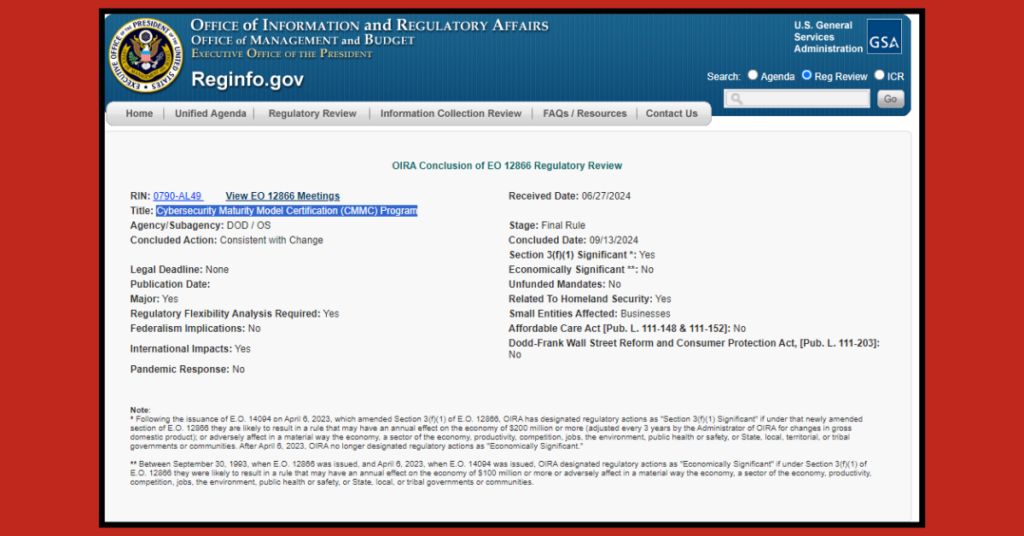
CMMC Program Updates: What You Need to Know and How to Avoid Snake Oil Salesmen
The Department of Defense’s (DoD) Cybersecurity Maturity Model Certification (CMMC) is rapidly moving forward, signaling significant changes for defense contractors. Two critical rules—one for the









