What is Cybersecurity Risk Management
In today’s hyper-connected world, organizations of all sizes operate within a complex digital landscape teeming with opportunities and, unfortunately, vulnerabilities. This interconnectedness reveals one uncomfortable truth about cybersecurity risk management — managing cyber risks across enterprises is now harder than ever. Today, keeping systems and architectures compliant and secure is an overwhelming task, even for the most skilled teams. Although managing cyber risk is increasingly challenging, it’s never been more crucial.
But what makes managing cyber risk more challenging today than it ever was?
This can be attributed to many factors. Take the unprecedented increase in third-party vendors and cloud services handling sensitive data, for instance. A study by the Ponem Institute revealed that an average company shares confidential information with 583 third parties — and 82% of companies provide those third parties access to their sensitive data. Thus, cyber security teams have the daunting task of managing complex systems and infrastructures rife with vendor risk.
Working from home or remotely on scrambled security protocols and unsecured networks broadens the attack surface, creating numerous potential entry points for cyber threats. Additionally, securing personal devices becomes challenging, relying on individual user practices and potentially introducing vulnerabilities beyond IT’s direct control.
Don’t forget the whole Bring Your Own Device (BYOD) practice. While BYOD aims to ensure employee satisfaction, flexibility, mobility, and productivity, it introduces a myriad of cybersecurity and compliance risks. Data leakage becomes a constant worry, as sensitive information could be inadvertently transferred or exposed through unsecured personal apps or compromised networks. The challenge lies in finding the right balance between allowing employee freedom and ensuring adequate data protection on personal devices.
At the same time, organizations face a growing number of regulations governing securing confidential, albeit unclassified data. Under certain regulations, enterprises are accountable for third parties processing data on their behalf. On top of managing internal risks, organizations now grapple with the added complexity of vendor risk. Although enterprises have increased cyber risk management responsibilities, they must manage them with fewer resources. Additionally, they face the pressure of complying with growing regulations, which come with significant noncompliance penalties.
What is Cybersecurity Risk Management?
Cybersecurity risk management is the strategic approach to prioritizing cyber threats. It can be defined as the continuous process of identifying, analyzing, assessing, and addressing cybersecurity threats to your organization. To effectively manage cybersecurity risks, organizations must identify their digital assets, evaluate existing security measures, and implement solutions to mitigate risks or maintain effective security practices.
Continuous vulnerability risk management (VRM) is vital as both the organization and external threats evolve. However, VRM should be an ongoing part of all business operations, where any discovered exploits are patched promptly. With work from home or remote working, BYOD, and the use of IoT devices and sensors in various physical locations, new potentially vulnerable devices are frequently added to the network. This could also happen with new installations or cloud orchestrations and app deployments. The new apps, deployments, installations, and orchestrations increase the attack surface.
Who is Responsible for Cybersecurity Risk Management?
Managing cybersecurity risks is not simply the job of an organization’s security team — every employee has a role to play, no matter their level. Employees and leaders within different business units tend to approach risk management separately, focusing only on their specific areas of responsibility. Unfortunately, they lack the holistic perspective required to tackle risk consistently and comprehensively. This begs the question, who should own what part of security risk? In essence, everyone shares ownership and responsibility for security risk. However, complexities arise when the four business functions are involved.
Every function pursues its agenda, often without fully understanding or empathizing with others. Sales teams prioritize customer satisfaction, seeking efficient methods for completing security audits. IT drives innovation with new technologies, occasionally perceiving security and compliance as hindrances to advancement. While security prioritizes safety, they often are out of touch with evolving technologies and regulations. Compliance teams ensure adherence to regulations, keeping everyone out of trouble. Regrettably, they often operate without a deep understanding of security.
To manage cybersecurity risk effectively, all functions must have clearly defined roles and specific responsibilities assigned to them. Gone are the days of isolated departments operating in disconnected confusion. Today’s cyber risk landscape calls for a unified, disciplined, consistent, and coordinated management solution. As part of cyber risk management, every organization must:
- Develop robust tools and policies to assess vendor risk.
- Identify emergent risks, including new regulations that have a business impact.
- Identify internal weaknesses such as poorly implemented multi-factor authentication (MFA).
- Adopt new mechanisms to mitigate cyber risks, such as adopting new policies and internal controls or training programs.
- Test their overall security posture.
- Document vendor security and risk management for regulatory assessment or to reassure potential customers.
Why is Cyber Risk Management Important?

Organizations implement cyber risk management to ensure most critical threats are promptly handled. Such an approach helps identify, analyze, evaluate, and address cyber threats based on the potential impact posed by each threat. A cyber threat management strategy acknowledges that an organization cannot block all cyber threats or eliminate all system vulnerabilities. Cybersecurity risk management can help organizations protect themselves against data breaches, cyberattacks, ransomware, and other types of cybercrimes. But what are the benefits of having a cybersecurity risk management plan?
Enhanced Security Posture
Planning and implementing a robust cybersecurity risk management can improve an organization’s cybersecurity posture. A risk management plan helps prevent various types of cybersecurity risks through:
Proactive Threat Mitigation
A cyber risk management plan helps identify and prioritize vulnerabilities before they can be exploited. It allows you to implement safeguards and mitigate potential attacks proactively.
Reduced Likelihiood of Breaches
By understanding their cyber threat landscape and addressing weaknesses, organizations can significantly reduce the chances of experiencing costly data breaches and operational disruptions.
Improved Incident Response
A well-defined risk management plan equips your team with clear procedures and protocols for efficiently responding to and containing cyber incidents, minimizing damage and downtime.
Compliance with Regulations
Today, there are many industry-specific regulations that organizations must demonstrate compliance with. To be compliant, an organization must meet and uphold certain levels of cybersecurity standards. Having a robust risk management strategy helps:
- Demonstrate due diligence: When an organization implements a cyber security strategy that showcases its commitment to data security, building trust with customers and partners.
- Meeting Industry Standards: Many industries have strict data privacy and security regulations, including HIPAA, ITAR, GDPR, PCI DSS, and CMMC, among others. Implementing a risk management plan ensures an organization adheres to these, avoiding hefty fines and reputational damage.
A robust risk management strategy aids organizations in meeting and upholding these regulatory compliance standards.
Situational Awareness
Another benefit of having a cybersecurity risk management plan is that it helps bring about situational awareness. Put simply, analysts can look at the available information, determine what is important, and act accordingly. Organizations must understand present and future risks. Awareness can be assessed on three levels, including:
Situational Awareness
This involves understanding the critical people, processes, and data within an organization, as well as organizational components for executing an effective information security strategy.
Situational Ignorance
An organization may assume that all is good without due consideration to the impact of processes, people, and data. It could be implementing the required security controls and awareness training but not having a process or strategy aligning with risk mitigation and reduction. Unfortunately, this results in budget creep.
Situational Arrogance
This happens when an organization continues spending big while routinely being breached or compromised. It may actually be taking processes, people, and data into account but not acting because of other budgetary priorities. Continuous failure to defend against attacks could inevitably lead to severe damage to a business’s reputation.
Cybersecurity risk management encompasses various security risk mitigation efforts. It’s crucial for all security organizations, across sectors and levels, to implement strategies for assessing, identifying, mitigating, and remediating vulnerabilities and risks.
Improved Decision Making
A cyber risk management strategy helps an organization understand the potential cyber threats and their associated consequences. This can help an organization make better decisions that consider cybersecurity. Hence, such an organization can better allocate resources and make better system design decisions.
Reduce Downtime
Whether DDoS attacks, ransomware, or phishing attempts, successful attacks can result in hours of disruptions in your organization’s operations. Such downtimes are excruciating and have a bearing impact on your reputation. Delays in one area of your organization might have cascading effects such as loss of productivity, workflow backup, or even lack of external and internal communication. A properly implemented cybersecurity risk management helps reduce downtimes as it includes incident response measures.
More Efficient Security Strategy
By focusing on threats posing the most significant risk, organizations can use risk management processes to develop effective security strategies. Hence, they can prioritize their security risk management efforts and better allocate resources.
Improved Visibility
Risk management enhances organizations’ insight into their cybersecurity status, pinpointing areas requiring additional security controls. This facilitates a deeper understanding of the security environment and enhances readiness to counter threats.
Enhanced Threat Detection
Implementing a robust cyber risk management strategy ensures organizations don’t relegated cybersecurity to an afterthought in their daily operations. It ensures that policies and procedures are followed and security is always up-to-date. A good cybersecurity risk management helps with continuous monitoring , identification, and mitigation of various types of cyber threats. It helps in:
- Fraud Protection
- Sensitive Data Leakage Monitoring
- Leaked Credentials Monitoring
- Supply Chain Risks
- Phishing Detection
- Automated Threat Mitigation
- Brand Protection
- Dark Web Activity Monitoring
- VIP and Executive Protection
- Malicious Mobile App Identification
Cybersecurity Risk Management Process
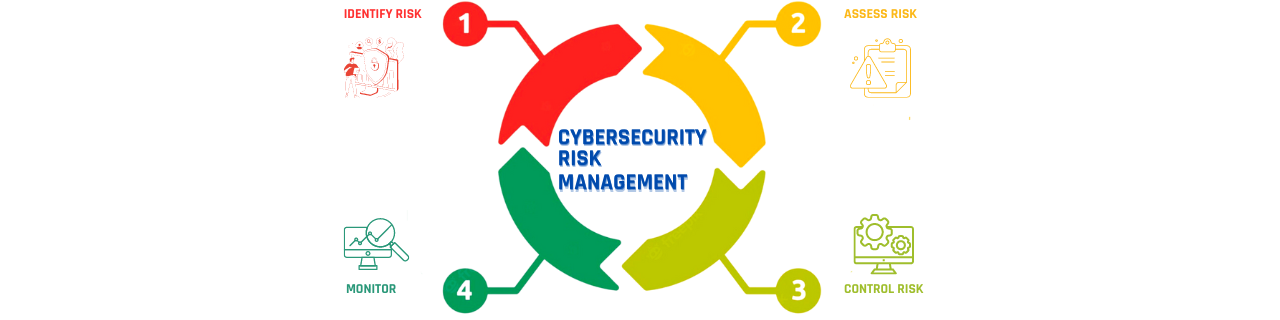
Cyberattacks aren’t random. There usually are signs of an imminent or planned attack against an organization, if you know where to look. Some signs include confidential information being put up for sale, mention of your organization in the dark web, and the registration of similar domain names that may be used for phishing attacks. Managing risk generally follows four steps starting with identifying cybersecurity risk. The risk is then assessed based on the probability of threats exploiting present vulnerabilities and their potential impact. Then, the organization uses various mitigation strategies to prioritize how risks will be addressed. Monitoring is the fourth step, and structured to current risk controls and response.
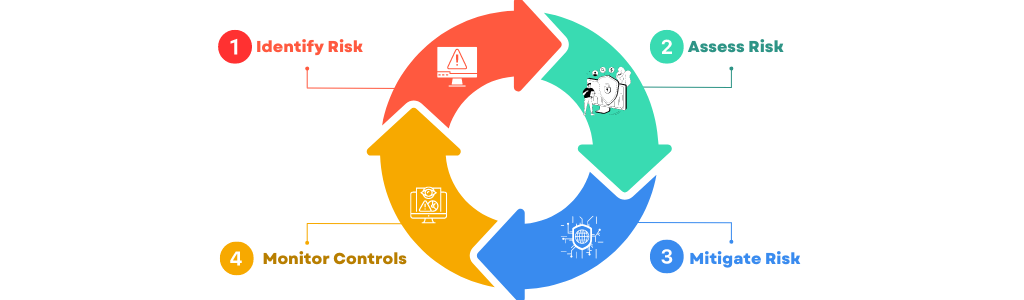
Fortunately, there’s a lot of guidance and help available for organizations looking to assess their risk levels. For instance, they can use the NIST SP 800-30 to assess the risk levels in their information systems. SP 800-30 expands on NIST SP 800-39 and is closely related to SP 800-53, another third-party risk management framework (RMF) which outlines privacy and security controls for the federal information systems. Although SP 800-30 is not mandatory within the private sector, it can be a helpful guide for any organization assessing risk.
Developing a Cybersecurity Risk Management Plan
To develop a robust risk management plan, let’s delve deeper into each of the 4 steps of the cybersecurity risk management plan.
Identify Cybersecurity Risks
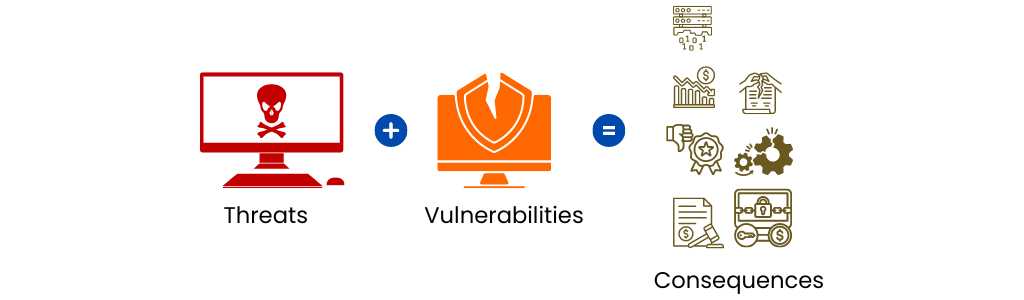
To identify cybersecurity risk, you must first understand what it is. So, what is an IT risk? Gartner defines IT risk as “the potential for an unplanned, negative business outcome involving the failure or misuse of IT.” Ask yourself, what is the likelihood of an existing threat exploiting a vulnerability? If odds exist, how dire would the outcomes be? Identifying cyber risks is the first step of the risk management process. To properly identify cybersecurity risks, you should have a good grasp of vulnerabilities, threats, and consequences of their coming together.
Threats can be defined as events or circumstances that have a likelihood of negatively affecting an organization’s assets, individuals or operations through unauthorized access, destruction, disclosure, or modification of information, and/or denial of service. Threats may arise from threat sources, which are situations or methods that may accidentally or intentionally exploit a vulnerability. Types of threat sources include:
(i) hostile cyber or physical attacks;
(ii) human errors of omission or commission;
(iii) structural or configuration failures
(iv) natural and man-made disasters, accidents, and failures beyond the control of the organization
These threat sources are detailed cyber threat section below.
Vulnerabilities refer to any weaknesses in security procedures, information systems, implementation, or internal control that a threat source may exploit. Because of inadequate internal functions such as security, vulnerabilities can externally exist in vendor relationships and supply chains.
Consequences are adverse results that arise when a threat exploits a vulnerability. The impact of a consequence measures its severity, and an organization must estimate such costs when trying to assess risk. These costs often arise from destroyed or lost information and may result in a considerable business setback for your organization.
Assess Cybersecurity Risks
Risk assessments are more than just compliance exercises; they are valuable opportunities to build a culture of security. Through assessing risks, an organization’s team gets to practice cooperation and communication which plays an important role in risk management in future. Assessments help answer one critical question: what’s your organization’s risk level?
Begin by identifying all assets and prioritize their importance. Then, identify all threats and vulnerabilities that may be present in your environment. You then should apply appropriate controls to address all known vulnerabilities. Next, try determining the possibility of a threat event occurring, then conduct an impact analysis to estimate its cost impact and potential consequences. Finally, use the risk determination to inform your risk response measures and risk management decisions.
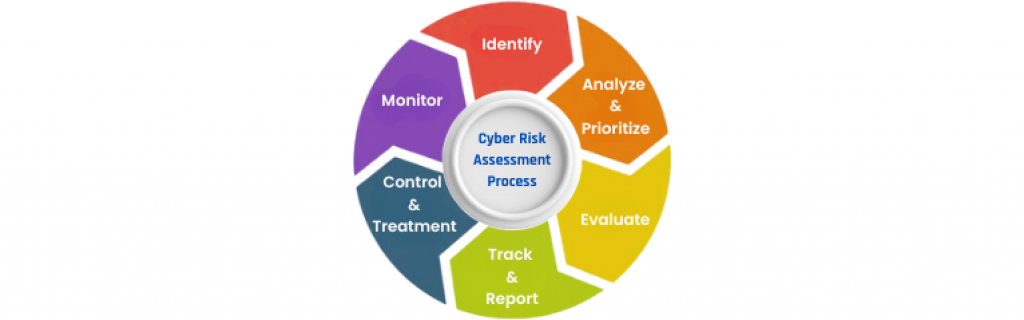
CISA has outlined its risk assessment process, which might appear a bit different from this. In its Guide to Getting Started with a Cybersecurity Risk Assessment, CISA identifies a 6-step process for conducting risk assessments. Organizations should:
- Identify and document network asset vulnerabilities
- Identify and use sources of cyber threat intelligence
- Identify and document internal and external threats
- Identify potential mission impacts
- Use threats, vulnerabilities, likelihoods, and impacts to determine risk
- Identify and prioritize risk responses
NIST SP 800-30 acts as a guide to Conducting Risk Assessments in federal information systems but can also be used in private organizations. The guidance identifies a 4-step process for conducting risk assessments, including:
- Preparing for the risk assessment by clarifying the purpose, scope, constraints, and risk analytics/models which you’ll use.
- Conduct a risk assessment to identify risks by impact and likelihood for an overall risk determination.
- Communicate and share risk assessment information with your team and stakeholders to drive their mitigation efforts.
- Maintaining assessment through continuous monitoring of your environments.
Identify Measures to Mitigate Cybersecurity Risks
Identification and assessment of risk are just a start. You must determine what your organization will do about the identified risks. What will be your mitigation response for managing risk? How will your organization manage residual risk? Any successful risk management team has a robust plan in place, guiding their risk response plan. This is a critical step of cyber risk management, where you must understand all your risk mitigation options. At this stage, you can use best practices or technological methods, or a combination of both.
Cyber Risk Mitigation Best Practices
“Cyber Risk Mitigation Best Practices” can be defined as the comprehensive strategies and protocols an organization may use to identify, assess, and mitigate potential cyber threats and vulnerabilities. They help organizations protect their digital assets and maintain operational resilience. So, what are the best practices for cybersecurity risk mitigation?
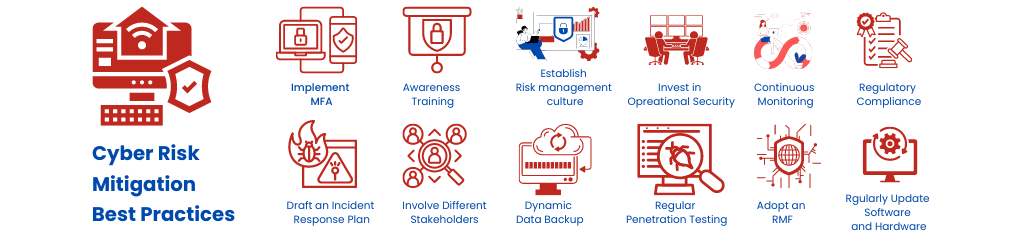
- Implementing multi-factor authentication to control access
- Cybersecurity awareness training programs for your teams and employees
- Regular, automated vulnerability scanning and penetration testing
- Dynamic data backup
- Updating software and hardware regularly
- Patching vulnerabilities in your information systems promptly
- Build a risk management culture
- Deploying privileged access management (PAM) solutions, etc.
What are Technological Cyber Risk Mitigation Measures?
Technological cybersecurity risk mitigation measures include using firewalls, encrypting network and data (at rest and in transit), and engaging automation to enhance system efficiency. Others include Runtime Application Self-Protection (RASP), DDoS and Bot protection solutions, and cloud protection tools. However, always base your risk management posture and risk response measures on real data. Smart organizations prioritize risk and mitigation solutions using data from real-world applications.
What Is Residual Risk in Information Security?
But what should you do with residual cybersecurity risk? What is it to begin with? Residual cybersecurity risk can be defined as the leftover risk after you have implemented all mitigation measures. This risk is unavoidable, and unfortunately, there’s not much you can do about it. With residual cybersecurity risk, organizations can either:
- Transfer it to a cybersecurity insurance provider that will shoulder it in the even of a cyber attack, albeit at a fee or
- If the cost of further mitigation outweighs the potential impact, accept the residual risk and implement monitoring and incident response plans.
The insurance option is preferred as it makes calculating the damage cost of cyber incidents easier.
What are the Costs Associated with Cyber Attacks?
It is increasingly becoming important for enterprises to accurately estimate damage costs related to a cyber risk. Organizations must consider the following 3 types of expenses when calculating or estimating damage costs associated with a cybersecurity risk:
- Reputational costs associated with data breaches which violate client trust and privacy.
- Fiscal costs include penalties and fines for non-compliance or lost income when new opportunities are lost or customers defect.
- Operational costs involve lost resources or time.
Reputational costs are the hardest to calculate, while fiscal costs are the easiest.
Use Continuous Monitoring
After identifying, assessing, and mitigating risks in your environment, that would be enough in a perfect world. Unfortunately, change is constant, especially in the cybersecurity landscape. Thus, your cybersecurity team must monitor information systems and environments to ensure that implemented internal controls align with IT risk. But should your organization monitor?
- Vendor risk: Ensure you assess and document compliance and security controls when onboarding new vendors. While this is a requirement of some regulations, your vendor shortcomings might quickly become your headaches.
- Internal IT use: What technologies does your internal team use? Are they secure? Can the hardware or applications introduce cyber risks? How does your team use the technologies to remain ahead of security gaps?
- Regulatory change: Regulatory compliance is a must in some industries. Thus, staying abreast with all regulations in your industry and their changes ensures you avoid fines and penalties. It also helps you align your internal controls with regulatory expectations.
What is a Cybersecurity Risk Assessment?
A cybersecurity risk assessment is a process by which an organization determines its key objectives and identifies appropriate IT assets necessary to realize its specific objectives. Cybersecurity Risk Assessment Involves identifying cyber attacks that might impact IT assets negatively. An organization must determine the likelihood of these attacks occurring and define the impact of each. Cyber risk assessments should identify the entire threat environment and its impact on the organization’s business goals. A risk assessment aims to assist security teams and other relevant stakeholders make informed decisions on the implementation of security measures to mitigate risks.
What are Cyber Threats?
Cyber threats refer to any vector(s) that could be exploited to breach security, exfiltrate data, cause damage to organizational assets, or individuals, or disrupt operations. Cyber threats come from threat sources. The most common types of threat sources include:
Human error
Humans remain the weakest link in cybersecurity. An employee may unwittingly download malware or be tricked by social engineering schemes such as phishing. A member of your security team may misconfigure storage or data sources, resulting in sensitive data exposure. Thus, organizations should enforce strong security controls and establish employee training programs to prevent and mitigate these threats effectively.
Adversarial threats
These threats may emanate from trusted insiders, disgruntled former employees, established hacker collectives, insider threats, ad hoc groups, privileged insiders, corporate espionage, and sometimes, nation states. Adversarial threats also include malware created by either of these entities. You can outsource security or, if you have enough resources, establish a security operations center with specialized tooling and trained security staff.
System failure
Data loss and disruptions in business continuity are some of the impacts of system failure. However, system failure may be caused by either of the above adversaries. To prevent frequent system failures, ensure your critical systems run on high-quality hardware, implement place redundancies and backups to ensure high availability, and choose providers who offer timely support.
Natural disasters
Threats can also exist in the form of natural disasters such as fire, hurricanes, lightning, earthquakes, etc, and will cause similar damages to a malicious cyber attacker. Natural disasters will result in the destruction of an organization’s digital or physical resources, disruption of services, and loss of data. You can minimize the impacts of natural disaster threats by using distributed cloud resources or distributing your organizational resources in multiple physical sites.
What are Some Common Threat Vectors Impacting Organizations?
Below are the common types of cyber threat vectors affecting most organizations today:
- Data leaks: Cloud and storage misconfiguration, and threat actors might result in sensitive data leaks.
- Unauthorized access could result from malware, employee error, or malicious attackers.
- Service disruption: Service downtime may be accidental or caused by a DoS or DDoD attack. Unfortunately, these downtimes result in revenue and reputational losses.
- Data losses: Poorly configured backup and replication processes might result in accidental deletion or data losses.
- Privilege abuse: This arises when authorized users misuse information by deleting, altering, or using data without authorization.
Cyber Risk Management Frameworks
Besides NIST SP 800-53, there are other risk management frameworks, each providing standards that organizations may use to identify and mitigate risks. Security leaders and senior management may use these frameworks to assess and enhance their organization’s security posture. But what are the benefits of a cyber risk management framework? A cybersecurity risk management framework can help your organization effectively assess, mitigate, and monitor cyber risks. It also helps an organization define security processes and procedures for addressing cyber risks. Below are the common cyber risk management frameworks:
NIST Cybersecurity Framework (NIST CSF)
NIST CSF has a set of 108 recommended security actions that are spread across 5 security functions. But What are the 5 functions of NIST CSF? The 5 critical security functions in NIST CSF include: Identify, Protect, Detect, Respond, and Recover. NIST CSF is designed to help enterprises manage and reduce all types of cyber risk, including DDoS, malware, Phishing attacks, password theft, interception of network traffic, and social engineering, among others. NIST Cybersecurity Framework’s first pillar states that “the organization understands the cybersecurity risk to organizational operations (including mission, function, image, or reputation), organizational assets, and individuals.” The Framework recommends that organizations:
- Identify and document asset vulnerabilities
- Tune into the latest cyber threat intelligence from information-sharing forums
- Identify and document both internal and external threats
- Identify the potential business impacts and likelihood of risk events
- Use threats, vulnerabilities, likelihood, and impacts to determine risk
- Identify and prioritize risk responses
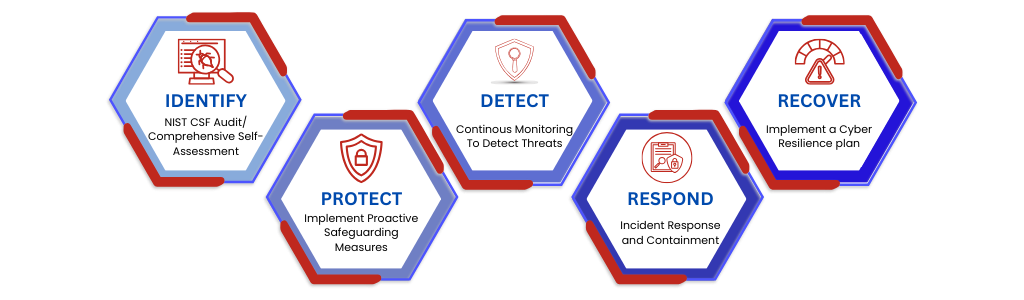
NIST cybersecurity framework also details what a risk management strategy should include. It states that “the organization’s priorities, constraints, risk tolerances, and assumptions need to be established to support operational risk decisions.” Under this framework, organizations also must establish and implement processes to identify, assess, and manage supply chain risks.
ISO/IEC 27001:2013
ISO 27001 clause 6.1.2 outlines the requirements of an information security risk assessment and organizations should:
- Establish and maintain information security risk assessment processes that include the risk acceptance and assessment criteria.
- Ensure that risk assessments are consistent, valid, and produce ‘comparable results.
- Apply the assessment processes to identify risks associated with the confidentiality, integrity, and availability (CIA) of the information assets within the defined scope of the Information Security Management System (ISMS).
- Assign risk to risk owners within the organization who will determine the level of risk, and assess the potential consequences should the risk materialize, together with ‘realistic likelihood of the occurrence of the risk’.
- Prioritize risk after assessment for risk treatment and then manage in accordance with the documented methodology.
DoD Risk Management Framework (RMF)
Compared to other Government requirements, DoD imposes stricter compliance demands based on the information they manage and the importance of their work. DoD RMF defines the guidelines that DoD agencies use for the assessment and management of cybersecurity risks. It divides cyber risk management strategy into six steps, including categorize, select, implement, assess, authorize, and monitor.
Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE)
OCTAVE is a product of the Software Engineering Institute at Carnegie Mellon University as a collaborative, self-directed approach to cyber risk assessment, planning, and mitigation. Octave involves 3 top-level phases
- Establishing drivers and objectives
- Identifying critical assets and threats
- Developing mitigation plans and strategies
This method can help organizations effectively understand their risk profile, dependencies, assets, and design solutions addressing specific objectives and needs. OCTAVE has two subversions: OCTAVE FORTE and OCTAVE Allegro. OCTAVE FORTE is an enterprise solution and includes 10 steps for cyber risk management, while OCTAVE Allegro is for small and mid-sized businesses and comprises 8 steps.
Factor Analysis of Information Risk (FAIR) Framework
FAIR Framework was released by The Open Group to help private organizations define, measure, analyze, understand, mitigate, and manage risk. The FAIR Framework helps enterprises make informed decisions when developing cybersecurity best practices.
NIST Risk Management Framework (RMF)
NIST RMF integrates privacy, security, and cyber supply-chain risk management activities into the System Development Life Cycle (SDLC). The RMF process may be applied to legacy and new systems, within any organization regardless of sector or size, and to any technology or system. The following are the key steps in NIST Risk Mmanagement Framework:

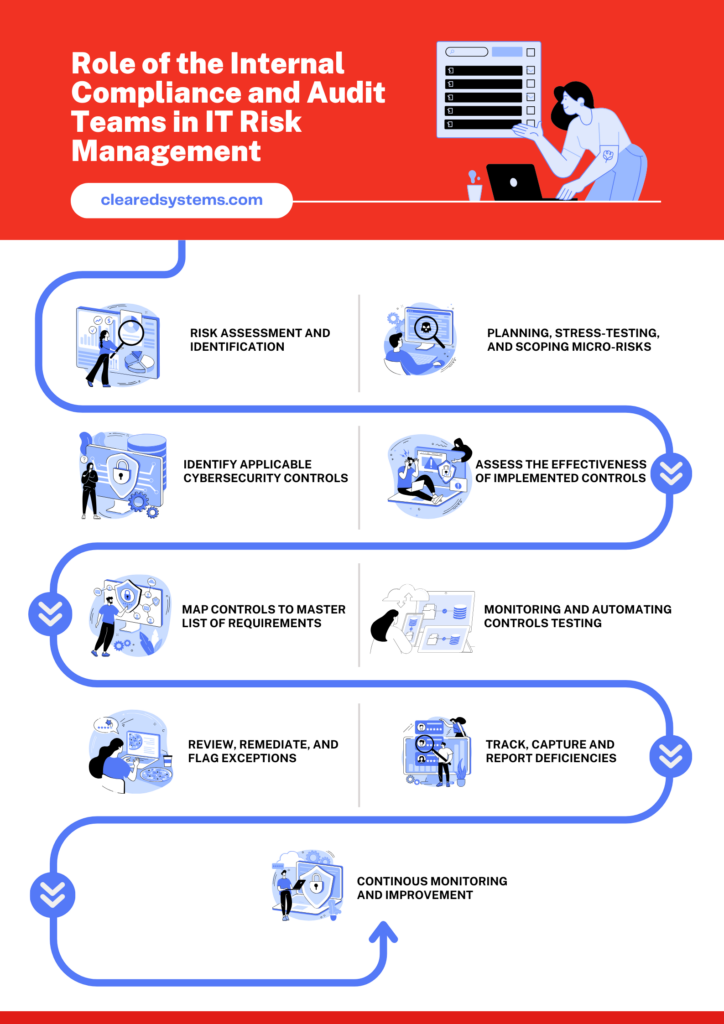
What is the Role of the Internal Compliance and Audit Teams in IT Risk Management?
Risk management is not a one time thing; it is continuous and involves re-assessment, new testing, and continuous mitigation. However, internal compliance and audit teams significantly can control IT risk through:
What are the Best Practices for Cybersecurity Risk Management?
Cybersecurity risk management can prove a challenge for most, particularly those organizations that aren’t used to incorporating assessments in their compliance with cybersecurity efforts. However, there are best practices that such organizations may adopt to ensure they remain compliant and secure. These organizations should:
Identify Critical Workflows
Organizations should analyze workflows contributing substantial business value and evaluate associated risks, paying particular attention to potential impacts. For example, payment processes, while valuable, can introduce data leakage and fraud risks. They must communicate these processes to the cybersecurity team, including data assets, tools, and teams involved, to implement necessary controls effectively. Foster collaboration between cybersecurity and business personnel, prioritizing proactive approaches over solely relying on maturity-based strategies.
Balance Current and Future Needs
Business and IT leaders may sometimes find themselves having to decide between an organization’s long-term planning and pressing issues. It becomes even more complex when future threats have to be balanced with the current expenditure. Hence, organizations must understand how to manage present and future risks.
Build a risk management culture
Establishing an organization-wide, cybersecurity-focused culture is essential for an effective cybersecurity risk management program. This culture serves as the foundation for your risk management framework. By raising awareness about cybersecurity’s significance and the potential impact of cyberattacks, you prioritize cybersecurity for all team members across departments.
Map Data Flows
To effectively understand risks to any data, an organization must first know how it moves through its information systems. Using dashboards and IT tracking to map the data flows can help an organization understand how far its security perimeter spans. These organizations can also understand the interactions of their complex systems and determine their points of weakness.
Prioritize Cyber Risks
Organizations should evaluate risk levels based on the value of the information and cost of prevention to inform their risk management and mitigation strategy. High-level risks should be addressed immediately while lower-level risks could be accepted as tolerable or handled later. However, the cost of protecting an asset should not surpass its value, unless there is risk of reputational damage.
Train Employees
Train employees in safe internet practices, phishing detection, password security, and data privacy to foster a cybersecurity-aware culture. Given the human role in cybersecurity, ensure all staff can spot malware, phishing attempts, and risks, and know whom to report suspicious activities to.
Securing Edge Devices
Daily used devices are the most vulnerable and riskiest aspects of any information system. These are the ones that are in constant use and can be exploited by attackers. Such elements include website interfaces, APIs, IoT nodes, and mobile devices. Organizations should implement the necessary measures to ensure attackers cannot pivot these devices to exploit their systems.
Continuous Risk Assessments
Conduct adaptable, ongoing, and actionable risk assessment and identification to remain abreast of growing cyber threats and solutions. Additionally, organizations should revisit cybersecurity risk management processes to identify and address any gaps. Cybersecurity professionals depend on actionable risk assessment insights to protect digital assets and environments effectively.
Develop a Response Plan
Organizations must develop a robust incident response plan focused on pre-identified risks. It will provide a roadmap that relevant stakeholders and teams will follow. This is even a requirement for some regulations like DFARS 7012. Additionally, the incident response plan must identify what needs to be done and by whom in case of an incident.
Integrate Cybersecurity with a Risk Management Framework
Any organization must integrate its risk-based cybersecurity program into a risk management framework. Instead of using the framework as a general guideline, organizations should use it as a foundational principle. Using this approach, businesses can frame their cyber risk management as a business risk, enabling them to understand it better.
Communicate Risk to Business Leaders
IT and business leadership may seem at odds over decision-making. However, IT and compliance leaders should effectively communicate risks to business leaders, enabling informed decisions aligned with organizational risks.
Essential Capabilities for Managing Cyber Ris
What capabilities will your IT team need to conduct cybersecurity assessments and manage risks effectively?
Communication and Collaboration tools
IT and Cybersecurity teams need tools for effective communication during IT risk assessments and mitigation stages. The tools must provide clear conversation for teams in different time zones, locations, and countries.
Risk Management Frameworks
Your team must leverage the risk management frameworks described above to guide risk assessment and management. Leveraging these frameworks can help your audit teams conduct a quick, precise gap analysis between current operations and compliance requirements.
Unified, Single Data Repository
Compliance, risk, and security professionals should store risk assessments, documentation, test results, and other relevant information in a single data repository.
Issues Management Tools
Another capability organizations should develop for their audit and cyber risk management teams is issues management. Issues management tools organize assignments of particular mitigation steps and automate reminders, enabling teams to accomplish tasks promptly. They can send notifications to senior executives if some tasks aren’t completed.
Analytics
The communication and collaboration tools can help with predictive and root cause analysis.
Versatile Reporting
Your IT audit and cyber risk management teams should be able to present IT risk management reports to senior executives and business unit leaders in a usable and most desired format.
Managing Cyber Risk in a Complex Digital World
Cybersecurity risk management is a critical process for organizations of all sizes in today’s digital landscape. With growing interconnectedness comes increased vulnerabilities that make cyber threats a constant concern. To reduce exposure, organizations must take a proactive and holistic approach to identifying, analyzing, and mitigating cyber risks across the enterprise. A robust cyber risk management plan that details roles, policies, tools, and procedures is essential for improving security posture, ensuring regulatory compliance, minimizing business disruption, enhancing visibility, and enabling better decision-making. Though complex, cyber risk management done right can significantly boost resilience against the evolving threat landscape. With a sound strategy grounded in assessing risk exposure and prioritizing responses, even resource-constrained teams can implement effective cyber protections tailored to their unique environment and priorities. A vigilant, coordinated effort makes managing cyber risk far less daunting. Need help with managing your cyber risk? Give Cleared Systems a call.
Share in Social Media
See More Case Studies

Securing Defense Contracts: A DFARS 252.204-7012 Compliance Case Study
Discover how Cleared Systems helped a Federal Contractor successfully achieve DFARS 252.204-7012 compliance by strengthening its cybersecurity posture, giving it a competitive edge when bidding for DoD Contracts.

What is GCC High? For ITAR & CMMC 2.0
Microsoft 365 Government Community Cloud (GCC) High is a specialized cloud solution tailored for U.S. federal, state, local, tribal, and territorial government organizations, as well as for contractors who hold or process data subject to specific security regulations. In this article, we will explore the features, benefits, and differences between Microsoft 365 GCC High and other Office 365 offerings.

Is AutoCAD ITAR Compliant? A Comprehensive Guide for Defense Manufacturers
Defense contractors and manufacturers working with sensitive military technologies face a critical question when selecting computer-aided design software: Is AutoCAD ITAR compliant? This question becomes

How to Get Help in Windows: Guide to Security and Compliance Support
In today’s digital landscape, ensuring your computer systems are secure and compliant with industry regulations is essential for both businesses and individuals. Windows, as one

Microsoft Copilot for GCC High: Enhancing Security and Compliance
In today’s fast-evolving digital landscape, organizations that handle sensitive data, particularly those in government sectors or defense contractors, face growing pressure to maintain strict security
Partner with Us for Compliance & Protection
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Security
- Compliance
- Peace of mind
- Efficiency
- Trust
What happens next?
Schedule an initial meeting
Arrange a discovery and assessment call
Tailor a proposal and solution
