurity posture, giving it a competitive edge when bidding for DoD Contracts.

What is GCC High? For ITAR & CMMC 2.0
Microsoft 365 Government Community Cloud (GCC) High is a specialized cloud solution tailored for U.S. federal, state, local, tribal, and territorial government organizations, as well as for contractors who hold or process data subject to specific security regulations. In this article, we will explore the features, benefits, and differences between Microsoft 365 GCC High and other Office 365 offerings.

Is AutoCAD ITAR Compliant? A Comprehensive Guide for Defense Manufacturers
Defense contractors and manufacturers working with sensitive military technologies face a critical question when selecting computer-aided design software: Is AutoCAD ITAR compliant? This question becomes

How to Get Help in Windows: Guide to Security and Compliance Support
In today’s digital landscape, ensuring your computer systems are secure and compliant with industry regulations is essential for both businesses and individuals. Windows, as one

Microsoft Copilot for GCC High: Enhancing Security and Compliance
In today’s fast-evolving digital landscape, organizations that handle sensitive data, particularly those in government sectors or defense contractors, face growing pressure to maintain strict security
Partner with Us for Compliance & Protection
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Security
- Compliance
- Peace of mind
- Efficiency
- Trust
What happens next?
Schedule an initial meeting
Arrange a discovery and assessment call
Tailor a proposal and solution
