8570 Compliance: Ensuring Your Team Meets DoD Cybersecurity Standards
In an era where digital security is paramount, understanding and adhering to the Department of Defense (DoD) Directive 8570.1 is not just a regulatory requirement, but a crucial step in safeguarding national security. Commonly referred to as “8570 compliance,” this directive is a cornerstone in the DoD’s strategy to ensure that all personnel with access to DoD information systems possess a baseline level of cybersecurity knowledge and certification. This article delves into the essence of 8570 compliance, unraveling its complexities and highlighting its significance for professionals and organizations working in or with the DoD.
As we navigate through this comprehensive guide, we will explore the intricate layers of 8570 compliance, from understanding its fundamental requirements to implementing strategies that ensure your team not only achieves but also maintains these critical standards. Whether you are a cybersecurity veteran or new to the field, this article aims to equip you with the knowledge and insights needed to align with the DoD’s cybersecurity benchmarks, thereby enhancing the security of your operations and contributing to the broader goal of national defense.
Understanding 8570 Compliance
At its core, 8570 compliance is more than a set of guidelines; it’s a critical framework established by the Department of Defense (DoD) to ensure that all personnel involved with information systems have a baseline level of cybersecurity knowledge and relevant certifications. This compliance is mandated under the DoD Directive 8570.1 and applies to every individual with privileged access to DoD IT systems – be it military personnel, civilians, or private contractors.
The Essence of 8570 Compliance
Also called the Information Assurance Workforce Improvement Program, DoD 8570 is not a certification. It is a policy that provides guidelines and procedures for training, certification, and management of authorized users of DoD information systems that have information assurance roles. This includes military service members, civilian employees, contractors, and foreign employees working for the DoD. The directive mandates these personnel to obtain industry-standard certifications accredited by the American National Standards Institute (ANSI) based on their roles and responsibilities. It categorizes workforce into Information Assurance Technical (IAT) and Information Assurance Management (IAM) roles and assigns qualification levels. Employees handling Information Assurance System Architect and Engineer (IASAE) and Computer Network Defense Service Provider (CND-SP) also must be certified. Personnel must achieve required certifications within specified timeframes and maintain credentials through continuous education. To maintain 8570 compliance, expired certifications must be renewed and shouldn’t be considered in the workforce reports.
DoD 8570 compliance comprises two parts: a baseline certificate and an environment certification. This could mean something like a Security+ CE and a CCNP or CCNA, depending on your role. All IAT personnel are required to achieve the appropriate IA certification within 6 months (DoD 8570.01-M paragraph C2.3.9) of assignment of IA duties unless granted a waiver. Those not appropriately certified within the 6 months of assignment or who have not maintained their certification status aren’t permitted privileged access. Compliance The goal is to build a qualified IA workforce that can effectively secure DoD systems and data. By implementing workforce identification, training, and certification tracking, the directive aims to put the right skilled people in critical cybersecurity positions. Essentially, it standardized cybersecurity expertise across the DoD through stringent certification requirements and ongoing training.
Categories and Levels in 8570 Compliance
As mentioned above, achieving 8570 compliance requires that employees acquire specified certifications based on the role. The approved 8570 compliant certifications are divided into three main categories: IAT, IAM, and IASAE. These categories are further subdivided into levels as explained below:
Information Assurance Technical (IAT)
The DoD Information Assurance Technician (IAT) certification program trains and certifies personnel on protecting information systems and networks. IAT certifications are mandated by the DoD for military, civilian and contractor IT roles interacting with DoD information systems. It has 3 levels that validate skills in security monitoring, vulnerability assessment, incident response, policy enforcement, and managing system security controls as detailed below.
This level of the IAT category is for employees with 0-5 years of experience and applies to computer technicians, security analysts, network, systems, and application administrators. Level 1 IAT personnel are expected to perform the following roles:
- Applying pre-established guidelines and instructions for the performance of Information Assurance tasks within a computing environment (CE).
- Recognizing potential security violations and taking necessary actions to report incidents as mandated by regulations while also working to mitigate any adverse impact.
- Providing end-user IA support for all computing environment operating systems, applications, and peripherals.
- Applying CE-specific IA program requirements to single out and address areas of weakness.
- Offering support, monitoring, testing, and troubleshooting for software and hardware IA issues related to a computing environment.
- Implementing appropriate CE access controls in accordance with established protocols.
- Testing IA safeguards as outlined in established test plans and procedures.
- Following established IA security procedures and safeguards and ensuring compliance with assigned responsibilities.
- Ensuring compliance with system termination procedures and incident reporting requirements related to potential security incidents or breaches in the computing environment.
In general, DoD 8570 IAT Level 2 applies to personnel with information assurance technology or related area work experience of at least 3 years. These include professionals like System Admins, information security analysts, and IT security specialists. Such employees also must have a mastery of Level 1 functions above. Personnel at this level usually focus on security-related functionalities like finding and patching vulnerabilities, intrusion detection, and improving system security. These professionals perform the following functions in furtherance of DoD 8570 compliance:
- Demonstrate proficiency in IAT Level 1 information assurance knowledge and skills for computing environments.
- Investigate potential security breaches to determine if network policies have been violated, evaluate impacts, and preserve evidence.
- Support, monitor, test, and troubleshoot hardware and software information assurance issues in the network environment.
- Recommend and schedule information assurance repairs and maintenance for the network environment.
- Provide customer support functions such as installation, configuration, troubleshooting, customer assistance, and/or training in response to customer requirements for the IA needs in the network environment.
- Offer end-user support for all information assurance applications in the network environment.
- Analyze patterns of noncompliance and take appropriate administrative or programmatic actions to minimize security risks and insider threats.
- Manage user accounts, network permissions, and system and equipment access in the network environment.
- Analyze system performance to identify potential security vulnerabilities.
This IAT level applies to professionals having Information Assurance experience of at least 7 years. These are experts in IAT levels 2 and 3 functions. IAT level 3 personnel perform high-level technical roles and include CISOs, PCI security specialists, and IT managers. They are also responsible for the secure operation and integration of systems, besides taking up Leadership roles. Other functions that IAT Level 3 personnel are expected to perform in line with DoD 8570 include:
- Providing support for and/or coordinating all enclave operations and applications.
- Directing or supporting system developers on how to remediate security issues identified during testing.
- Examining enclave vulnerabilities and determining appropriate mitigating actions
- Providing inputs to or formulating an information assurance or IT budgets
- Mastering IAT levels 1 and 2 network and computing environments skills and knowledge
- Implementing enclave vulnerability Countermeasures
- Analyzing IA patterns and security incidents to determine the right remedial action to correct the identified vulnerabilities.
- Identifying or determining if a security incident violates a law that needs legal action.
Information Assurance Management (IAM)
The next category of the DoD 8570 is Information Assurance Management or IAM. Certifications in this category are more focused on leadership and managerial skills. Hence, IAM professionals are essential in managing and implementing information security programs across organizations regardless of size. With increased sophistication in cyber threats, there’s a need to have professionals who understand and can recommend proper mitigating solutions.
IAM Level 1 applies to professionals with 0-5 years of experience. Qualifications under this level relate to entry-level management roles and apply to jobs like IA managers, cybersecurity analysts, ISSO, and ISSM. They are required to offer support for the development, integration, and evaluation of security technologies, architectures, and systems. To ensure 8570 compliance, these professionals must apply their knowledge of IA procedures, policies, and structure to design, develop, implement, and maintain a secure CE. Additionally, IAM Level 1 personnel should:
- Assess and mitigate system vulnerabilities.
- Use organization-specific and federal publications to manage the operations of their CE systems.
- Ensure IA security requirements are identified appropriately in CE operation procedures.
- Design and implement security solutions
- Administer and support data recovery and retention within the computing environment.
- Ensuring adherence to system configuration guidelines
- Ensuring information assurance requirements for a system or DoD component are integrated into the CoOP (Continuity of Operations Plan)
IAM Level 2 pertains to professionals with over 5 years of managerial experience, emphasizing expertise in Information Assurance (IA) policy, procedures, and workforce structure. The primary focus is on developing, implementing, and maintaining a secure network environment. Functions associated with Level 2 IAM, as outlined by DoD 8570, include but are not limited to:
- Developing, implementing, and enforcing policies and procedures that align with the legislative intent of relevant laws and regulations for the network environment (NE).
- Recommending resource allocations necessary for securely operating and maintaining an organization’s NE IA requirements.
- Identifying alternative functional IA security strategies to address organizational NE security concerns.
- Evaluating selected security safeguards to ensure that security concerns outlined in the approved plan have been adequately addressed.
- Assessing the presence and sufficiency of security measures proposed or provided in response to requirements specified in acquisition documents.
- Assisting in the collection and preservation of evidence used in the prosecution of computer crimes.
- Creating, distributing, and maintaining plans, instructions, guidance, and standard operating procedures related to the security of network system operations.
- Formulating security requirements for hardware, software, and services acquisitions specific to NE IA security programs.
- Reviewing IA security plans for the NE.
These responsibilities are typically associated with high-level management and leadership roles in information security.
IAM Level 3 is tailored for seasoned professionals with a minimum of 10 years of management experience, leveraging their expertise in Information Assurance (IA) policy, procedures, and workforce structure to create, implement, and uphold a secure enclave environment. Key functions expected from Level 3 IAM personnel, as per DoD 8570, include but are not limited to:
- Establishing information ownership responsibilities for each Department of Defense Information System (DoD IS) and implementing a role-based access scheme.
- Securely integrate and apply department/agency missions, organization, functions, policies, and procedures within the enclave.
- Ensuring personnel with privileged access performing IA functions and those at IAM Levels I and II and IAT Levels I – III get the necessary initial and ongoing IA training and certification(s) to fulfill their duties.
- Interpreting patterns of non-compliance to determine their impact on risk levels and/or the effectiveness of the enclave’s IA program.
- Evaluating proposals to assess how effective proposed security solutions meet enclave requirements outlined in contract documents.
- Conducting economic, cost-benefit, and risk analyses in the decision-making process.
- Ensuring that security-related provisions in system acquisition documents address all identified security needs.
- Evaluating and approving development efforts to ensure baseline security safeguards are appropriately installed.
Level 3 IAM roles and the associated certifications apply to the highest-level management positions in information security.
Information Assurance System Architecture and Engineer (IASAE)
The U.S. DoD IASAE outlines Information Assurance architecture and engineering requirements for IA System Architects and Engineers, as per DoD 8570.01-M. This manual defines certification paths for Information Assurance (IA) professionals, necessitating personnel to attain and uphold certifications within their specific track for 8570 compliance. IA architects and engineers play a vital role in designing and securing information systems architectures. Their responsibilities include implementing measures such as firewalls, VPNs, antivirus software, IDS/IPS, border gateways, switches, routers, etc. Job titles for IASAE professionals encompass IT systems engineer, network engineer, cybersecurity architect, and others.
IASAE Level 1 usually is entry-level. It requires professionals to apply their knowledge of IA procedures, policy, and structure to design, develop, and implement computing environment systems, components, or architectures. Jobs at this level include entry-level positions in roles such as data architects, systems engineers, and IT systems engineers. Some of the roles of a Level I IASAE professional include:
- Designing and developing information assurance security requirements that need to be included in procurement documents.
- Identifying, assessing, and recommending information assurance or IA-enabled to be used in a computing environment and ensuring the recommended items/products are compliant with DoD validation and/or evaluation requirements.
- Developing and implement information assurance countermeasures for the computing environment.
- Identifying the specific information protection requirements for the CE network(s) and system(s).
- Ensuring that a system design(s) supports the incorporation of DoD-directed information assurance vulnerability solutions.
- Ensuring that software, OS, and hardware designs address IA security requirements for the computing environment.
- Developing IA architectures and designs for the SCI processing systems operating on protection Levels I or II.
- Designing and developing IA or IA-enabled products to be used in a computing environment
- Designing, developing, and implementing security designs for existing or new computing environment system(s).
Personnel with at least 5 years of IASAE experience fall under IASAE Level II. IASAE Level II professionals can be information system security engineers, cybersecurity architects, or data architects. These roles include developing, designing, implementing, and/or integrating DoD IA architecture, systems, or components for use in a NE. In furtherance of DoD 8670 compliance, these IASAE Level II professionals are expected to among other things:
- Identify the Network Environment’s information protection needs.
- Ensure that network environment information assurance policies are implemented in system architectures.
- Assessing vulnerabilities and threats to a network environment.
- Designing and developing IA or IA-enabled products to be used in a network environment.
- Developing methodologies to mitigate network environment vulnerabilities and recommending changes to the network or its system components where required.
- Ensuring a proper implementation of security designs to mitigate identified threats.
- Design, develop, and implement specific IA countermeasures for the network environment.
- Develop IA architectures and designs for DoD IS with basic integrity and availability requirements, including MAC III systems, systems with a Basic Concern for availability or integrity, and other DAA-designated systems.
IASAE Level III focuses on professionals with a minimum of 10 years of IASAE experience. Professionals holding IASAE Level III are responsible for designing, developing, implementing, and/or integrating a DoD IA architecture, system, or system component for use within NE, CE, and enclave environments. They ensure that the DoD information systems design and architecture are secure and functional. Table C10.T7 of DoD 8570.01-M specifies the functions of an IASAE Level III professional, including, but not limited to:
- Identifying information protection needs for the enclave environment.
- Ensuring the implementation of enclave IA policies into system architectures.
- Ensuring the implementation of subordinate CE and NE IA policies are integrated into the enclave system architecture.
- Developing IA architectures and designs for systems and networks with multilevel security requirements or requirements for the processing of multiple classification levels of data.
- Ensuring that acquired or developed system(s) and network(s) employ Information Systems Security Engineering and are consistent with DoD Component level IA architecture.
- Assessing the effectiveness of information protection measures utilized by the enclave.
- Designing and developing IA or IA-enabled products for use within the enclave.
- Ensuring that the implementation of security designs properly mitigate identified threats.
- Implementing and/or integrating security measures for use in the enclave and ensure that enclave designs incorporate security configuration guidelines.
- Overseeing and providing technical guidance to IASAE Level I and II personnel.
IASAE level III applies to the highest-level positions in the field. These include jobs like senior systems engineer, information assurance systems engineer, CTO, and system and network designer.
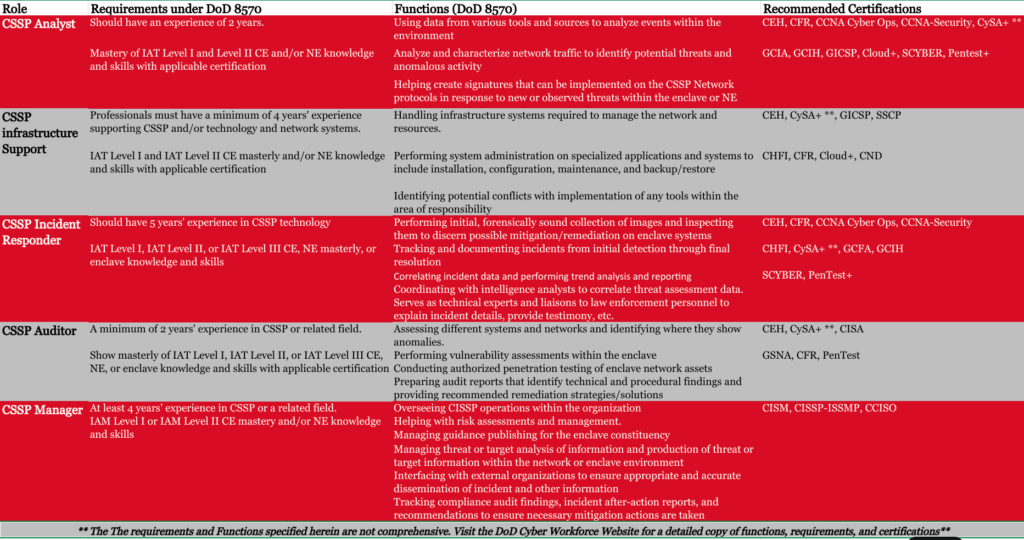
Cyber Security Service Provider (CSSP)
In 8570 compliance, the Cyber Security Service Provider (CSSP) certifications are crucial. Similar to other 8570 certifications, CSSP certifications are role-specific, involving training and third-party certification. The CSSP category includes five distinct roles: Analyst, Infrastructure Support, Incident Responder, Auditor, and Manager. Each role has specific requirements, detailed in the table below, outlining the diverse skills and expertise necessary for individuals to achieve and maintain DoD CSSP certification
The Significance of 8570 Compliance
DoD 8570, despite being officially succeeded by DoD 8140, remains crucial for cybersecurity, playing a key role in securing national interests. It enhances interoperability by standardizing training, fostering collaboration across DoD entities. Addressing IA architecture vulnerabilities, it unifies diverse systems under a comprehensive code of practice, creating a resilient structure. Trained personnel respond effectively to cyberattacks, safeguarding critical infrastructure. 8570 facilitates efficient third-party partnerships, crucial in the dynamic defense landscape, and strengthens international cooperation. Emphasizing continuous learning, it future-proofs defense by keeping the workforce abreast of evolving threats, ensuring national security resilience amidst constant change.
Benefits to Individuals
Embracing 8570 benefits individuals seeking advancement and skill development within the cybersecurity field. The directive encompasses all personnel involved in IA tasks, military and civilian alike. Its structured development process offers a clear path for individuals to acquire necessary training and certifications, streamlining compliance and ensuring everyone possesses the required skills and knowledge.
- Career Advancement: Pursuing 8170 compliant certifications equips individuals with valuable knowledge and skills, boosting their marketability and opening doors to coveted opportunities in the cybersecurity sector.
- Increased Credibility: Recognized certifications serve as industry-recognized benchmarks for competence, instilling trust and confidence in clients and employers alike.
- Enhanced Problem-Solving Skills: The training process hones analytical and critical thinking skills, enabling individuals to tackle complex cybersecurity challenges effectively.
- Lifelong Learning: The emphasis on continuous learning fosters a culture of professional development, ensuring individuals stay relevant and adaptable throughout their careers.
Benefits to Organizations
8570 compliance extends beyond regulatory obligation, providing tangible benefits for contractors handling sensitive information. By implementing 8570, organizations can benefit through:
- Enhanced Data Security: Implementing 8570 principles establishes a strong foundation for information security, minimizing the risk of data breaches and protecting valuable assets.
- Boosted Competitive Advantage: Demonstrating commitment to robust cybersecurity through adherence to 8570 standards attracts clients and partners, enhancing brand reputation and trust.
- Reduced Financial Risks: Proactive cybersecurity measures minimize the potential for financial losses associated with data breaches, reputational damage, and regulatory fines.
- Improved Operational Efficiency: Streamlined information sharing and standardized processes fostered by 8570 training enhance operational efficiency within organizations.
- Laying groundwork for efficient third-party partnerships: Defense is a multi-layered and dynamic concept. Modern defense technologies require partnering with third-party organizations because of factors like resource distribution and budget constraints. DoD 8570 plays a critical role in supporting the partnerships on a continuous basis. Through providing a transparent, complete set of IA requirements, 8570 leaves no room for ambiguity. Therefore, third parties can integrate their services with those internal to DoD.
The legacy of 8570 transcends its regulatory function. It serves as a blueprint for building a secure digital future, empowering individuals, fortifying organizations, and ultimately safeguarding national interests. By embracing its principles, we can collectively build a more resilient cyberspace where data, individuals, and nations are protected from evolving threats.
Requirements for 8570 Compliance
Navigating the specific requirements of 8570 compliance is essential for anyone involved with the Department of Defense’s information systems. Below is a breakdown of the key elements that individuals and organizations must understand and implement to meet these standards.
Certification Requirements for Various Roles
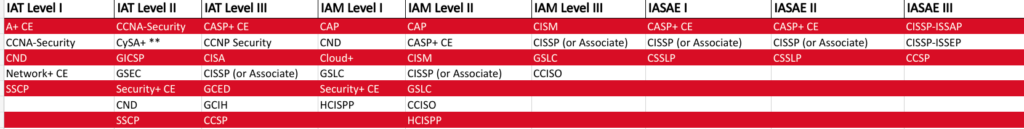
DoD 8570 meticulously outlines certification requirements tailored to distinct roles crucial for the effective functioning of the Department of Defense’s information systems. The directive categorizes these roles into 4 main categories: IAT, IAM, IASAE, and CSSP. Each level corresponds to specific responsibilities and skill sets, and DoD 8570 mandates corresponding certifications to ensure that individuals in these roles possess the requisite expertise. For instance, professionals in technical roles might be required to attain certifications like CompTIA Security+, demonstrating proficiency in implementing and managing security measures for information systems. On the managerial side, certifications such as Certified Information Systems Security Professional (CISSP) might be necessary, emphasizing leadership capabilities in information assurance. Each category, level and function of the cybersecurity roles has a list of approved baseline certifications that validate the required skills and knowledge. The certifications are from various vendors and organizations, such as CompTIA, Cisco, ISC2, EC-Council, ISACA, etc.
In addition to role-based certifications, DoD 8570 recognizes specific certifications that meet compliance standards. Certifications like CompTIA Security+, Certified Ethical Hacker (CEH), and CISSP are explicitly acknowledged as fulfilling the directive’s requirements. This recognition serves as a crucial guide for individuals and organizations, directing their focus towards certifications that the DoD explicitly accepts. By aligning with these recognized certifications, professionals ensure that their skills and knowledge are not only comprehensive but also in line with the specific cybersecurity needs of the Department of Defense. This strategic approach ensures the workforce is well-prepared to tackle evolving threats and maintain the security integrity of the DoD’s information systems. You can find the complete list of approved certifications on the DoD Cyber Exchange website.
Achieving and Maintaining Certifications
Paths to Certification
Achieving and maintaining DoD 8570 certifications is the first step in achieving compliance with the directive. However, you must understand which certifications are 8570 compliant. Fortunately, the DoD Cyber Exchange website lists all the Approved 8570 Baseline Certifications you can take if you are part of the IA workforce. To obtain a certification:
Identify Your Position
DoD 8570 certifications are role-specific. Thus, ensure you know your position’s IA roles before enrolling for one. You can know your role, level, and certification requirements by contacting your Information Assurance Manager (IAM) and following your component procedures.
Enroll in a Certification Program
You can register for a training program through your current employer or independently. Employers support career training with benefits, especially if certification and training are within the same industry. DoD 8570 certifications do not require completing lower levels before enrolling for higher ones. Therefore, you can directly register for the specialization or certification level that matches your career goals with enough work experience. A list of IA workforce certification providers can be found here.
Train for the Certification
Taking a training course helps you prepare for the certification exam. However, 8570 doesn’t recommend a particular training organization. Therefore, you can obtain training toward an 8570-information assurance baseline certification from any vendor. You can also use online resources, take supplemental courses, or attend workshops. While DoD 8570 doesn’t require training before you sit for the certification, you must follow your organization’s established procedures to request or get training.
Request for a Certification Exam Voucher
This is for those who registered through their IAMs. They should request that their information assurance managers provide them with an exam voucher in readiness to register for the certification exam. However, register for the certification exam early as it could be available only on certain days of the year. Some people register far in advance and prepare before the scheduled date of the exam arrives.
Pass the Certification Exam
When you’ve sufficiently prepared, then it’s time to schedule a certification exam. However, you should review all the relevant materials, practice some sample questions, and understand the exam format. Be focused, wisely manage your time, and answer all the questions to the best of your ability on the exam day.
Notify the IA Manager
Upon completing the certification, brief your component’s IA workforce personnel point of contact on your certification status. This ensures your certification is documented appropriately to show information assurance workforce compliance.
Maintaining Certification Status
To maintain your DoD 8570 compliance, you must ensure your certification status remains active. One of the best ways is through continuous learning. It not only helps you meet security standards but also equips you to adapt to emerging threats. Stay up-to-date with developments in the industry and attend relevant workshops, webinars, and training sessions. Remember, 8570 certifications usually have expiration periods, which typically are from 3-5 years. Hence, you want to be up-to-date with developments in the industry by the time of your next recertification or renewal. Some certifications require you to earn Continuing Professional Education (CPE) credits to maintain your certification. These can be made through professional activities like attending industry events, publishing articles, or taking relevant courses. As your certification nears its expiration date, plan for recertification. This might involve taking an exam or completing several continuing education units (CEUs). Be sure to check the specific recertification requirements for your certification.
Organizational Compliance Strategies
Organizations wishing to become 8570 compliant must strategically develop comprehensive plans to ensure collective conformity. Such plans involve meticulously considering various factors to create a robust framework.
Developing a Compliance Plan
The process begins by identifying specific compliance requirements, understanding the organization’s unique needs, and delineating responsibilities. In creating an excellent compliance plan, your organization should:
- Assess Requirements: Understand specific DoD 8570 compliance requirements relevant to roles within the organization.
- Identify Roles and Responsibilities: Clearly delineate compliance responsibilities, ensuring each team member understands their role.
- Training Initiatives: Implement regular and targeted training programs tailored to the requirements of DoD 8570.
- Certification Tracking: Establish a system to track and monitor certification statuses for all team members.
- Automate Compliance Tracking: Utilize automated tools to streamline compliance tracking, reducing manual efforts and minimizing errors.
- Continuous Learning Support: Subsidize training costs and exam fees to motivate continuous learning and certification renewal.
- Communication Strategy: Develop a clear and consistent communication strategy to inform and remind team members about compliance expectations.
- Recognition and Rewards: Implement a recognition program for individuals or teams maintaining DoD 8570 compliance, fostering a culture of achievement.
- Integration into Onboarding: Incorporate DoD 8570 requirements into the onboarding process, ensuring new hires are aware and compliant.
- Policy Reviews: Regularly review and update compliance policies to align with any changes in DoD 8570 standards or organizational needs.
A comprehensive plan that includes all the above ensures an effective DoD 8570 compliance across the organization.
Integrating Compliance into Organizational Culture
Effective communication and messaging are crucial to making 8570 compliance seem like a natural part of operations rather than an imposition. Leadership should regularly reference compliance in emails, meetings, and company newsletters. Tie 8570 policies to larger organizational values around ethics and integrity. Feature employees who maintain certifications as model team members. Make compliance topics engaging with real-world examples and opportunities for discussion during training. Offer frequent refreshers and lunch-and-learns to keep requirements top of mind. Provide study aids and practice tests to facilitate continuous learning.
Automating reminders about upcoming renewals and flagging any lapses through HR systems reduces mistakes. The process should be streamlined so employees can quickly register for training courses and exams. Cover the costs of certification to remove financial barriers. Compliance should be part of new hire onboarding processes and included in performance reviews. Implement rewards and recognition programs for teams and individuals who sustain 8570 standards to reinforce achievements. Maintain an up-to-date knowledge base on the intranet with compliance resources. Regularly review and optimize policies and procedures to simplify meeting requirements. With the proper support systems and culture of learning in place, 8570 can be a seamless aspect of daily work.
8570 compliance requires a proactive approach to cybersecurity certification. It’s not just about meeting a standard but about fostering an environment where continuous learning and adherence to cybersecurity best practices are integral to your team’s ethos. Understanding these requirements is the first step in building a robust defense against the evolving threats in the digital world.
Steps to Achieve 8570 Compliance for Your Team
Ensuring your team meets the 8570 compliance standards is a vital part of maintaining cybersecurity readiness, especially when working with the Department of Defense. Below is an outline of the practical steps that can guide your team towards achieving and sustaining this crucial compliance.
Assessing Current Compliance Status
Before you can plan and implement any actions to achieve 8570 compliance, you must clearly understand your team’s qualifications and certifications. This will help you identify the gaps and prioritize the areas that need improvement. Conducting an initial assessment is the first step to determine the current compliance status of your team. It involves mapping the roles and functions of your team members to the corresponding 8570 categories and levels and verifying their existing qualifications and certifications against the 8570 requirements. This will help you establish a baseline for your team’s compliance and identify your team’s strengths and weaknesses.
After conducting the initial assessment, the next step is to find out where your team members fall short of the 8570 requirements. During gap identification, you must also determine how much effort is needed to close those gaps. It involves analyzing the initial assessment results and prioritizing the gaps based on the urgency, impact, and feasibility of addressing them. To identify gaps, you can use techniques such as:
- Using a risk assessment to assess the likelihood and consequences of non-compliance and determine the level of risk associated with each gap.
- Using a gap analysis matrix to compare the current and desired states of your team’s compliance and quantify the gaps in terms of numbers, percentages, and costs.
- Using a SWOT analysis to evaluate your team’s compliance’s strengths, weaknesses, opportunities, and threats and identify the internal and external factors that affect it.
Training and Certifying Team Members
Once you have identified and prioritized the gaps, you need to close them out. Gaps in 8570 compliance are primarily in terms of an unqualified workforce. Thus, you must plan and execute the actions to train and certify your team members. This will help you ensure your team members have the necessary knowledge and skills to perform their roles and meet the 8570 requirements. To achieve this, begin by selecting appropriate training programs. This involves finding and choosing the best training courses that match your team members’ learning objectives and outcomes of the required certifications. Research and compare the available training options, then evaluate them based on the quality, relevance, cost, and convenience of the training.
When choosing the appropriate training programs, consider factors like the accreditation and reputation of the training provider and the certification body. The training curriculum should also align and cover the certification exam objectives. Additionally, you must consider the delivery and format of the training. Is it self-paced, online, instructor-led, or classroom-based? How long will the training take? Other things to consider include cost and availability of the training. After you select the optimal training program, facilitate certification by offering financial support, forming study groups, allocating study resources, and providing motivation. Create a certification plan outlining steps, resources, and timelines for achieving goals. This entails supporting team members with reimbursement, sponsorship, study groups, time allocation, and motivation through recognition or incentives.
Integrating Compliance into Hiring and Onboarding
Achieving 8570 compliance is not a one-time event but a continuous process that requires constant monitoring and maintenance. Therefore, you need to integrate compliance into your hiring and onboarding processes to ensure that your team always complies with current and future standards. To achieve this, you should hire with compliance in mind. This involves designing and implementing a recruitment strategy that emphasizes the importance and benefits of 8570 compliance and screens the candidates based on their qualifications and certifications. Some strategies for hiring with compliance in mind are:
- Including the 8570 requirements in the job descriptions and advertisements for the positions you are hiring for
- Using the DCWF to define the roles and responsibilities of the positions and verify the qualifications and certifications of the candidates
- Conducting technical interviews and assessments to test the candidates’ knowledge and skills in the relevant 8570 domains
- Offering competitive compensation and benefits packages that reflect the value and demand of the 8570 certifications
Your organization should orient and integrate new hires into your team and ensure they know and align with the 8570 compliance expectations and goals. It involves providing the necessary information and resources to achieve and maintain their certification status and monitor their progress and performance. To onboard for success:
- Provide an orientation on the 8570 policy and its purpose, scope, and benefits.
- Explain the 8570 requirements and expectations for their role and function.
- Provide them with the resources and support to achieve their certification goals, such as training programs, study materials, exam vouchers, etc.
- Assign them a mentor or a buddy to guide and assist them throughout the certification process.
- Track and review their certification progress and performance and provide feedback and recognition
Creating a Culture of Continuous Learning
Since achieving 8570 compliance is a dynamic and evolving process, it requires constant adaptation and improvement. Therefore, you need to create a culture of continuous learning among your team members to ensure they are always up to date and ahead of the curve in the cybersecurity field. You can do this by staying updated with compliance changes and promoting ongoing education. To facilitate ongoing education, foster a learning mindset and environment among your team members and provide them with opportunities and resources to enhance their knowledge and skills and renew their certifications. To achieve this, your organization must create and implement a learning and development plan that aligns with the 8570 requirements and the team’s goals and needs. Additionally, ensure your team is constantly updated on cybersecurity and compliance changes. You can achieve this by enrolling them into newsletters and podcasts and periodically financing their attendance to conferences and events geared towards 8570 compliance.
Achieving 8570 compliance is a dynamic and ongoing process that requires commitment and strategic planning. By following these steps, you can ensure your team is not only compliant with current standards but also prepared for any future changes in the cybersecurity landscape.
Maintaining 8570 Compliance
Achieving 8570 compliance is a significant milestone, but maintaining it is an ongoing journey. So, what are the strategies and best practices to ensure long-term adherence to these critical cybersecurity standards?
Continuous Education and Recertification
The best way to maintain 8570 compliance is through continuous education, which may involve attending training courses, workshops, conferences, and participating in knowledge-sharing initiatives. It helps you stay ahead of cyber threats, which are constantly evolving. Since vulnerabilities and attack vectors emerge daily, continuous education enables you to know how to manage and mitigate against them. By continuously learning, you can get the latest knowledge and skills to identify, understand, and defend against these evolving threats. Different 8570-approved certifications have varying recertification intervals, typically three to five years. You must adhere to the recertification deadlines and provide the required documents to support your recertification.
Adapting to Changes in Compliance Requirements
To maintain active 8570 compliance in your organization, you must adapt to the changes in compliance requirements. To achieve this, ensure your organization has a designated point of contact (PoC) responsible for following up on changes and updates to the 8570 Directive and related compliance standards. The PoC may use official DoD channels, industry publications, and professional networks to gather information promptly. Whenever changes arise, they must be implemented efficiently and swiftly. Thus, your organization also needs to establish a communication plan and workflow for disseminating information about new requirements. The PoC should then conduct awareness sessions, update internal policies and procedures, and provide practical guidance on implementing the changes with minimal disruption.
Internal Audits and Assessments
Continuous education and adapting to changes are not enough. Your organization must regularly conduct internal audits and assessments to identify gaps in 8570 compliance. However, the audits must be tailored to specific roles within the IA workforce. After identifying any gaps, corrective actions and improvements should be taken swiftly. If any gaps need to be reported under the law, you should notify the relevant authorities. Additionally, your organization should develop a straightforward process for addressing any compliance issues identified during these audits. Any corrective actions must be implemented promptly and effectively, documenting the steps taken and ensuring lessons learned are incorporated into future practices.
Fostering a Culture of Security Awareness
Finally, any organization working with DoD must foster a culture of cybersecurity awareness. It must integrate cybersecurity into its core values and mission. Such an organization must emphasize the shared responsibility for safeguarding sensitive information and assets, making security awareness a fundamental aspect of every role. It should also champion top-down communication of this message. Such a culture can only be fostered through engaging and educating the IA workforce. However, the organization should go above and beyond traditional methods. It should use innovative approaches to ensure its employees engage in cybersecurity best practices and compliance. These methods include using gamified learning modules, interactive workshops, internal awareness campaigns, and simulated phishing exercises to create a dynamic and engaging learning environment. Individuals who demonstrate exemplary security awareness and behavior should be recognized and awarded.
Maintaining 8570 compliance is as crucial as achieving it. It’s a commitment to excellence in cybersecurity, requiring continuous vigilance and adaptation. However, this is not a one-time effort but a constant commitment. By implementing these strategies and best practices, you can create a culture of security awareness, keep your personnel qualified and updated, and adapt to evolving threats and regulations, ensuring long-term adherence to these critical cybersecurity standards.
Overcoming Challenges in 8570 Compliance
While achieving and maintaining 8570 compliance is essential, it’s often accompanied by various challenges. This section explores common obstacles and provides practical solutions to overcome them, ensuring successful compliance.
Identifying Common Challenges
Many organizations face the challenge of limited budgets, personnel, and other resources. The scarcity of skilled professionals, high competition for talent, and the cost of acquiring and retaining are some of the challenges organizations face when recruiting personnel with the required 8570-compliant qualifications. Since entities working on DoD contracts must achieve 8570 compliance, they must develop inventive ways of addressing personnel and resource challenges. For instance, they can prioritize the most critical roles for 8570 compliances first, then gradually expand their efforts as resources allow. They can also leverage free online resources and seek government grants to address the deficiencies in finances. To address personnel limitations, your organization can cross-train existing staff, hire part-time consultants, and use managed security service providers (MSSPs). Alternatively, they can offer competitive salaries and benefits or promote career development opportunities.
Developing Effective Solutions
Many organizations face a challenge in developing effective solutions. To address this, they should partner with universities and training providers to help alleviate financial and logistical burdens. This accords benefits such as access to expert instructors, shared costs, and customized training programs. However, these entities must choose reputable partners, ensure alignment with compliance requirements, and negotiate clear terms and conditions. Another option is to use government resources. Numerous resources are provided by the government and industry bodies to support 8570 compliance efforts. These include online training materials, certification guides, and advice and best practices forums. Such resources include NIST guidance, CISA programs, and industry best practices documents. Thus, entities can access free or low-cost resources, up-to-date information, and proven compliance strategies.
Streamlining the Certification Process
Many IA employees go through various hurdles to attain 8570 compliant certifications. Organizations can make the certification process more accessible to the IA workforce by providing clear, step-by-step guides and offering support. They can offer on-site or online training options, provide study materials and practice tests, and recognize and reward successful completion. Unfortunately, this also has issues, such as time constraints, employee resistance, and lack of motivation. They should also help employees manage their work responsibilities while pursuing necessary certifications. Organizations can offer flexible training schedules, provide study leave programs, or reimburse certification costs.
Building Resilience Against Compliance Challenges
Foster a supportive culture that encourages continuous learning and growth in your organization. This could include recognizing and rewarding employees who gain new certifications or contribute significantly to your compliance efforts. Ensure you create a trusting environment where your employees are comfortable suggesting improvements and raising concerns. Adaptable approaches to compliance can help organizations navigate and overcome obstacles effectively. This could involve regularly reviewing and updating your compliance strategies to ensure they remain practical and relevant. Additionally, you must be prepared to adjust plans and processes based on changing regulations, threats, and technologies. You must prioritize resources based on identified vulnerabilities and the potential impact of security breaches.
Future of 8570 Compliance
As the landscape of cybersecurity evolves, so too will the standards and requirements for 8570 compliance. In this part, we diiscuss anticipated changes and trends in the realm of cybersecurity compliance, preparing organizations and individuals for what lies ahead.
Anticipated Changes in Compliance Standards
As cyber threats and technology evolve, we can expect updates to the 8570 Directive, including new certification requirements to address emerging threats. There may be a shift beyond technical controls towards threat intelligence, incident response, and risk management skills. Future certifications may align with Zero Trust principles, cloud security, IoT, and supply chain risks. The goal is to equip professionals with relevant skills to combat current and future threats. With a constantly changing cybersecurity landscape, compliance standards must adapt flexibly and rapidly. This requires organizations and individuals to update their knowledge and skills regularly. Compliance will likely become more flexible to enable quicker responses to new technologies and threats. Through updates to 8570 standards, professionals can stay on top of leading-edge skills to counter the latest cyber risks.
Emerging Cybersecurity Trends and Their Impact
Emerging threats, such as advanced persistent threats (APTs) and ransomware, could influence future compliance requirements. Such threats require better-trained personnel to address. Additionally, competently qualified personnel are required to develop detection and response tools. Additionally, the rise in IoT requires secure device management and communication protocols for interconnected devices. Artificial intelligence and Machine Learning are used in various areas, such as analytics, risk management and fraud detection. Unfortunately, AI can also power complicated cyberattacks against organizational information systems. Another emerging technology that has an impact on cybersecurity is quantum computing. For instance, it poses a threat to the current cryptographic tools and modules. Therefore, there is a need for an IA workforce that can handle threats emanating from emerging cybersecurity trends. This means that we might see a new requirement in 8570 compliances to include certifications aligning with these emergent cybersecurity trends.
Preparing for the Future of Cybersecurity Compliance
The dynamic nature of the technological landscape often leads to compliance challenges. Compliance requirements are regularly reviewed and updated to stay current with the cybersecurity landscape. So, how can you stay prepared for these changes? Here are some strategies:
- Collaboration and Information Sharing: Stay ahead of emerging threats by actively participating in industry forums and information sharing initiatives.
- Embracing Automation: Leverage automated tools for threat detection, vulnerability management, and incident response.
- Continuous Monitoring and Improvement: Cultivate a culture of continuous monitoring, threat hunting, and incident response simulations.
- Upskilling and Reskilling: Continuous learning is crucial with the constant evolution of the cybersecurity field. This could involve pursuing additional certifications, participating in training programs, or staying informed about the latest trends and threats.
Being proactive also entails anticipating changes in compliance requirements and taking necessary steps to meet them. By adopting these strategies, you can effectively navigate the ever-changing cybersecurity landscape.
The Broader Implications for National Security
DoD 8570 applies to the DoD IA workforce and its civilian supply chain. Therefore, compliance with the mandate has a profound impact on national security and national defense. By ensuring that cybersecurity professionals are well-equipped to protect against threats, organizations can protect critical infrastructure and sensitive data against cyber threats and state-sponsored espionage. To further protect essential information related to defense, there may be stricter compliance requirements in the future. Remember, effective compliance contributes to national cyber deterrence capabilities and incident response strategies.
Global cybersecurity trends will profoundly influence future DoD compliance standards. The increased adoption of cloud computing will necessitate cloud security certifications to ensure proper configuration, data protection, and incident response. The growth of IoT requires certifications focused on device provisioning, network segmentation, and vulnerability management at scale. Emerging technologies like AI, blockchain, and quantum computing introduce new risks and attack vectors that compliance must address through relevant certifications. Compromise to supply chain through third-party vendors and open-source libraries drives a need for vendor risk management and application security certifications.
The rise of sophisticated nation-state attacks and advanced persistent threats globally means a need for certifications in threat intelligence, digital forensics, and incident response. Expanding data privacy regulations worldwide necessitate certifications in legal/regulatory environments and data privacy. Overall, DoD compliance must continuously evolve as technology and threats advance globally, expanding recognized skills, focus areas, and certifications to match the shifting landscape.
The future of 8570 compliance is not set in stone, but one thing remains certain: the need for robust cybersecurity measures will only grow. By staying informed, adaptable, and committed to continuous improvement, organizations and individuals can not only anticipate these changes but also play a role in shaping the future of cybersecurity compliance.
Conclusion
As we wrap up our comprehensive exploration of 8570 compliance, it’s clear that this framework is more than a regulatory requirement – it’s a critical component in safeguarding our digital infrastructure and national security. The journey to achieving and maintaining 8570 compliance might be challenging, but it is undoubtedly rewarding, offering enhanced cybersecurity readiness and professional credibility. Organizations and individuals that embrace the principles of 8570 compliance not only contribute to their own security but also to the broader goal of national defense. As cybersecurity threats evolve, so too will the standards for compliance. Staying informed, adaptable, and committed to continuous learning are key to navigating this ever-changing landscape. Remember, 8570 compliance is not a one-time achievement but an ongoing commitment. By integrating these standards into the very fabric of your organizational culture and personal development, you position yourself and your team at the forefront of cybersecurity excellence.
As we look ahead, let’s carry the insights and strategies discussed in this article forward, championing a future where robust cybersecurity is a shared responsibility and a universal priority.
Additional Resources
For further information and updates on 8570 compliance and cybersecurity standards, you can refer to the following .gov resources:
- Cybersecurity Compliance Frameworks – cisa.gov
- National Initiative for Cybersecurity Careers and Studies – niccs.cisa.gov
- DoD Cyber Workforce – public.cyber.mil
Share in Social Media
See More Case Studies

Securing Defense Contracts: A DFARS 252.204-7012 Compliance Case Study
Discover how Cleared Systems helped a Federal Contractor successfully achieve DFARS 252.204-7012 compliance by strengthening its cybersecurity posture, giving it a competitive edge when bidding for DoD Contracts.

What is GCC High? For ITAR & CMMC 2.0
Microsoft 365 Government Community Cloud (GCC) High is a specialized cloud solution tailored for U.S. federal, state, local, tribal, and territorial government organizations, as well as for contractors who hold or process data subject to specific security regulations. In this article, we will explore the features, benefits, and differences between Microsoft 365 GCC High and other Office 365 offerings.

Is AutoCAD ITAR Compliant? A Comprehensive Guide for Defense Manufacturers
Defense contractors and manufacturers working with sensitive military technologies face a critical question when selecting computer-aided design software: Is AutoCAD ITAR compliant? This question becomes

How to Get Help in Windows: Guide to Security and Compliance Support
In today’s digital landscape, ensuring your computer systems are secure and compliant with industry regulations is essential for both businesses and individuals. Windows, as one

Microsoft Copilot for GCC High: Enhancing Security and Compliance
In today’s fast-evolving digital landscape, organizations that handle sensitive data, particularly those in government sectors or defense contractors, face growing pressure to maintain strict security
Partner with Us for Compliance & Protection
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Security
- Compliance
- Peace of mind
- Efficiency
- Trust
What happens next?
Schedule an initial meeting
Arrange a discovery and assessment call
Tailor a proposal and solution
