ISO 27001 Compliance & Audit Consulting Services
In today’s digital landscape, safeguarding sensitive information is crucial for organizations of all sizes. Achieving ISO 27001 certification demonstrates a commitment to maintaining the highest standards of information security management. At Cleared Systems, we offer comprehensive ISO 27001 Compliance & Audit Consulting Services to help businesses across all industries achieve and maintain ISO 27001 certification efficiently and effectively.
Why ISO 27001 Certification Matters
ISO 27001 is the leading international standard for Information Security Management Systems (ISMS). It provides a framework for managing and protecting sensitive information through a systematic approach, including risk management and continuous improvement. ISO 27001 certification ensures that your organization:
- Mitigates risks related to data breaches and cyber threats.
- Complies with regulatory and contractual requirements.
- Builds trust with clients, partners, and stakeholders.
- Protects its reputation by implementing industry-standard security controls.
Whether you’re seeking initial certification or maintaining compliance through regular audits, our expert consultants provide a tailored approach to meet your specific business needs.
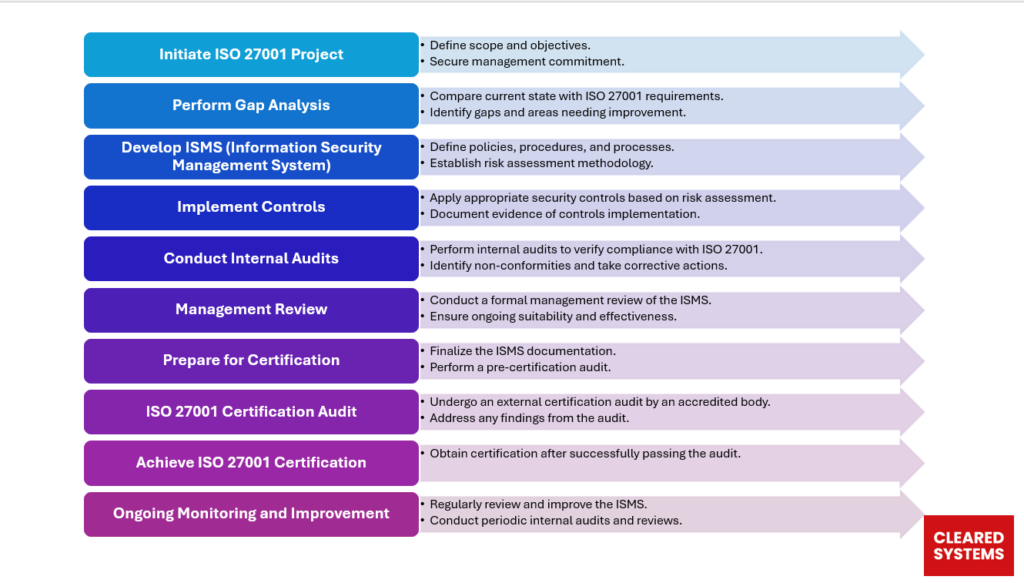
Our ISO 27001 Consulting Services
At Cleared Systems, we understand that each organization faces unique challenges in achieving compliance. Our consultants guide you through each stage of the ISO 27001 certification process, from planning and implementing an ISMS to conducting internal audits and preparing for certification. Our services include:
Gap Analysis
We conduct a thorough gap analysis to assess your current security posture against the ISO 27001 standard. This helps identify any gaps or weaknesses that need to be addressed before proceeding with certification.
Risk Assessment & Treatment
Our consultants perform a comprehensive risk assessment, identifying potential threats and vulnerabilities to your information assets. We help develop a risk treatment plan to mitigate identified risks, ensuring that your ISMS is both compliant and effective.
Policy & Procedure Development
We work closely with your team to design and implement security policies and procedures that align with ISO 27001 requirements. These documents form the backbone of your ISMS and are essential for certification.
ISMS Implementation
Our experts will assist in implementing your Information Security Management System, ensuring that all security controls, processes, and procedures are in place. We provide training and guidance to your staff to ensure proper adoption and management of the ISMS.
Internal Audit
Prior to the official certification audit, we conduct an internal audit to evaluate your ISMS. This helps identify any potential issues and areas for improvement, allowing for corrective actions to be taken before the certification audit.
Certification Support
We support you through the entire ISO 27001 certification process, working directly with the certification body to ensure a smooth and successful audit. Our consultants are on hand to provide guidance and answer questions during the external audit.
Ongoing Compliance & Audit Support
Achieving ISO 27001 certification is only the beginning. We offer ongoing compliance support, including periodic audits and updates to your ISMS, ensuring that your organization continues to meet the evolving ISO 27001 requirements.
Benefits of Working with Cleared Systems
Expertise
Our team of ISO 27001 certified consultants brings years of experience in information security, compliance, and risk management. We stay up-to-date with the latest industry standards and best practices, ensuring that your organization receives the highest level of service.
Tailored Solutions
We understand that no two organizations are alike. Our consulting services are tailored to meet your specific business requirements, whether you’re a small business or a large enterprise.
Proven Results
Cleared Systems has helped numerous organizations achieve ISO 27001 certification, from tech companies to defense contractors. We deliver results by providing actionable insights and hands-on guidance throughout the compliance process.
End-to-End Support
From initial planning and assessment to certification and beyond, our consultants are with you every step of the way. We offer continuous support to ensure that your ISMS remains compliant and effective as your business evolves.
ISO 27001 Compliance for Defense Contractors
For defense contractors, maintaining a high standard of information security is crucial for meeting regulatory requirements such as the Defense Federal Acquisition Regulation Supplement (DFARS) and CMMC 2.0. ISO 27001 certification not only improves your security posture but also ensures compliance with these regulations, making your organization a trusted partner for the U.S. government and other defense clients.
Ready to Achieve ISO 27001 Certification?
ISO 27001 certification is a valuable asset that demonstrates your organization’s commitment to information security. With Cleared Systems by your side, you can achieve certification and protect your business from evolving cyber threats. Contact us today to learn how our ISO 27001 Compliance & Audit Consulting Services can help your organization succeed.
What is ISO 27001 certification?
ISO 27001 is an international standard that sets the requirements for an Information Security Management System (ISMS). It helps organizations manage and protect their information assets through a systematic approach to security, including policies, procedures, and risk management. Certification demonstrates your organization’s commitment to securing sensitive information.
Why is ISO 27001 certification important?
ISO 27001 certification provides several benefits, including:
- Improved information security management.
- Compliance with legal, regulatory, and contractual obligations.
- Reduced risk of data breaches and cyber threats.
- Increased trust from customers, partners, and stakeholders.
- Competitive advantage in industries that require stringent security controls.
Who needs ISO 27001 certification?
ISO 27001 is relevant for organizations of all sizes and industries, particularly those that handle sensitive or confidential information. It is especially valuable for businesses in sectors like technology, finance, healthcare, and defense contracting, where data security is critical.
What is involved in the ISO 27001 certification process?
The ISO 27001 certification process involves several key steps:
- Conducting a gap analysis to assess your current security posture.
- Performing a risk assessment and creating a risk treatment plan.
- Developing and implementing an Information Security Management System (ISMS).
- Conducting an internal audit to identify and address any issues.
- Undergoing an external audit by an accredited certification body.
How long does it take to achieve ISO 27001 certification?
The timeline for achieving ISO 27001 certification varies depending on the size of your organization, the complexity of your information security needs, and your current security posture. On average, the process can take anywhere from 3 to 12 months.
What is a gap analysis, and why is it important?
A gap analysis is a critical first step in the ISO 27001 certification process. It involves evaluating your current information security practices against the ISO 27001 standard to identify areas where improvements are needed. This helps ensure that your organization is fully prepared before moving forward with certification.
What is an Information Security Management System (ISMS)?
An ISMS is a set of policies, procedures, and controls that an organization uses to manage and protect its information assets. The ISMS is the foundation of ISO 27001 compliance, providing a structured approach to risk management, security policies, and continuous improvement of security measures.
How much does ISO 27001 certification cost?
The cost of ISO 27001 certification varies depending on factors like the size of your organization, the scope of the ISMS, and the external certification body’s fees. At Cleared Systems, we offer tailored consulting packages to meet your specific needs, ensuring a cost-effective path to certification.
What happens during an ISO 27001 internal audit?
An internal audit is a key part of the certification process. It involves reviewing your ISMS to ensure that it complies with ISO 27001 requirements. This includes checking the effectiveness of your security controls, risk management practices, and compliance with security policies. The goal is to identify and address any gaps before the external audit.
How often is an ISO 27001 audit required?
ISO 27001 certification is valid for three years, but regular surveillance audits are required to maintain certification. Typically, these audits are conducted annually to ensure continued compliance with the standard. At the end of the three-year cycle, a recertification audit is needed.
Can ISO 27001 certification help my organization meet other compliance requirements?
Yes! ISO 27001 can help your organization comply with other regulatory frameworks, such as the General Data Protection Regulation (GDPR), NIST 800-53, CMMC, and HIPAA. The ISMS framework helps streamline compliance with these and other regulations by establishing strong security controls.
How does ISO 27001 certification benefit defense contractors?
For defense contractors, ISO 27001 certification demonstrates a strong commitment to cybersecurity, which is critical for securing defense contracts. It also helps meet compliance requirements under the Defense Federal Acquisition Regulation Supplement (DFARS) and the Cybersecurity Maturity Model Certification (CMMC), both of which require stringent security controls to protect sensitive government data.
What role does Cleared Systems play in ISO 27001 certification?
At Cleared Systems, we offer end-to-end ISO 27001 consulting services. From performing gap analyses and risk assessments to developing your ISMS and supporting you through the certification audit, we are here to guide you every step of the way. Our team of experts ensures that you achieve certification efficiently and maintain compliance long-term.
What if we already have security policies in place?
If your organization already has security policies and procedures, we will review them as part of our gap analysis. We’ll help you align existing policies with ISO 27001 requirements, making necessary updates and filling any gaps to ensure your ISMS meets certification standards.
How do I get started with ISO 27001 certification?
Getting started is simple. Contact Cleared Systems to schedule a consultation. Our team will assess your needs, develop a tailored plan, and guide you through every step of the ISO 27001 certification process.
What Clients Says About Us

Partner with Us for Compliance & Protection
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Security
- Compliance
- Peace of mind
- Efficiency
- Trust
What happens next?
Schedule an initial meeting
Arrange a discovery and assessment call
Tailor a proposal and solution










