Understanding CMMC 2.0 Level 1
The DoD has implemented the Cybersecurity Maturity Model Certification (CMMC) to ensure that companies working with sensitive government information have adequate cybersecurity practices in place. CMMC establishes a framework of security controls and processes that organizations must meet to protect CUI and FCI. FCI refers to sensitive data related to government contracts that is not intended for public release. CUI encompasses information that requires security measures under federal laws and policies. CMMC 2.0 defines three maturity levels that represent increasingly sophisticated cybersecurity capabilities. Organizations can pursue certification at the Foundational, Advanced, or Expert level depending on their needs. By obtaining CMMC certification, companies demonstrate that they can properly safeguard government information and reduce cybersecurity risks. This article provides an overview of CMMC 2.0 Level 1, the basic Foundational tier of certification. We will examine the security requirements and controls that organizations must implement to achieve Level 1 compliance.
Understanding CMMC 2.0 Level 1
“CMMC 2.0 Level 1,” also called the “foundational level,” is the first stage of the three-tiered cybersecurity maturity model certification (CMMC). It is designed to address common cyber threats by implementing fundamental cybersecurity and risk management practices. CMMC Level 1 focuses on establishing basic security measures such as access control and authentication, which determine the accessibility of information. This Level is characterized by 17 distinct practices encompassing areas like Asset Management, Media Protection, Security Assessment and authorization, Identification and authentication, and System and Communication Protection. To achieve this Level of certification, organizations must demonstrate the successful implementation of these practices and exhibit efficient cybersecurity risk management processes.
What are CMMC Level 1 Security Controls?
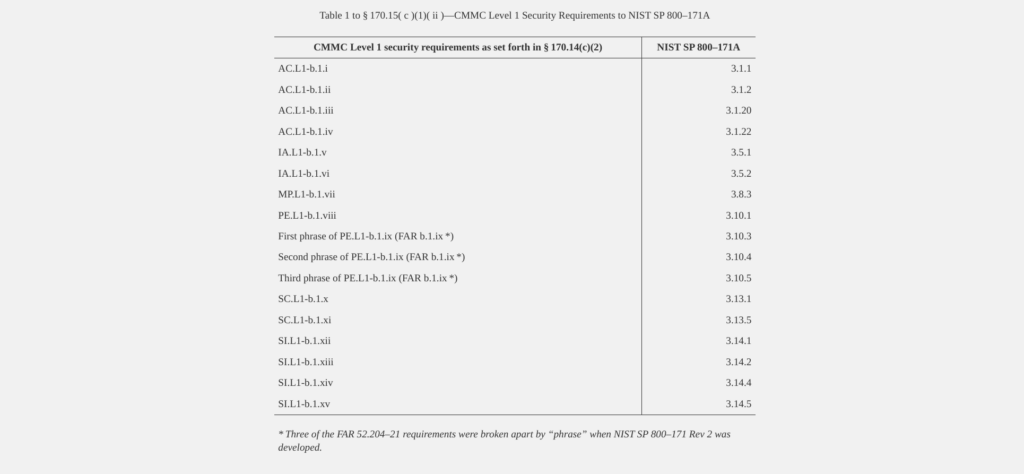
CMMC 2.0 Level 1 applies to any DoD contractor or subcontractor handling Federal Contract Information (FCI). Any organization that deals with FCI must achieve ‘Basic Cyber Hygiene” by implementing the security requirements set forth in FAR clause 52.204–21(b)(1)(i) through (b)(1)(xv). These requirements are detailed and discussed in the CMMC Assessment Guide – Level 1 Version 2.11. Before any contract or subcontract with a “CMMC 2.0 Level 1” requirement can be awarded, the OSAs must meet all the stipulated self-assessment requirements. Additionally, they must submit a compliance affirmation to the SPRS for all information systems that fall within the scope of the CMMC assessment. Since adhering to Level 1 security requirements isn’t a one-time activity, contractors must regularly review their information systems for vulnerabilities and assess risks they may pose. Below is a tabular representation of CMMC Level 1 security requirements.
CMMC 2.0 Level 1 Scoping
The CMMC Level 1 Self-Assessment requires the OSA to define the CMMC Assessment Scope, which outlines the assets within the OSA’s environment that will be evaluated. The assets in scope are those that process, store, or transmit Federal Contract Information (FCI). This includes assets that use FCI (accessed, entered, edited, generated, manipulated, or printed), store FCI (inactive or at rest on an asset), and transmit FCI (transferred from one asset to another). These assets are assessed against all CMMC Level 1 requirements.
Assets that do not process, store, or transmit FCI are considered outside the scope for the CMMC Level 1 Self-Assessment and are not part of the assessment. There are no documentation requirements for these Out-of-Scope Assets. Specialized Assets, which can process, store, or transmit FCI but are unable to be fully secured, are also not part of the Level 1 CMMC Self-Assessment Scope and are not assessed against CMMC requirements. These include Internet of Things (IoT) devices, Industrial Internet of Things (IIoT) devices, Operational Technology (OT), Government Furnished Equipment (GFE), Restricted Information Systems, and Test Equipment.
CMMC Level 1 Self-Assessments
This CMMC Level doesn’t require third-party assessments. This means that an OSA can conduct self-assessments on its information systems and in-scope assets itself. However, the OSA must meet some conditions to be compliant with CMMC Level 1 requirements. It must complete all the security requirements specified in the table above with a MET result. This Level doesn’t allow for the use of time limited POA&M, meaning an OSA cannot achieve conditional compliance. Additionally, CMMC 2.0 Level 1 assessments must be conducted in accordance with the scoping requirements described above. Security requirements scored in accordance with stipulations set out in § 170.24 of the proposed rule.
Self-Assessments for CMMC Level 1 compliance must be conducted using objectives defined in NIST SP 800–171A. However, compliance cannot be a one-time thing. Thus, OSAs are required to conduct CMMC Level 1 Self-Assessments annually and upload the findings in SPRS. At a minimum, the OSA should include the following in the results uploaded to the SPRS:
- CMMC Level.
- Date of the Assessment
- Assessment Scope.
- All industry CAGE code(s) associated with the information system(s) addressed by the CMMC Assessment Scope
- Compliance result.
For all “CMMC 2.0 Level 1” Self-Assessments, affirmations are mandatory. The OSA’s Affirming Official must “at the completion of a Self-Assessment and annually after that,” submit a CMMC Affirmation. The affirmation attests to the OSA’s continuing compliance with all security requirements for CMMC Level 1.
CMMC 2.0 Level 1 POA&M and Scoring Methodology
For CMMC Level 1 Self-Assessments, the use of a Plan of Action & Milestones (POA&M) is not allowed. Every security requirement under CMMC Level 1 must be fully implemented for the assessment to be considered MET. The results of the self-assessment are evaluated as either fulfilled (MET) or not fulfilled (NOT MET), with no partial scores or scoring methodology involved. Therefore, there’s no need for a scoring system at this maturity level.
Can an OSA’s CMMC Level 1 Status be Revoked?
YES. If there are indications that an active CMMC Level 1 Self-Assessment is questionable, the CMMC PMO may start investigative evaluations. Should the results of the investigation uncover that CMMC Level 1 provisions haven’t been achieved or maintained, the CMMC PMO can revoke the validity status of that Self-Assessment. Such a revocation triggers standard contractual remedies, meaning the OSA won’t be eligible for any additional contracts with CMMC Level 1 self-assessment or higher requirements. This applies to all the information systems that fall within the CMMC Assessment Scope and remains until a valid CMMC Level 1 Self-Assessment is achieved.
Conclusion
In conclusion, the Cybersecurity Maturity Model Certification (CMMC) 2.0 Level 1 is a crucial first step in safeguarding sensitive government information. It establishes a foundation of basic security measures and practices that organizations must implement to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). Achieving this level of certification demonstrates an organization’s commitment to cybersecurity and risk management. For further assistance in navigating the complexities of CMMC 2.0 Level 1 and ensuring your organization meets all necessary requirements, consider reaching out to Cleared Systems, a trusted partner in cybersecurity compliance.
Share in Social Media
See More Case Studies

Securing Defense Contracts: A DFARS 252.204-7012 Compliance Case Study
Discover how Cleared Systems helped a Federal Contractor successfully achieve DFARS 252.204-7012 compliance by strengthening its cybersecurity posture, giving it a competitive edge when bidding for DoD Contracts.

What is GCC High? For ITAR & CMMC 2.0
Microsoft 365 Government Community Cloud (GCC) High is a specialized cloud solution tailored for U.S. federal, state, local, tribal, and territorial government organizations, as well as for contractors who hold or process data subject to specific security regulations. In this article, we will explore the features, benefits, and differences between Microsoft 365 GCC High and other Office 365 offerings.

Is AutoCAD ITAR Compliant? A Comprehensive Guide for Defense Manufacturers
Defense contractors and manufacturers working with sensitive military technologies face a critical question when selecting computer-aided design software: Is AutoCAD ITAR compliant? This question becomes

How to Get Help in Windows: Guide to Security and Compliance Support
In today’s digital landscape, ensuring your computer systems are secure and compliant with industry regulations is essential for both businesses and individuals. Windows, as one

Microsoft Copilot for GCC High: Enhancing Security and Compliance
In today’s fast-evolving digital landscape, organizations that handle sensitive data, particularly those in government sectors or defense contractors, face growing pressure to maintain strict security
Partner with Us for Compliance & Protection
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Security
- Compliance
- Peace of mind
- Efficiency
- Trust
What happens next?
Schedule an initial meeting
Arrange a discovery and assessment call
Tailor a proposal and solution
